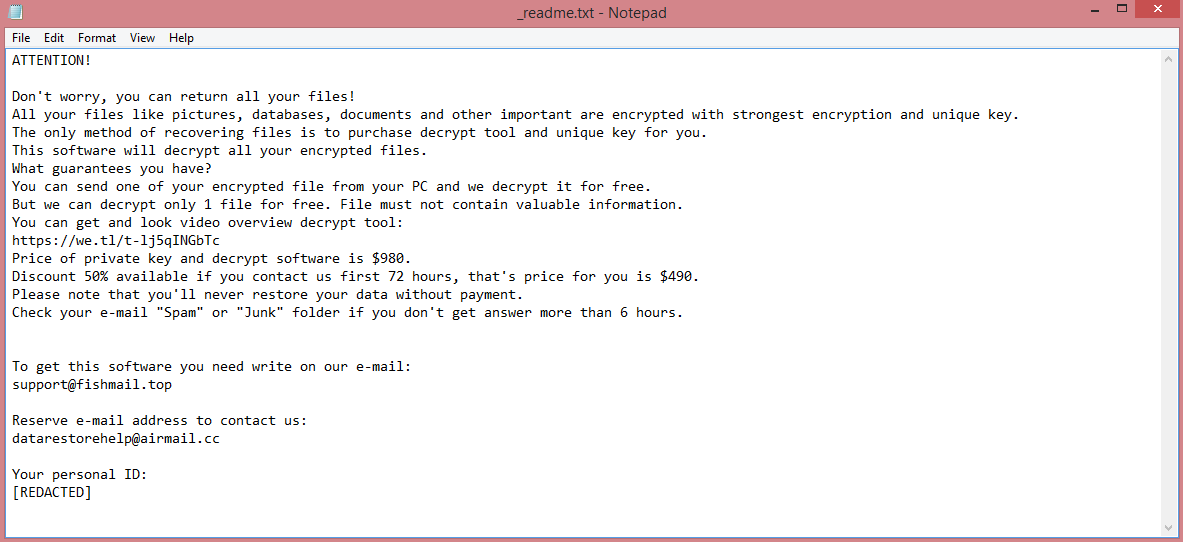
What is Kevin ransomware?
Kevin is a recently-discovered ransomware program. This term explains the primary aim of this virus: to extract money from its victims by the means of ransom. To accomplish this, Kevin ransomware performs a simple sequence of actions.
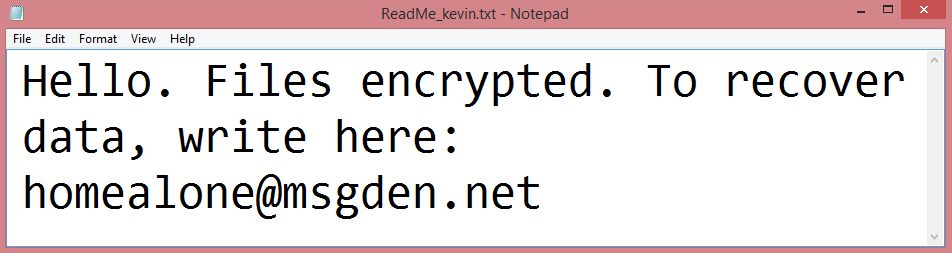
The first step is to encrypt the files. As such files cannot be accessed, they can be considered “stolen”. Then, it renames the encrypted files to highlight that an attack has taken place. To be more precise, the hacker’s e-mail address and .kevin file extension get added to the end of each filename.
Finally, the virus also creates a ransom note, named “ReadMe_kevin.txt”. This rather brief note can be read on the image above, and doesn’t really contain anything except the aforementioned e-mail address.
So, should you contact the criminal? Probably not. First, this will this encourage him to carry out future attacks; attacks that might target you again. Second, these people are neither trustworthy nor honorable. They’re criminals after all. Many of them stop replying after receiving, without bothering to decrypt the files at all.
For this reason, you should explore other ways to remove Kevin ransomware and decrypt .kevin files. Our guide aims to aid in this process of exploration.
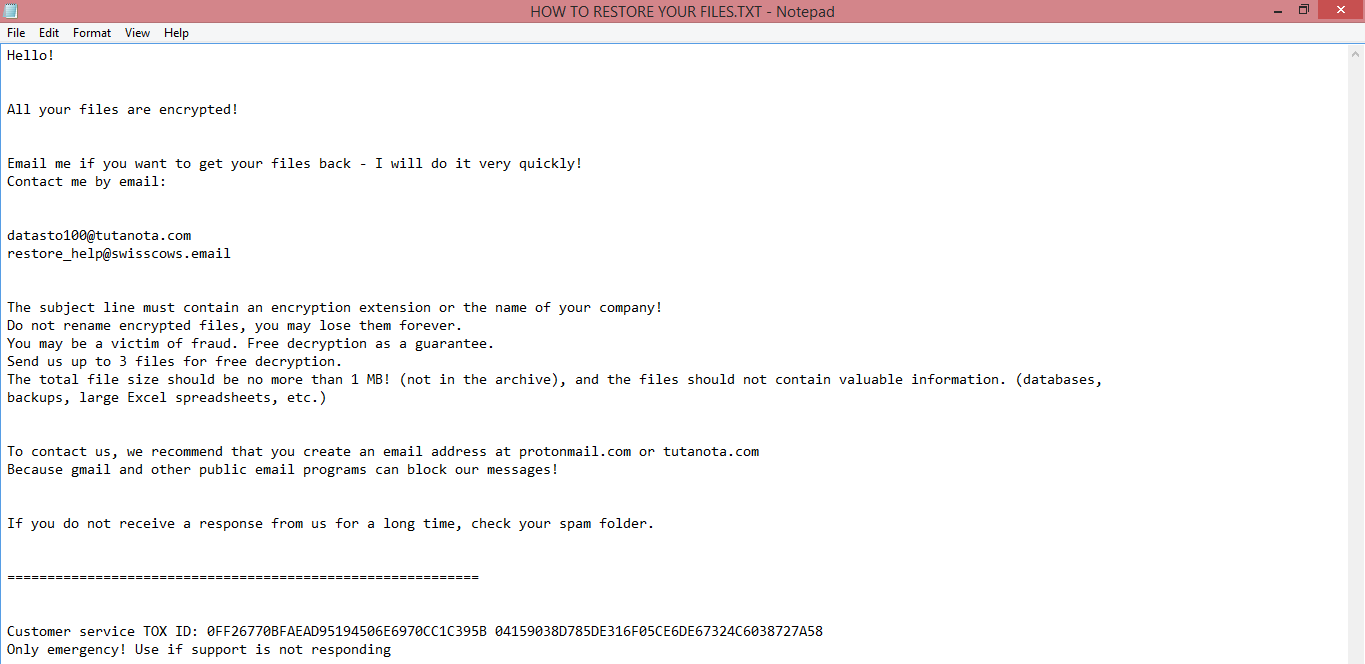
![RansomBoggs ransom note:
Dear human life form!
This is James P. Sullivan, an employee of Monsters, Inc.
Recently our company has again expecienced great financial problems and we require some cash to move on with our
electronic crap.
So we are relying on you in these hard times and are crying for help.
I am extremely sorry for the inconvenience but I am currently encrypting your documents using AES-128.
This key is encrypted using RSA public key and saved to aes.bin file:
[ C:\Users\[REDACTED]\Desktop\aes.bin ]
Please, DO NOT WORRY! I have a decrypting functionality too.
Just don't delete aes.bin, please. You will need it!
==================================================================================
You just need to contact me:
m0nsters-inc@proton.me
https://t.me/m0nsters_inc
TOX 76F64AF81368A06D514A98C129F56EF09950A 8C7DF19BB1B839C996436DCD36A6F27C4DF00A6
==================================================================================
This is the end of the note. Below you will find a guide explaining how to remove RansomBoggs ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-ransomboggs-ransomware.png)
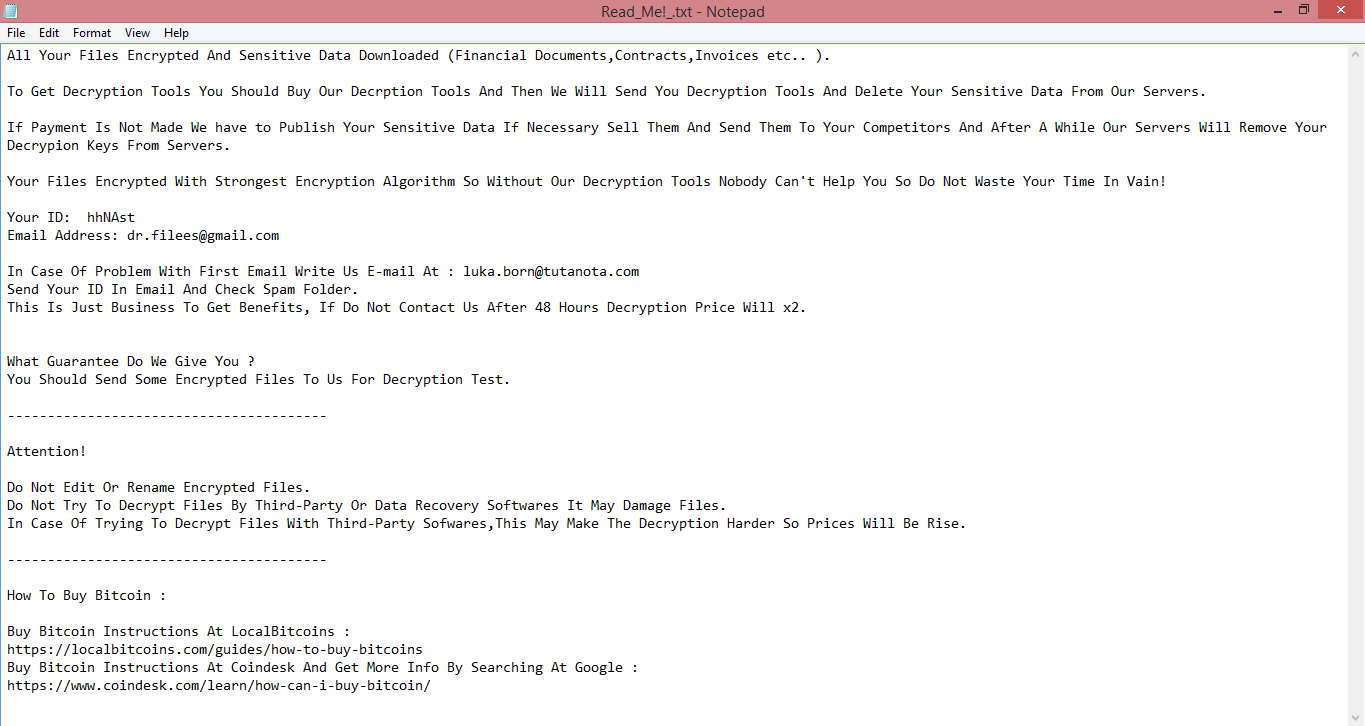
![Vohuk ransom note:
[~] Vohuk Ransomware V1.3
>>> What's happened?
ALL YOUR FILES ARE STOLEN AND ENCRYPTED.
To recovery your data and not to allow data leakage, it is possible only through purchase of a private key from us.
>>> What guarantees?
We are not a politically motivated group and we do not need anything other than your money.
Before paying you can send us up to 2 files for free decryption.
The total size of files must be less than 2MB(non archived).
files should not contain valuable information. (databases, backups, large excel sheets, etc.)
>>> CONTACT US:
Please write an email to both: payordiebaby@tutanota.com & payordiebaby69@msgsafe.io
Write this Unique-ID in the title of your message: [REDACTED]
>>> ATTENTION!
Do not delete or rename or modify encrypted files.
Do not try to decrypt using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price(they add their fee to our).
We use strong encryption, nobody can restore your files except us.
The price depends on how fast you contact with us.
remember to hurry up, as your email address may not be available for very long.
All your stolen data will be loaded into cybercriminal forums/blogs if you do not pay ransom.
If you do not pay the ransom we will attack your company repeatedly again.
This is the end of the note. Below you will find a guide explaining how to remove Vohuk ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-vohuk-ransomware.png)