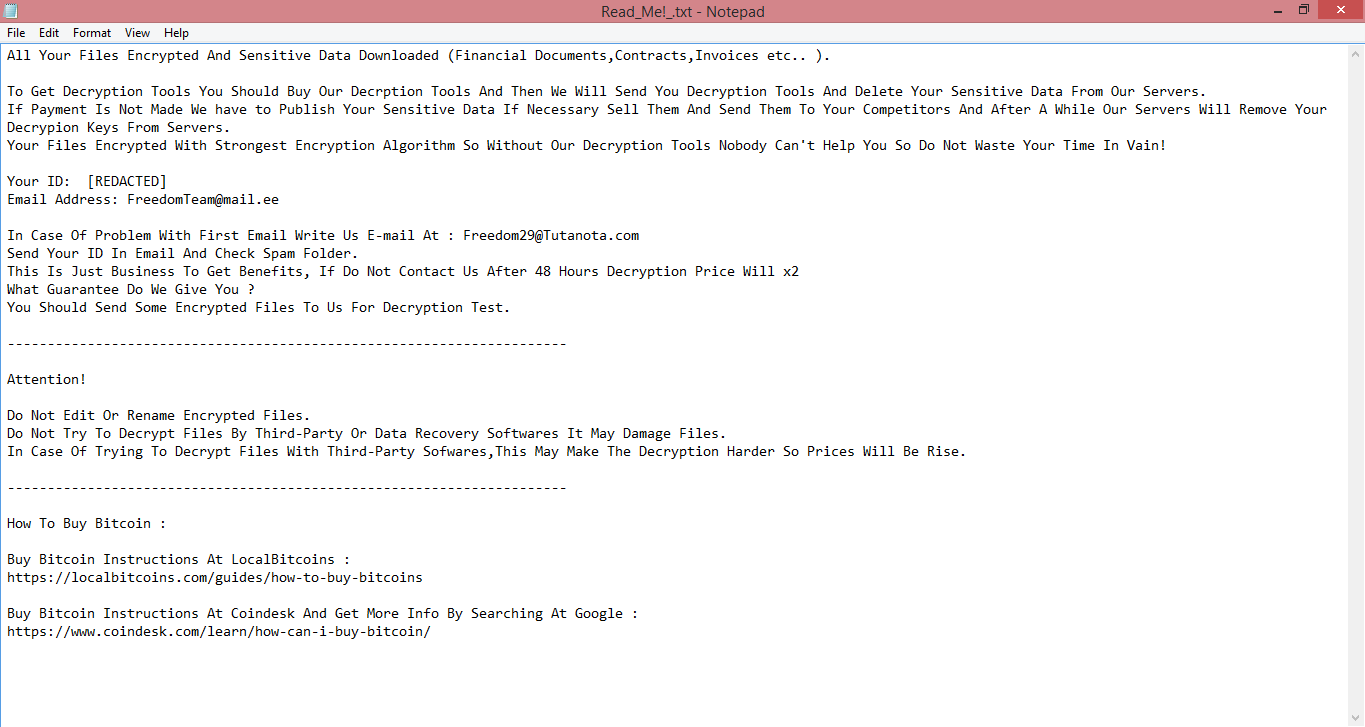
![Joker ransom note:
Your Files Are Has Been Locked
Your Files Has Been Encrypted with cryptography Algorithm
If You Need Your Files And They are Important to You, Dont be shy Send Me an Email
Send Test File + The Key File on Your System (File Exist in C:/ProgramData example : RSAKEY-SE-24r6t523 pr RSAKEY.KEY) to
Make Sure Your Files Can be Restored
Make an Agreement on Price with me and Pay
Get Decryption Tool + RSA Key AND Instruction For Decryption Process
Attention:
1- Do Not Rename or Modify The Files (You May loose That file)
2- Do Not Try To Use 3rd Party Apps or Recovery Tools ( if You want to do that make an copy from Files and try on them and
Waste Your time )
3-Do not Reinstall Operation System(Windows) You may loose the key File and Loose Your Files
4-Do Not Always Trust to Middle mans and negotiators (some of them are good but some of them agree on 4000usd for example and
Asked 10000usd From Client) this Was happened
Your Case ID :[REDACTED]
OUR Email :suppransomeware@tutanota.com
in Case of no answer: suppransomeware@mailfence.com
This is the end of the note. The following is a guide explaining how to remove Joker ransomware.](https://www.computips.org/wp-content/uploads/2022/09/how-to-remove-joker-ransomware.png)
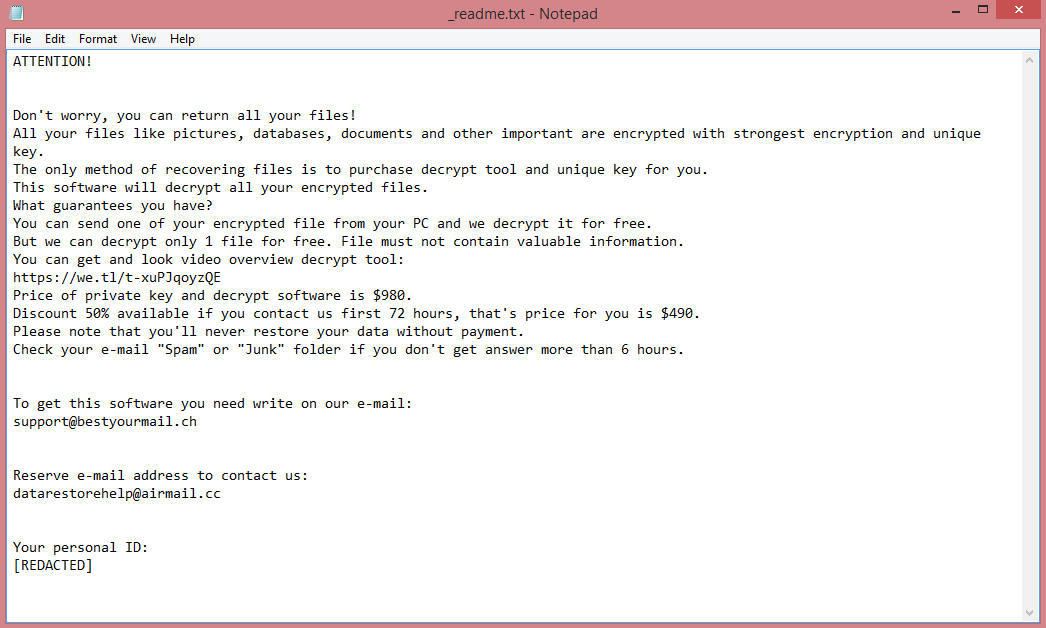
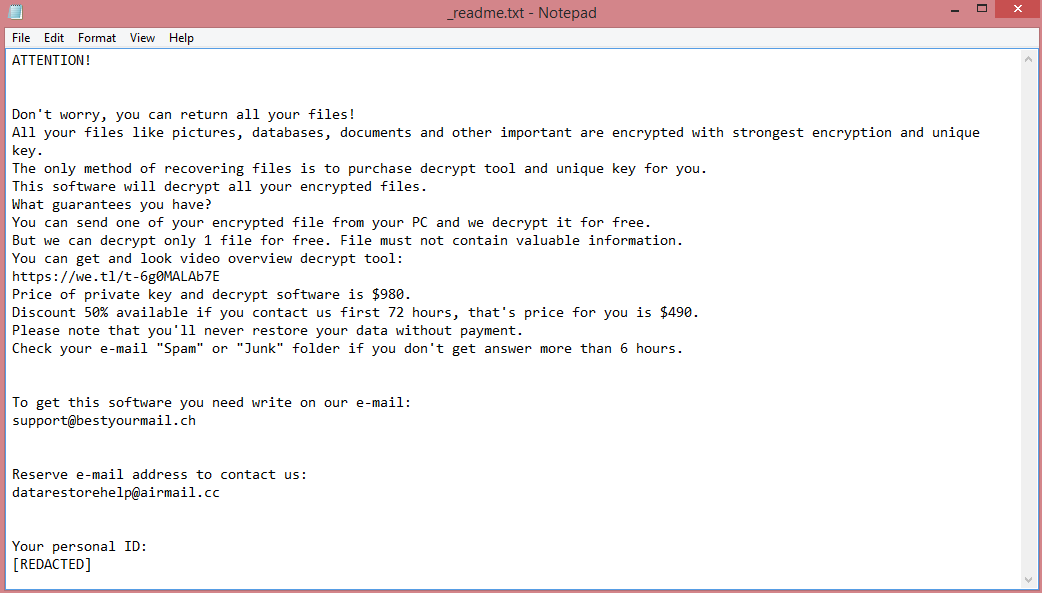
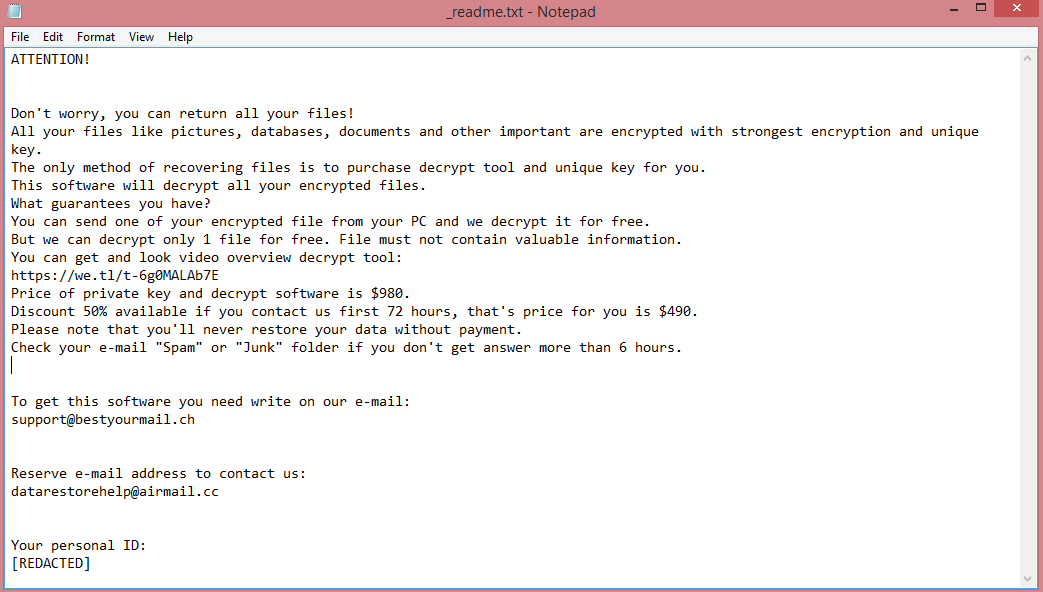
What is Joker ransomware?
Joker is an illegal program that makes money via data ransom (this is why it’s called ransomware). It infiltrates the victim’s computer and encrypts all files it can find using cryptographic algorithms. This renders the files inaccessible; to view and edit them again, they need to be decrypted. You can think of it as password-locking. Of course, the victim is not given the password; instead, the hackers say that the only way to decrypt the files is to pay them.
Joker specifically belongs to the VoidCrypt ransomware family. Files locked by this ransomware are given .Joker file extension, which is how the virus got its name to begin with. The virus also leaves two ransom notes, “Decryption-Guide.HTA” and “Decryption-Guide.txt”. They contain the same information, but the first one appears automatically, as a pop-up. You can read the full text on the image above, but here are the highlights.
The note does not mention any specific price; it merely asks the victim to contact the hacker to negotiate. It is also written in very poor English.
Giving into these demands is not recommended; often, the hackers simply take the money and disappear without giving the victims their files back. You can, however, remove Joker ransomware and decrypt .Joker files by following the guide below.
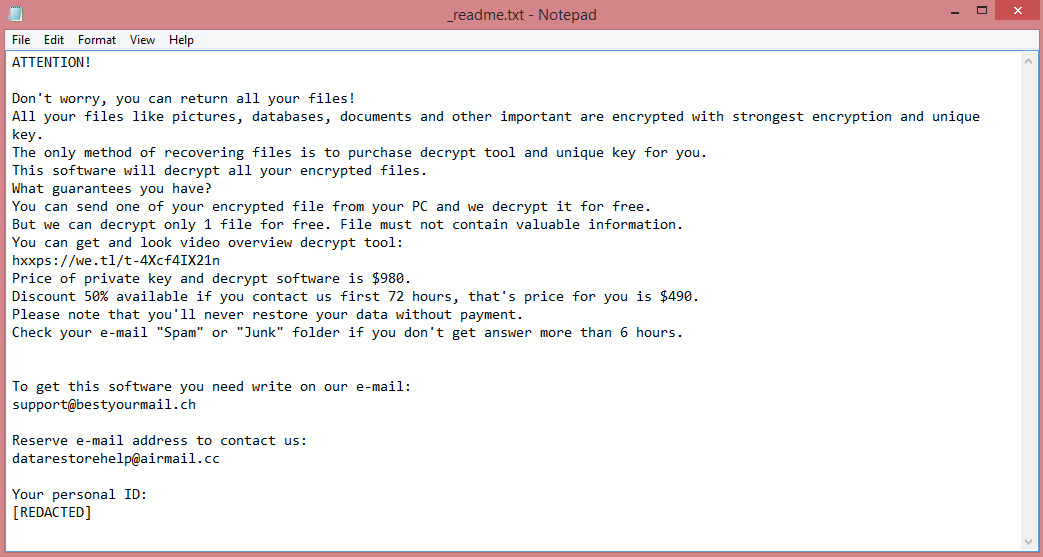
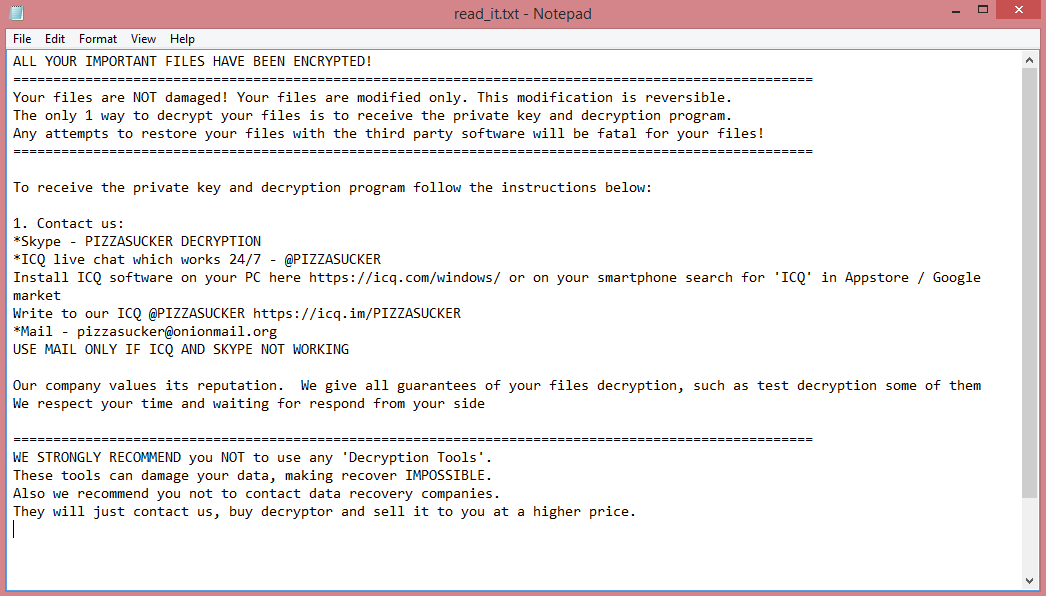
![Encfiles ransom note:
Your files are now encrypted!
Your personal identifier:
[REDACTED]
All your files have been encrypted
And all your backup and NAS system deleted military grade ERASE Methods.
Now you should send us email with your personal identifier.
This email will be as confirmation you are ready to pay for decryption key.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
If you want take back your files please contact us.
Email : dataprotection@tuta.io
Please send both email adress for contact us
Free decryption as guarantee!
Before paying you can send us up to 3 files for free decryption.
The total size of files must be less than 10Mb (non archived), and files should not contain
valuable information (databases, backups, large excel sheets, etc.).
How to obtain Bitcoins?
* The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click
'Buy bitcoins', and select the seller by payment method and price:
https://localbitcoins.com/buy_bitcoins
* Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins
Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price
(they add their fee to our) or you can become a victim of a scam.
This is the end of the note. Read the guide below to learn how to remove Encfiles ransomware.](https://www.computips.org/wp-content/uploads/2022/09/how-to-remove-encfiles-ransomware.png)