What is Vypt ransomware?
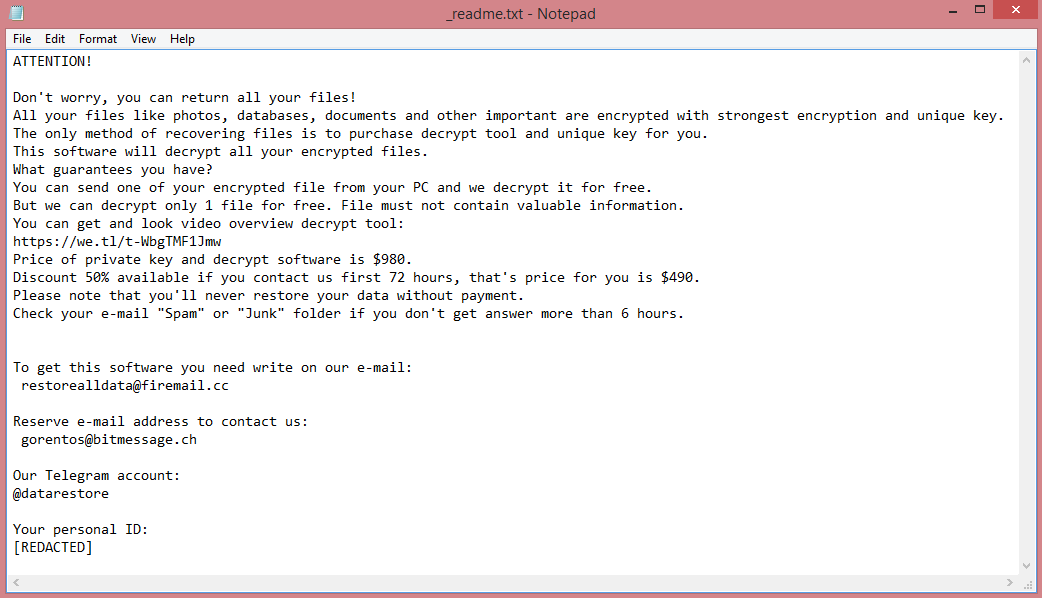
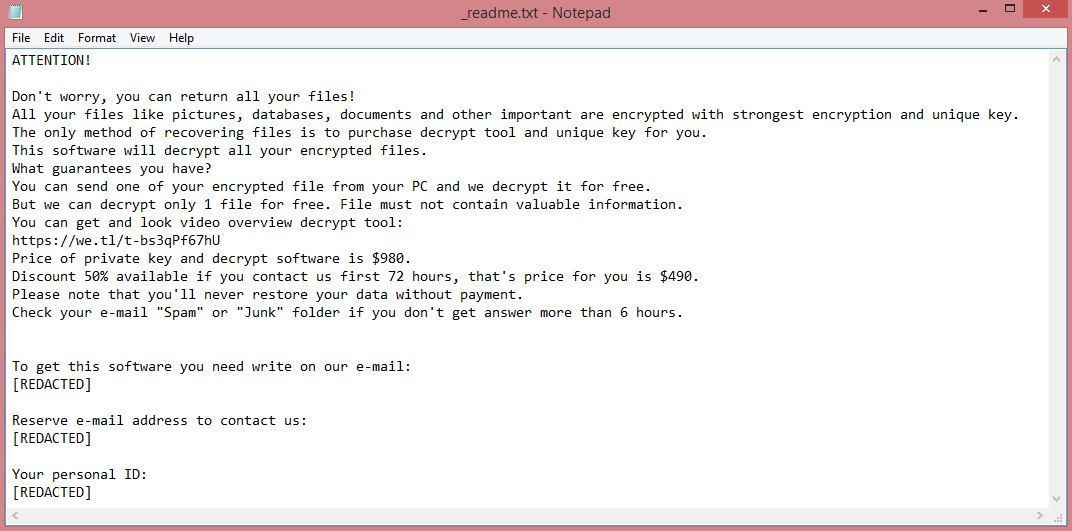
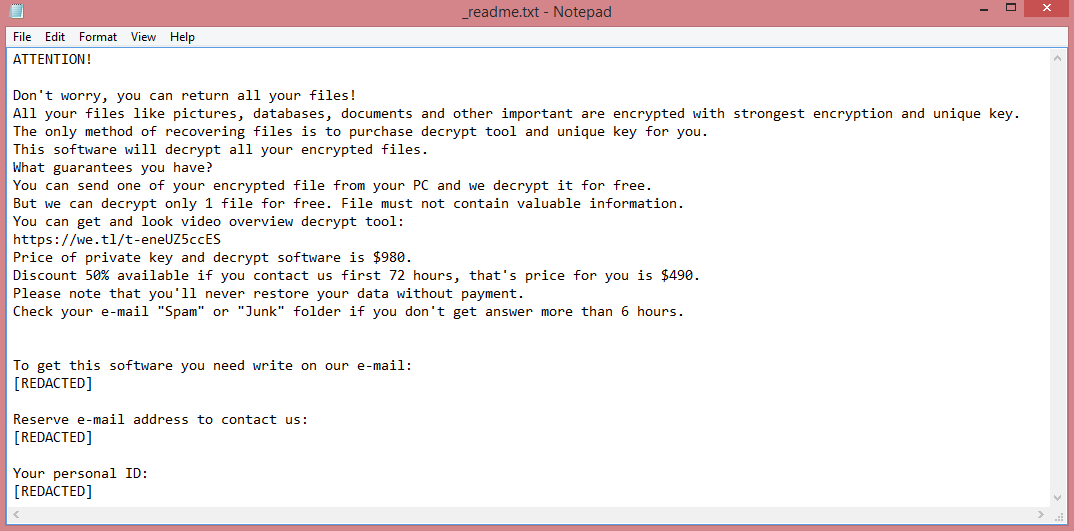
Vypt is one of the latest strains of STOP/Djvu, a ransomware virus. It encrypts your files (photos, videos, documents, etc.) with the intention of demanding ransom for them. It is very easy to tell that you’ve been infected by this virus, as it gives .vypt file extension to all encrypted files.
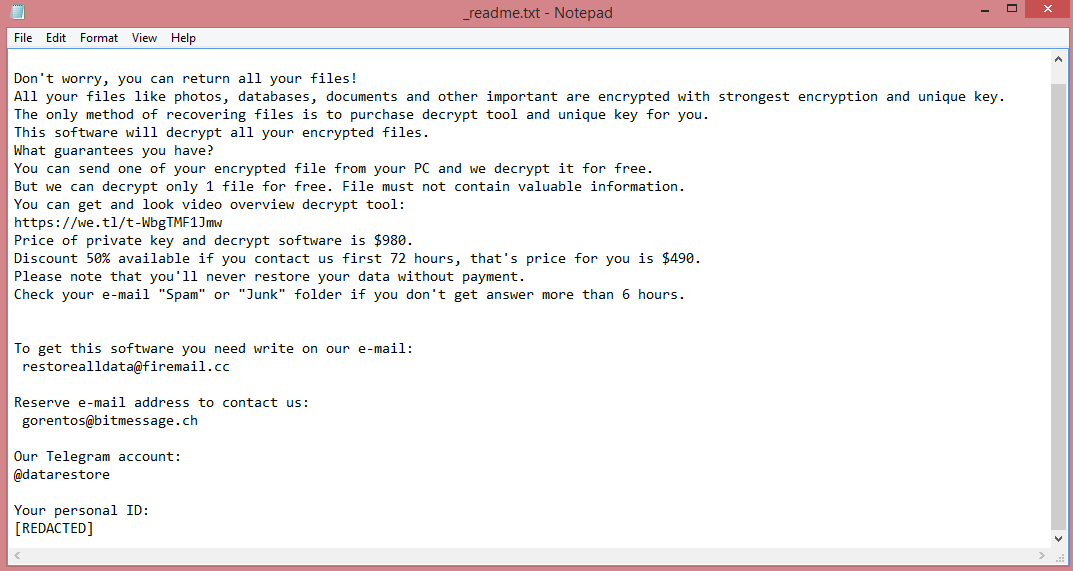
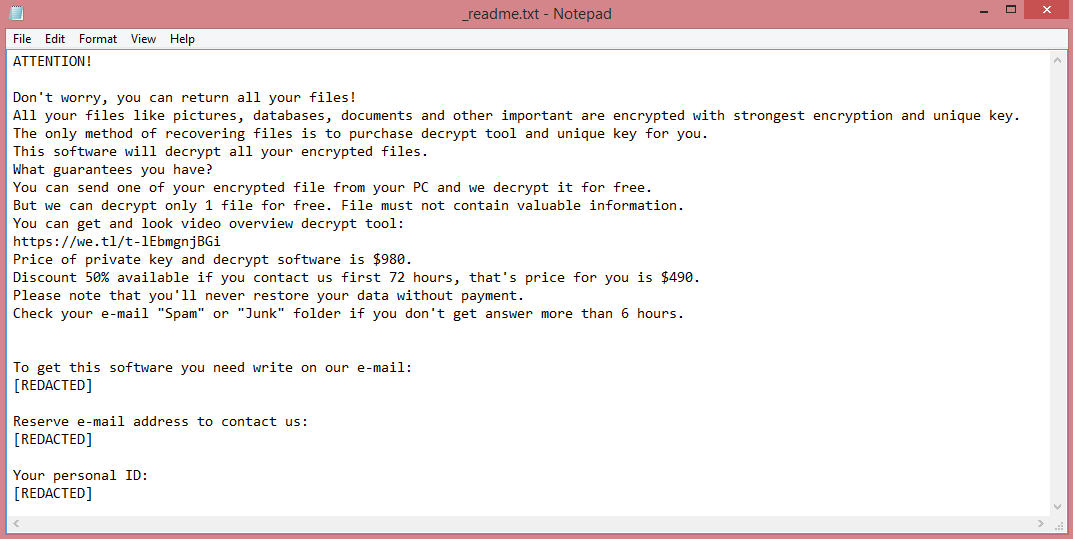
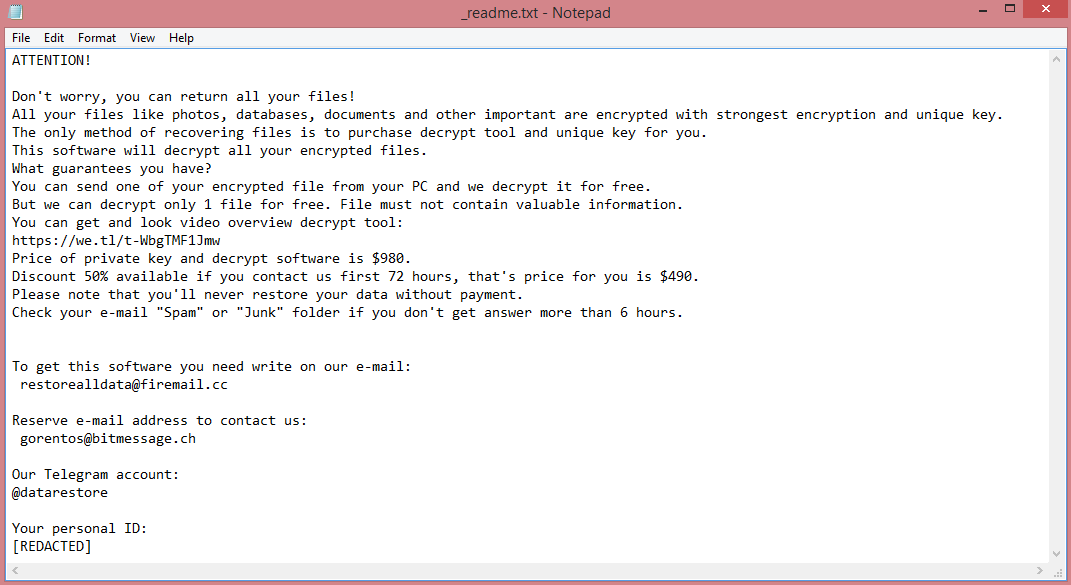
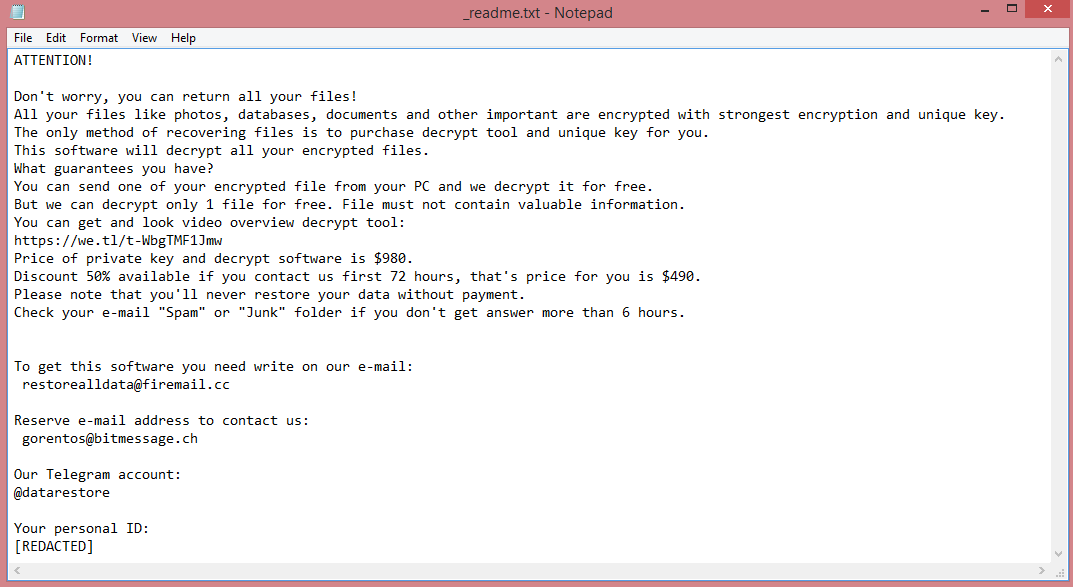
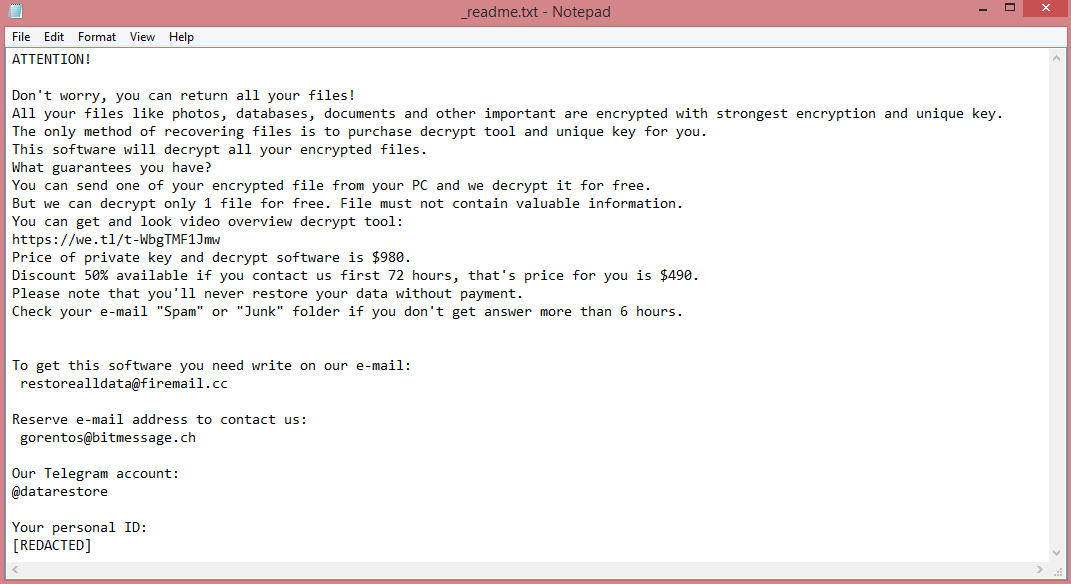
As a variant of STOP/Djvu, Vypt shares many similarities with other such variants. All of them have four-letter names: Coty, Boza, and Kifr are a few examples. More importantly, all STOP/Djvu viruses have identical ransom notes, and, consequently, identical demands. Vypt ransom note can be read on the image above.
The demands contained in these notes are pretty simple; the hackers want 980 US dollars. They do not mention how this money must be paid. Instead, the victim is simply told to contact the criminals via e-mail. To pressure hesitant victims into paying, the hackers also offer a 50% discount for those who pay within three days.
Paying the attackers is problematic for several reasons. Firstly, you’ll be encouraging them to carry out further attacks, which may once again target you. Secondly, criminals are not trustworthy; it is likely that they will not bother decrypting your files even after receiving payment.
This is why you should explore alternative ways to remove Vypt ransomware and decrypt .vypt files. Read our guide for an overview.
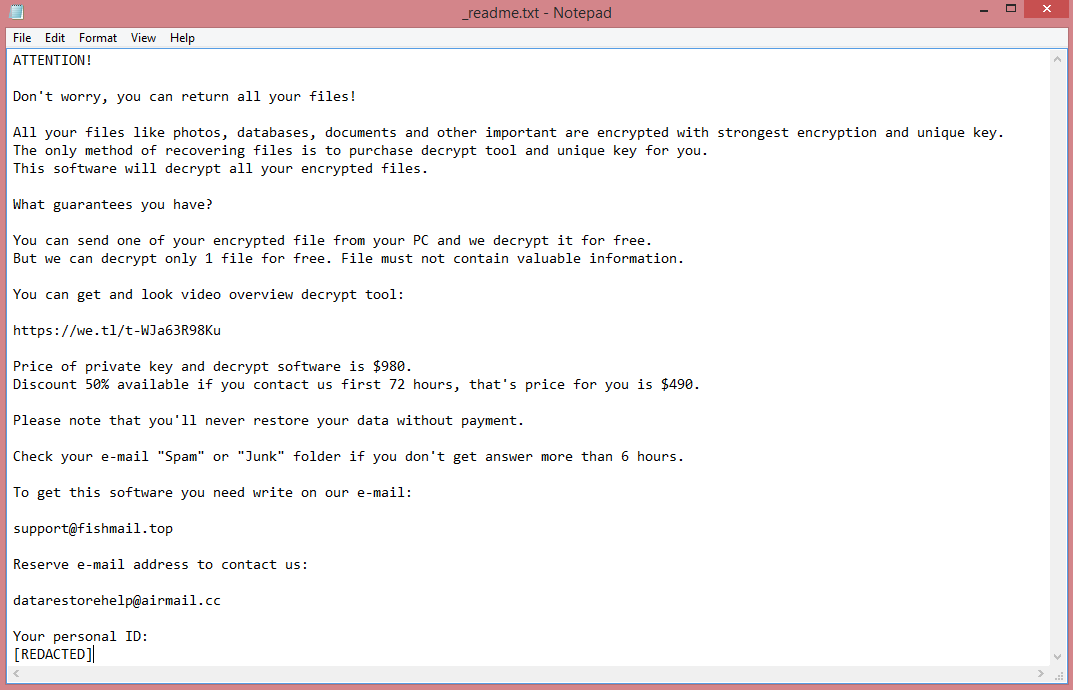
![Proton ransom note:
~~~ Proton ~~~
What happened?
We encrypted and stolen all of your files.
We use AES and ECC algorithms.
Nobody can recover your files without our decryption service.
How to recover?
We are not a politically motivated group and we want nothing more than money.
If you pay, we will provide you with decryption software and destroy the stolen data.
What guarantees?
You can send us an unimportant file less than 1 MG, We decrypt it as guarantee.
If we do not send you the decryption software or delete stolen data, no one will pay us in future so we will keep our promise.
How to contact us?
Our Telegram ID: @ransom70
Our email address: Kigatsu@tutanota.com
In case of no answer within 24 hours, contact to this email: Kigatsu@mailo.com
Write your personal ID in the subject of the email.
Your personal ID: [REDACTED]
Warnings!
- Do not go to recovery companies, they are just middlemen who will make money off you and cheat you.
They secretly negotiate with us, buy decryption software and will sell it to you many times more expensive or they will simply scam you.
- Do not hesitate for a long time. The faster you pay, the lower the price.
- Do not delete or modify encrypted files, it will lead to problems with decryption of files.
This is the end of the note. Below you will find a guide explaining how to remove Proton ransomware and decrypt .kigatsu files.](https://www.computips.org/wp-content/uploads/2023/04/how-to-remove-proton-ransomware.png)