![Reopen ransom note:
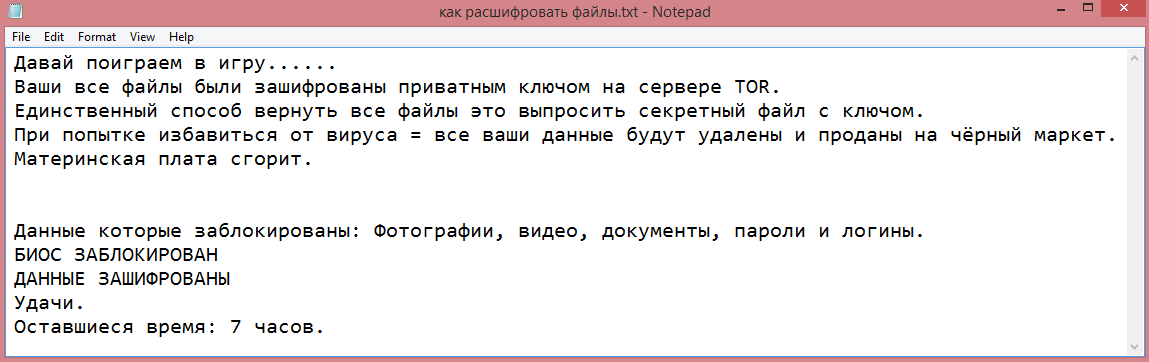
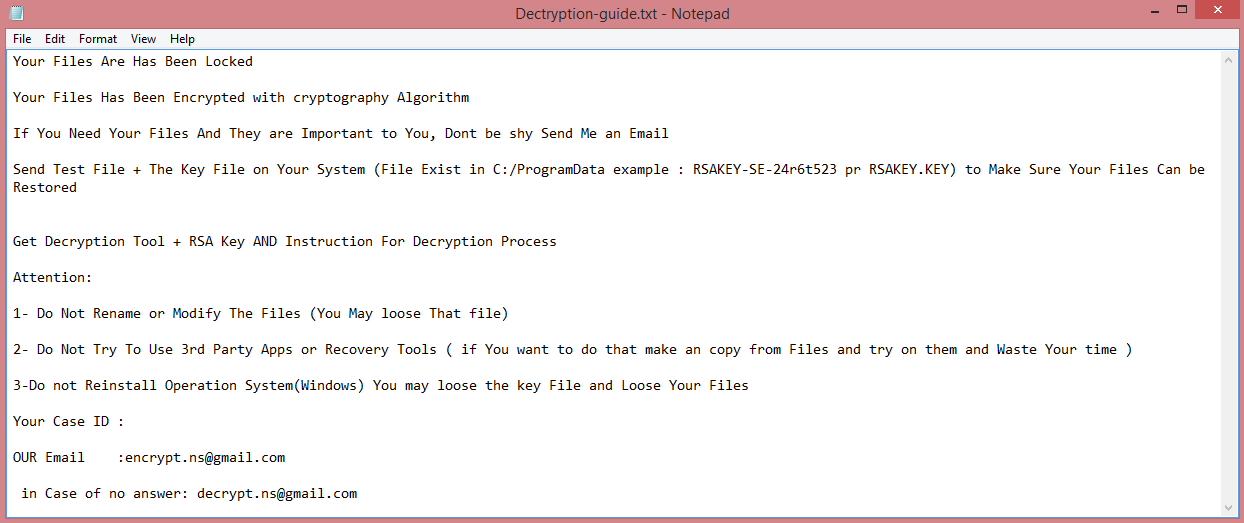
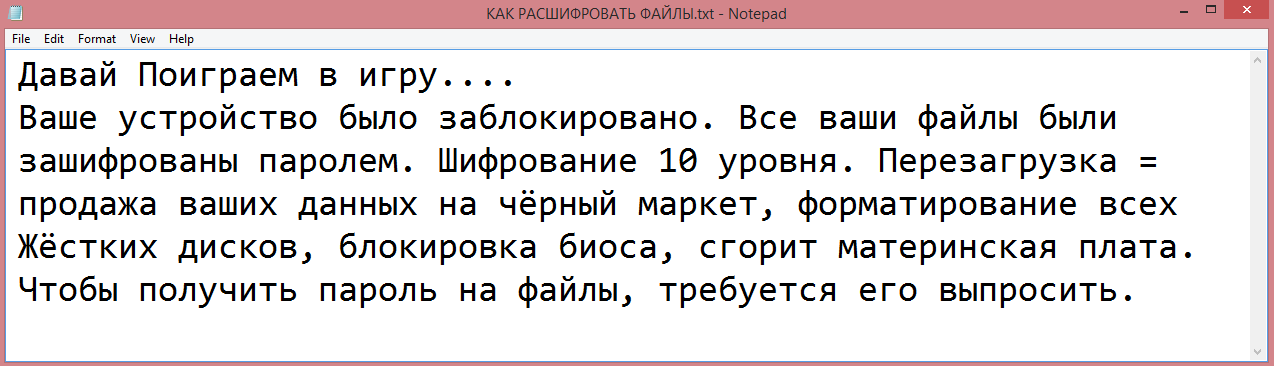
Your Files Are Has Been Locked
Your Files Has Been Encrypted with cryptography Algorithm
If You Need Your Files And They are Important to You, Dont be shy Send Me an Email
Send Test File + The Key File on Your System (File Exist in C:/ProgramData example : KEY-SE-24r6t523 or RSAKEY.KEY) to Make Sure Your Files Can be Restored
Make an Agreement on Price with me and Pay
Get Decryption Tool + RSA Key AND Instruction For Decryption Process
Attention:
1- Do Not Rename or Modify The Files (You May loose That file)
2- Do Not Try To Use 3rd Party Apps or Recovery Tools ( if You want to do that make an copy from Files and try on them and Waste Your time )
3-Do not Reinstall Operation System(Windows) You may loose the key File and Loose Your Files
4-Do Not Always Trust to Middle mans and negotiators (some of them are good but some of them agree on 4000usd for example and Asked 10000usd From Client) this Was happened
Your Case ID : [REDACTED]
Our Email:Reopenthefile@gmail.com
This is the end of the note. Below you will find a guide explaining how to remove Reopen ransomware.](https://www.computips.org/wp-content/uploads/2023/03/how-to-remove-reopen-ransomware.png)
What is Reopen ransomware?
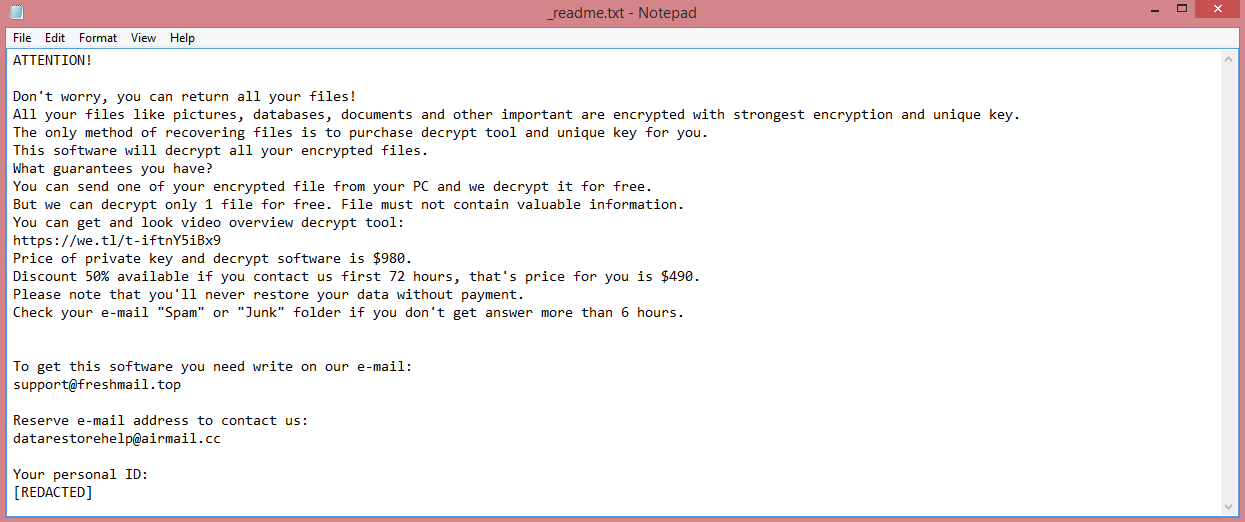
Reopen is a recently-developed virus that encrypts your files and demands payment to make them accessible again. Unsurprisingly, this category of viruses is called ransomware.
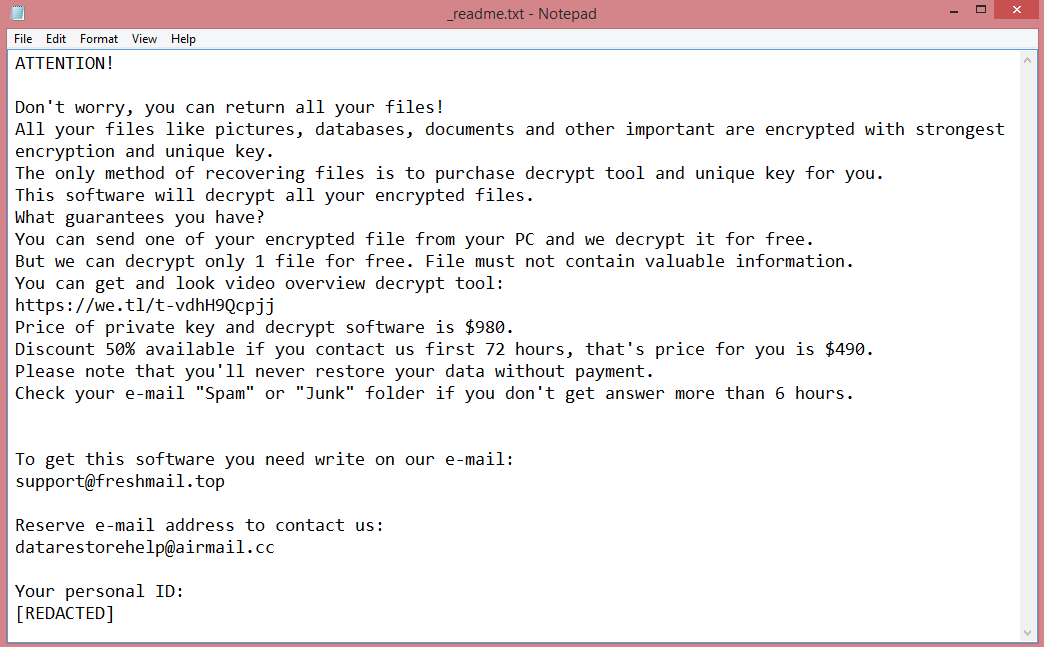
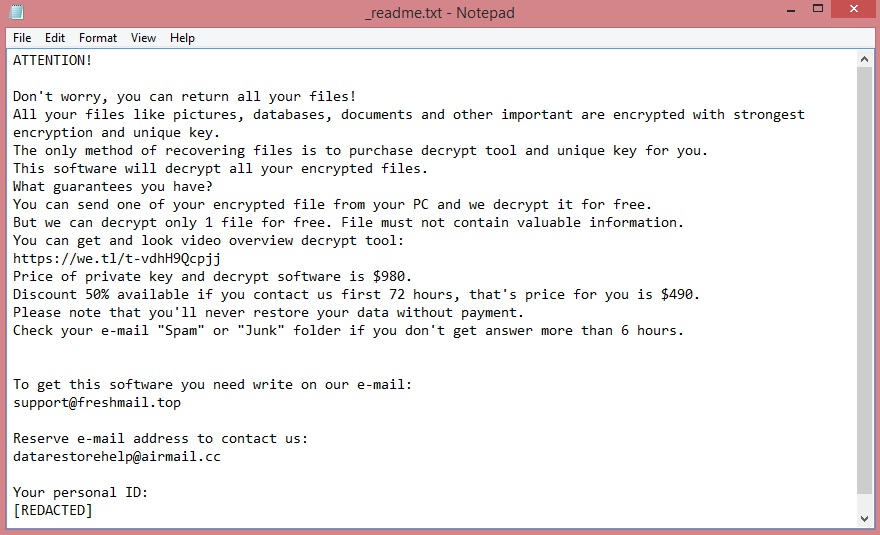
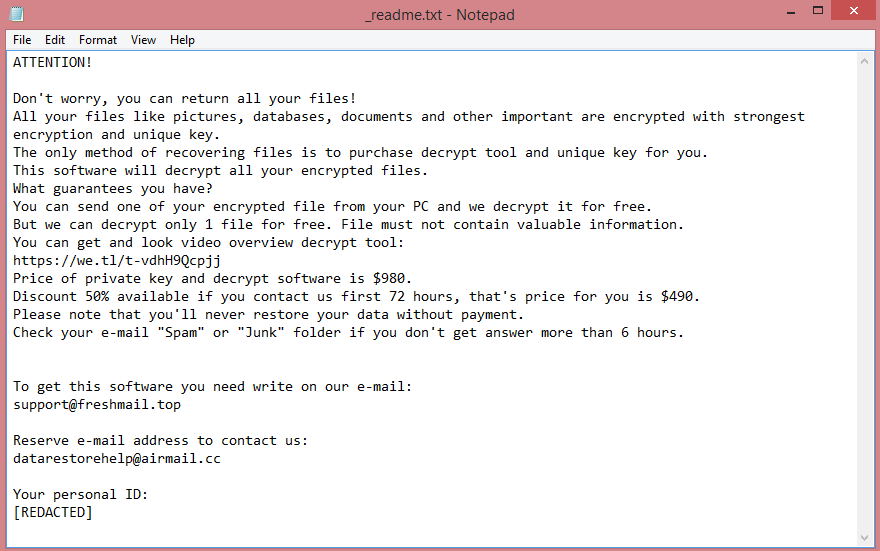
This virus belongs to the VoidCrypt ransomware family. In simple terms, this means that Reopen is not a unique virus; it was made using a template. This becomes apparent by reading the ransom note left by the virus (a text file named “INFORMATION.TXT”). You can read it on the image above; it is very similar to ransom notes left by other VoidCrypt viruses such as Eking.
Reopen also modifies the names of the files after encrypting them. An e-mail address belonging to the hackers, a victim’s ID, and .reopen file extension are added to the end of each file name. The virus does this so that inattentive victims who somehow miss the ransom note could still notice that they were attacked.
Of course, it is not a good idea to contact the criminal. Although some do, indeed, decrypt the files after payment, many of them simply take the money and disappear. This is why you should learn about other ways to remove Reopen ransomware and decrypt .reopen files. The guide below can help you with that.
![SkullLocker ransom note:
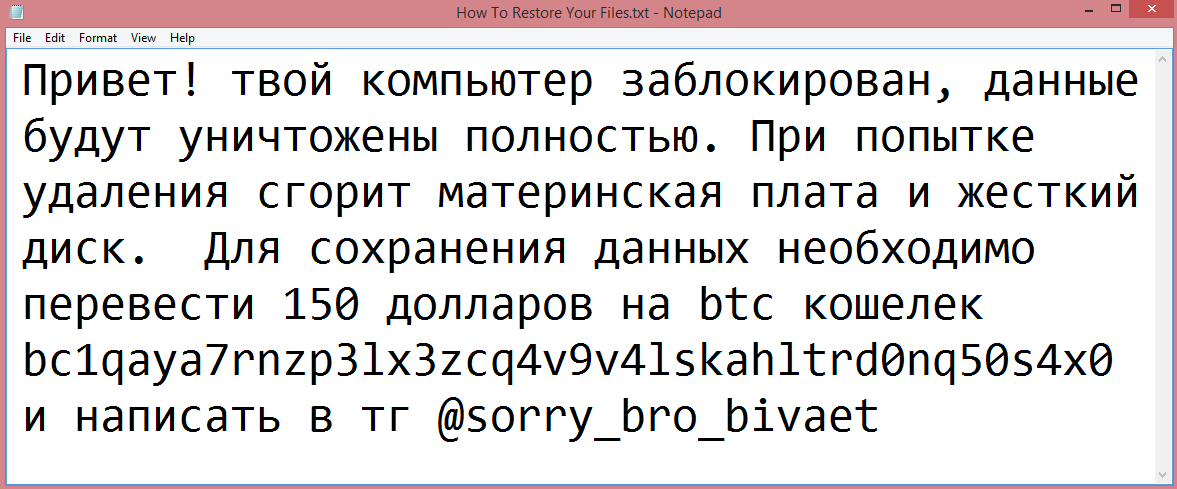
Witaj,
Twoje pliki zostały zaszyfrowane przez SkullLocker ransomware. Aby odzyskać dostęp do nich, musisz zapłacić okup w ciągu 72 godzin. W przeciwnym razie dane zostaną trwale utracone.
Aby uzyskać więcej informacji na temat sposobu zapłaty okupu i odzyskiwania plików, przejdź na stronę internetową podaną poniżej.
[REDACTED]
Jeśli masz jakiekolwiek pytania, możesz skontaktować się z nami za pomocą adresu e-mail [REDACTED].
Nie próbuj usuwać programu ransomware ani próbować odzyskać danych za pomocą oprogramowania antywirusowego. Może to spowodować trwałe uszkodzenie Twoich plików.
Pamiętaj, że czas jest kluczowy. Im dłużej zwlekasz, tym mniejsze szanse na odzyskanie Twoich plików.
Pozdrawiamy,
Zespół ransomware
This is the end of the note. Below you will find a guide explaining how to remove SkullLocker ransomware.](https://www.computips.org/wp-content/uploads/2023/03/how-to-remove-skulllocker-ransomware.png)