What is Djvu ransomware
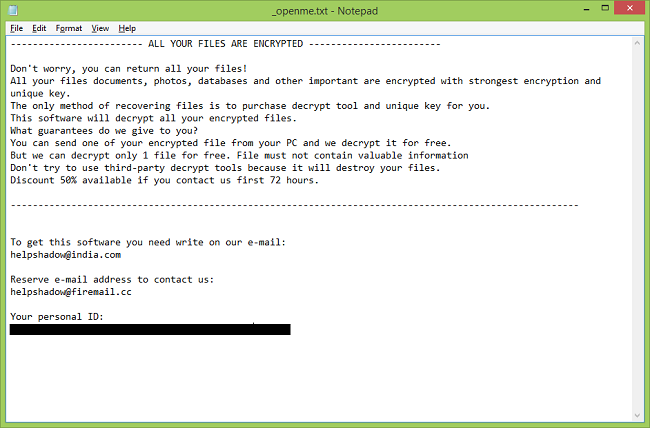
Professional users are aware of viruses such as extortionists. Djvu ransomware refers specifically to this type of virus. Djvu ransomware, also known as djvu files virus, is a very risky computer infection which modifies the Windows Registry. According to some information, this virus links with Stop Ransomware, because it shows the _openme.txt message, that gives an invasion and requires unlock files by contacting with us giving before this email helphadow@india.com or restorejvu@firemail.com to discuss the price of the decryptor and even a 50% discount if the answer lasts for 72 hours! There are several versions of djvu ransomware : Djvus virus, Djvuu virus, Uudjvu ransomware, Udjvuq ransomware. The activity of this crypto-extortionist came at the beginning of June 2018. It is focused on English-speaking users, but this does not prevent spreading it around the world. So, if you want to know how to remove djvu ransomware from your computer and decrypt .djvu files, read our article.
The content of the redemption text:
All your important files were encrypted on this computer.
You can verify this by clicking on see files and try to open them.
Encryption was produced using unique public key RSA-4096 generated for this computer.
To decrypted files, you need to obtain the private key.
The single copy of the private key, with will allow you to decrypt the files, is located on a secret server on the internet;
The server will destroy the key within 48 hours after encryption completed.
To retrieve the private key, you need to pay 2 bitcoins IMPORTANT YOU HAVE ONLY 48 HOURS IF U DON'T PAY ALL YOUR FILES WILL BE DELETED!
Bitcoins have to be sent to this address: 15sJ3pT7J6zefRs95SEsfBZMz8jAw1zAbh
After we confirm the payment , we send the private key so you can decrypt your system.
Variations of encryption`s titles:
.1cd, .3gp, .ac3, gzip, .htm, .html, .ifo, .isr, .jar, .ace, .ape, .avi, .BAC, .BAK, .bak,cer, .csv, .dat, .dbf, .docx, .bat, .bkf, .bmp, .cap, .cdr, .drt, .dwg, .edb, .erf, .exe, .EXE, .flac, .flv, .FPT, .frm, .gif, . .JAVA, .jpeg, .jpg, .kwm, .xlsx, .xlt, .xml, .zip.
At the moment there are 73 options for extensions, there is a part of them:
.cerber
.LOCKED
.workencryptincfolder@india.com=.cerberV5
.xdata
.0JELvV
.5vypSa
.6FKR8d
.7ineServices@gmail.com
.decryptoffice@tuta.io
Also, there is a frequent update of the extensions of this virus, which indicates that soon there may be more and more.
There is a little part of them:
extension:cerberV5
Update: April 18, 2017
extension:decripted2017@gmail.com
Update: May 12, 2017
extension:SaMsUnG
How to Remove Djvu ransomware
If you do not want this virus will continue to encrypt all files (photos, documents ) by using a reliable encryption algorithm, you ought to immediately remove it.The easiest way to rid of Djvu ransomware is to delete this automatically.
However, if you want to try all possible ways of recovering .phobos files, including data recovery tools, then I suggest you use these tools first and scan with anti-malware later. Skip to the explanation
How to Recover .phobos files
If you want to recover files encrypted by ransomware you can either try to decrypt them or use methods of file recovery.
Ways to decrypt the files:
- Contact the ransomware authors, pay the ransom and possibly get the decryptor from them. This is not reliable: they might not send you the decryptor at all, or it might be poorly done and fail to decrypt your files.
- Wait for security researchers to find some vulnerability in the ransomware that would allow you to decrypt .phobos files without paying. This turn of events is possible but not very probable: out of hundreds of known ransomware variants only dozens were found to be decryptable for free. You can visit NoMoreRansom site from time to time to see if free decryptor for Phobos exists.
- Use paid services for decryption. For example, antivirus vendor Dr. Web offers its own decryption services. They are free for users of Dr.Web Security Space and some other Dr. Web’s products if Dr. Web have been installed and running at the time of encryption (more detail). For users of other antiviruses the decryption, if it’s deemed possible, might cost €150 or more. According to Dr. Web’s statistics, the probability of them being able to restore files is roughly 10%.
Other ways to recover encrypted files:
-
- Restore from backup. If you make regular backups to a separate device and check from time to time that those are in working order and files can be successfully restored – well, you probably won’t have any problems getting back your files. Just scan your computer with a couple of AVs and anti-malware programs or reinstall operating system, and then restore from backup.
- Recover some files from cloud storage (DropBox, Google Drive, OneDrive, etc.) if you have one connected. Even if encrypted files were already synced to the cloud, a lot of cloud services keep old versions of altered files for some time (usually 30 days).
- Recover Shadow Volume Copies of your files if those are available – ransomware usually tries to delete them too. Volume Shadow Copy Service (VSS) is a Windows technology that periodically creates snapshots of your files and allows you to roll back changes made on those files or recover deleted files. VSS is enabled together with System Restore: it’s turned on by default on Windows XP to Windows 8 and disabled by default on Windows 10.
- Use file recovery software. This probably won’t work for Solid State Drives (SSD – it is a newer, faster and more expensive type of data-storage devices) but is worth a try if you store your data on a Hard Disc Drive (HDD – older and more common as of yet storage device). When you delete a file from your computer – and I mean completely delete: use Shift + Del or empty the Recycle Bin – on SSD it gets wiped from the drive right away. On HDD however, it rather gets marked as deleted, and the space it occupies on a hard drive – as available for writing, but the data is still there and usually recoverable by special software. However, the more you use the computer, especially if you do something that writes new data on the hard drive, the more chance that your deleted file gets overwritten and will be gone for good. That is why, in this guide we will try to recover deleted files (as you might know, ransomware creates an encrypted copy of a file and deletes the original file) without installing anything on a disk. Just know that this still might not be enough to successfully recover your files – after all, when ransomware creates encrypted files it writes new information on a disk, possibly on top of files it just deleted. This actually depends on how much free space is there on your hard drive: the more free space, the less chance that new data will overwrite the old data.
Going further, we need to 1) stop ransomware from encrypting files that we recover, if malware is still active; 2) try not to overwrite files deleted by ransomware. The best way to do it is disconnect your hard drive and connect it to another computer. You will be able to browse all your folders, scan them with antivirus programs, use file recovery software or restore data from Shadow Volume Copies. Although it is better to download all tools you’ll need beforehand and disconnect the computer from the Internet before connecting the infected hard drive, just to be safe.
Disadvantages of this method:
-
-
- This might void your warranty.
- It’s harder to do with laptops, and you’ll need a special case (disk enclosure) to put a hard drive in before connecting it to another machine.
- It is possible to infect the other computer if you open a file from the infected drive before scanning the drive with AVs and removing all found malware; or if all AVs fail to find and delete the malware.
-
Another, easier, way is to load into Safe Mode and do all file recovery measures from there. However, that will mean using the hard drive and potentially overwriting some data. In this case it’s preferable to use only portable versions of recovery software (the ones that don’t require installation), download them onto an external device, and save any recovered files onto an external device as well (external hard drive, thumb drive, CD, DVD, etc.).
Boot Into Safe Mode:
 Windows XP,
Windows XP,  Windows Vista,
Windows Vista,  Windows 7:
Windows 7:
-
-
- Restart the computer.
- Once you see a boot screen tap F8 key continuously until a list of options appears.
- Using arrow keys, select Safe Mode with Networking.
- Press Enter.
-
 Windows 8,
Windows 8,  Windows 8.1,
Windows 8.1,  Windows 10:
Windows 10:
-
-
- Hold down Windows key
 and hit X key.
and hit X key. - Select Shut down or sign out.
- Press Shift key and click on Restart.
- When asked to choose an option, click on Advanced options => Startup Settings.
- Click Restart in the bottom right corner.
- After Windows reboots and offers you a list of options, press F5 to select Enable Safe Mode with Networking.
- Hold down Windows key
-
Back up Your Encrypted Files
It is always advisable to create a copy of the encrypted files and put it away. That might help you if free ransomware decryptor becomes available in the future, or if you decide to pay and get the decryptor but something goes wrong and files get irreparably damaged in the process of decryption.
Use File Recovery Tools to Recover Files
“Aiseesoft Data Recovery: Recover deleted/lost photo, audio, video, document and more from computer, hard drive, memory card, flash drive, mobile phone, etc.”
Screenshot:
R-Undelete
How to recover deleted files with R-Undelete
Puran File Recovery

Video guide on how to use Puran File Recovery
Recover Encrypted Files From Shadow Copies.
The easiest way to access Shadow Volume Copies is by using a free tool called Shadow Explorer. Just download the latest version and install it (or download the portable version).
-
-
- Launch Shadow Explorer.
- On the top left part of the window you can select a disk (C:\, D:\, etc.) and a date when a snapshot of files was taken.
- To recover a file or a folder right-click on it and select Export….
- Choose where do you want to put the files.
-
Remove Phobos Ransomware
Now that you have your recovered or still encrypted files on an external device, it is time to scan your computer with AV and anti-malware software or, better yet, reinstall the operating system, to fully get rid of possible ransomware traces. Remember to also scan your external device before putting files back on your computer!
Ningún programa stellar, es capas de desencriptar nada, tiene otras funciones pero no la Desencriptar
j ai ete cripte par extention vvoa impossible de recuperer mes photos