What is Mppn ransomware?
Mppn is a ransomware program that belongs to the STOP/Djvu family of ransomware. It operates in the same fashion as all other ransomware programs: it encrypts files on the infected computer, then renames them (adding .mppn file extension to the end of the name), and leaves a ransom note named “_readme.txt”. However, it is even more similar to other STOP/Djvu viruses, as they always have the same demands (which you can confirm by reading about any other STOP/Djvu ransomware, for example Mbtf ransomware).
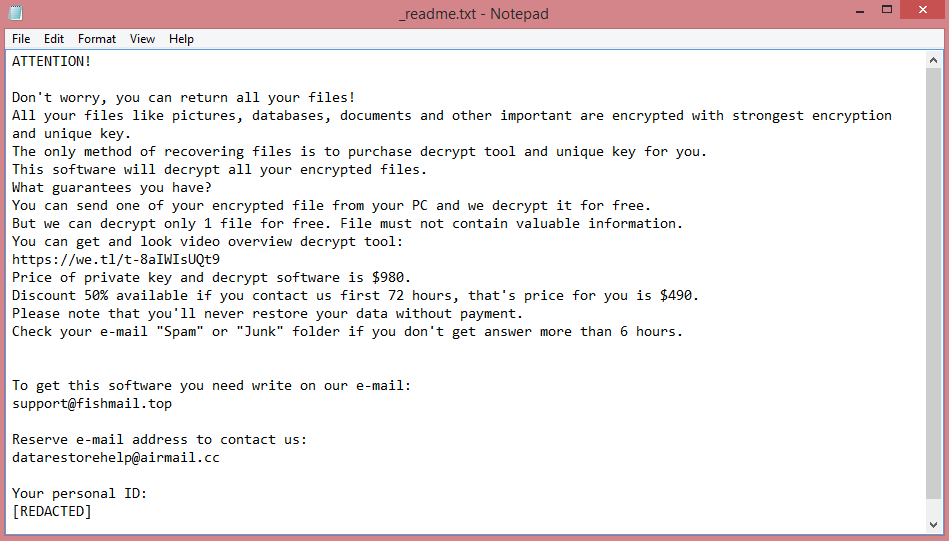
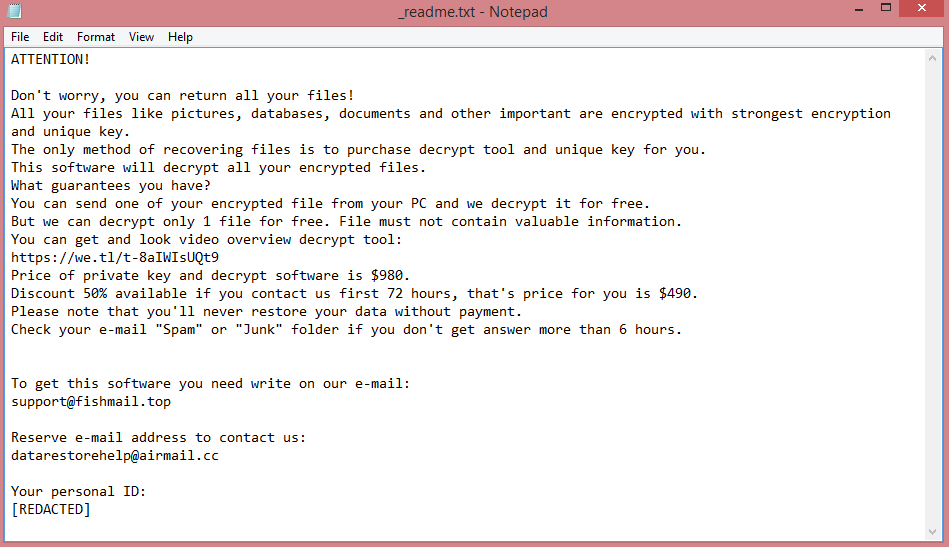
The image above is a screenshot of the Mppn ransom note; you can read it to see what the hackers demand and how they go about it. Or, you can keep reading as we will summarize the note in the next paragraph.
Mppn demands $980 for decryption; however, they also promise a 50% discount should the victim pay within 3 days of infection. This is a well-known manipulation tactic. By creating a sense of urgency, they make it more likely that the victims will contact them.
Don’t fall for it. Few ransomware hackers even bother decrypting the files; most just take the money and cease all communications afterwards. This is why you should explore alternative ways to remove Mppn ransomware and decrypt .mppn files, such as these explained in the guide below.