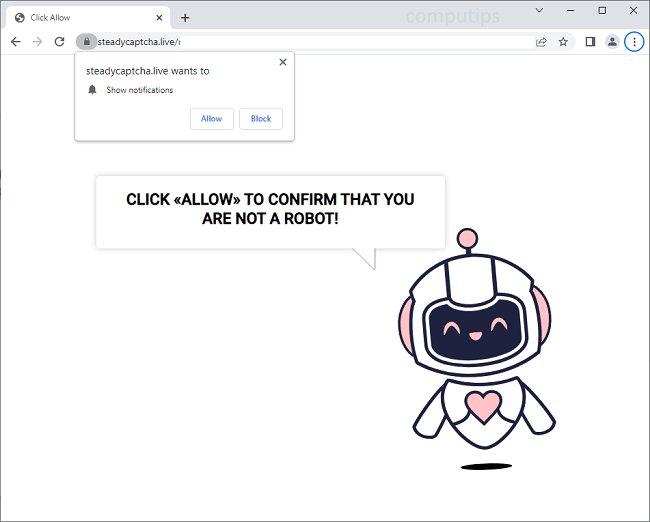
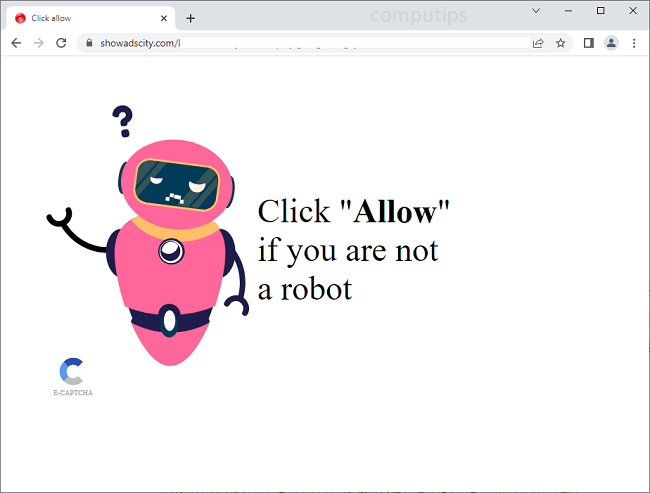
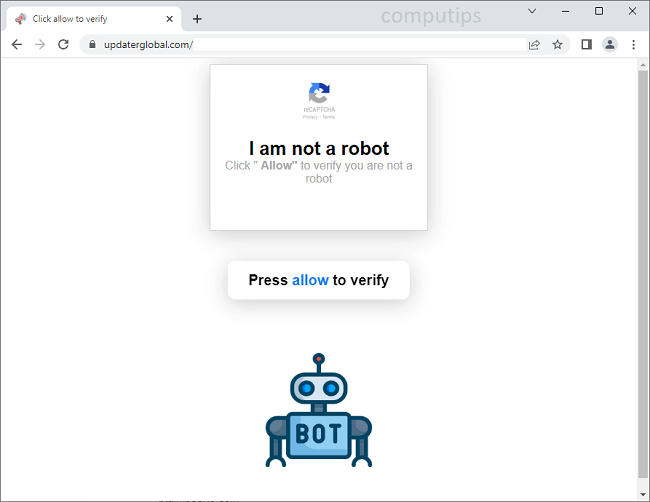
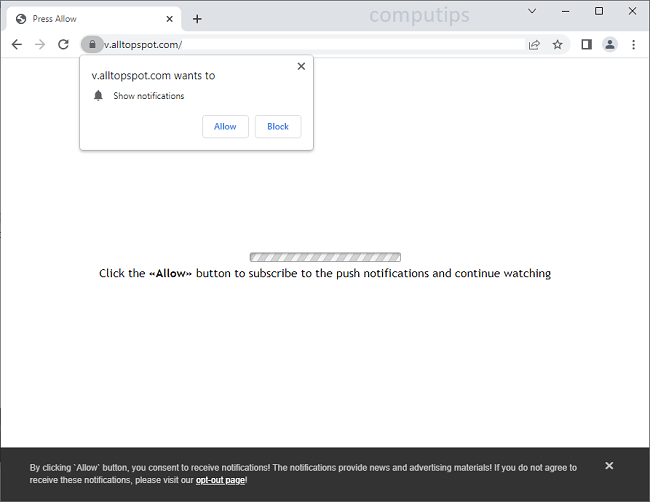
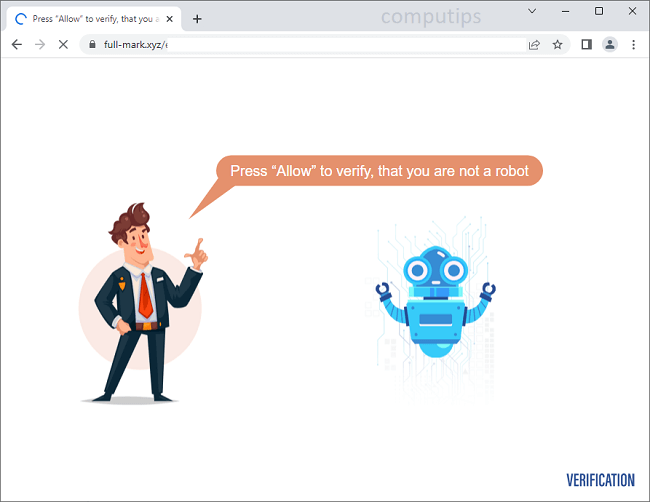
What Is Steady Captcha Live?
Steady Captcha Live (steadycaptcha.live, a.steadycaptcha.live, b.steadycaptcha.live, etc.) is a questionable website which tries to make users turn on its notifications. Site notifications are pop-ups with news and updates from sites that appear in the lower right hand corner of the screen on Windows computers, in the top right hand corner of the screen on Macbooks, and on the status bar on Android devices. Steady Captcha Live claims that users need to click Allow on its notifications confirmation pop-up to verify that they are not robots. Once allowed, the notifications will start spamming users with ads, prompts to download some programs, fraudulent messages, fake alerts from the OS, etc.
![Vohuk ransom note:
[~] Vohuk Ransomware V1.3
>>> What's happened?
ALL YOUR FILES ARE STOLEN AND ENCRYPTED.
To recovery your data and not to allow data leakage, it is possible only through purchase of a private key from us.
>>> What guarantees?
We are not a politically motivated group and we do not need anything other than your money.
Before paying you can send us up to 2 files for free decryption.
The total size of files must be less than 2MB(non archived).
files should not contain valuable information. (databases, backups, large excel sheets, etc.)
>>> CONTACT US:
Please write an email to both: payordiebaby@tutanota.com & payordiebaby69@msgsafe.io
Write this Unique-ID in the title of your message: [REDACTED]
>>> ATTENTION!
Do not delete or rename or modify encrypted files.
Do not try to decrypt using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price(they add their fee to our).
We use strong encryption, nobody can restore your files except us.
The price depends on how fast you contact with us.
remember to hurry up, as your email address may not be available for very long.
All your stolen data will be loaded into cybercriminal forums/blogs if you do not pay ransom.
If you do not pay the ransom we will attack your company repeatedly again.
This is the end of the note. Below you will find a guide explaining how to remove Vohuk ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-vohuk-ransomware.png)
![CryptBIT 2.0 ransom note:
Hello!
Now your files are crypted with the strongest millitary algorithms RSA4096 and AES-256.
In addition, all encrypted files have been sent to our server
and in the event of non-payment within 7 days,they will be made public.
Warning!
Do not rename encrypted files.
Do not try to decrypt your data using third party software.
You can only do damage to your files, lose your money and time.
In order to confirm that we are not scammers, you can send 2-3 files to the email address below.
Files should be less than 5 MB and contain no valuable data (Databases, backups, large excel sheets, etc.).
Please don't forget to write the name of your company in the subject of your e-mail.
You will receive decrypted samples.
To recover all files you must contact us for a private quote by the contact email.
You have to pay for decryption in Bitcoins.
P.S. Remember, we are not scammers.
We don't need your data or information but after 7 days all files and keys will be deleted automatically.
Write to us immediately after infection
All your files will be restored. We guarantee.
Contact email:
cryptbit2.0@protonmail.com
BTC wallet:
[REDACTED]
Have a nice day
CryptBIT 2.0 ransomware group
This is the end of the note. Below is a guide explaining how to remove CryptBIT 2.0 ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-cryptbit-2.0-ransomware.png)