What is Erqw ransomware?
Erqw is a file-encrypting virus, which means that it’s classified as ransomware. More specifically, Erqw is a variant of STOP/Djvu ransomware.
There are thousands of such variants, and hundreds of recent ones. That is because it is very easy for the hackers to produce a new STOP/Djvu variant; all of them strongly resemble one another as hackers reuse most of the code. For example, if you check out Assm ransomware, another STOP/Djvu variant that’s been active recently, you will find that it’s very similar to Erqw.
The easiest way to tell these viruses apart is to look at the names of encrypted files. Very often, ransomware programs will rename them; in our case, the files are given .erqw file extension. This means that a file named “song.mp3” would be renamed to “song.mp3.erqw” after encryption.
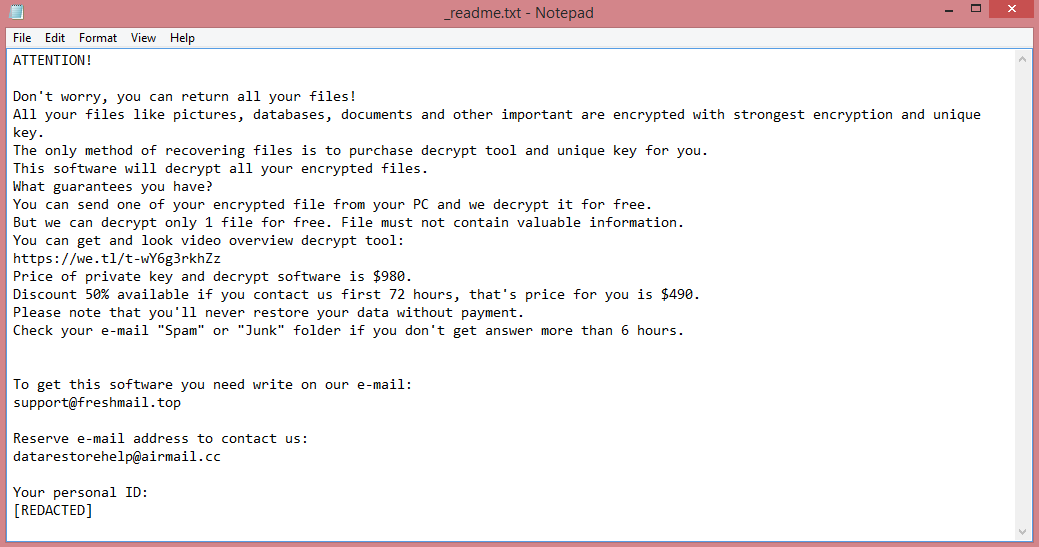
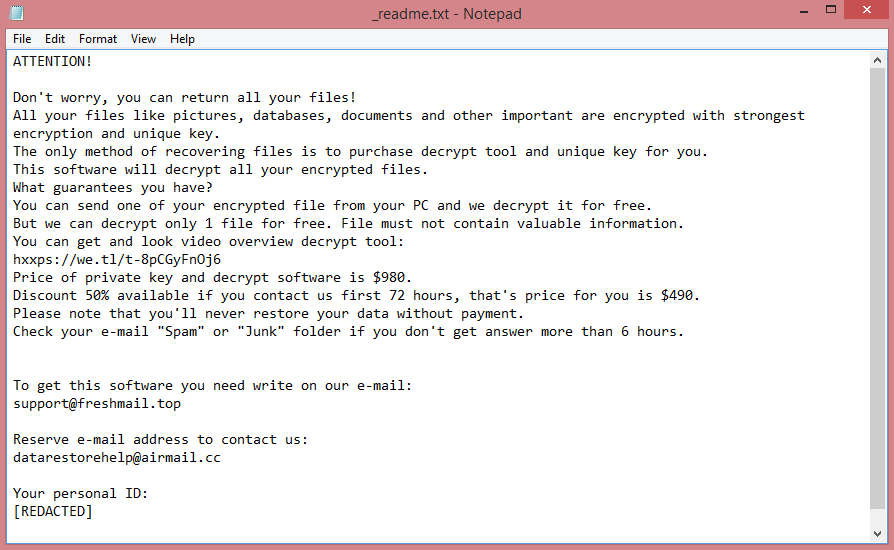
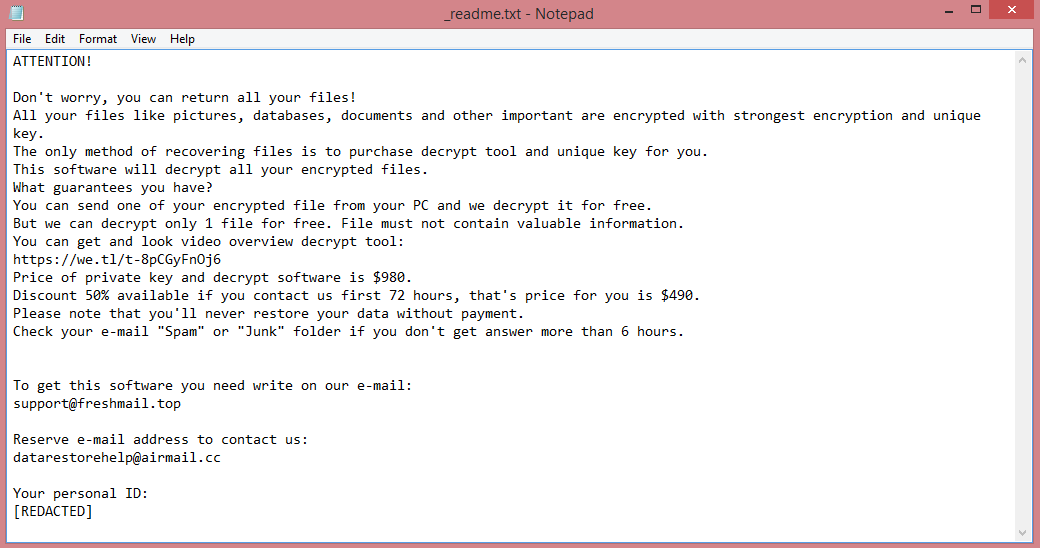
Erqw virus creates a ransom note, named “_readme.txt”, to communicate its demands to the victim. It demands $980 in ransom, or $490 if paid within 72 hours after the attack. The note frames it as a discount, however it simply means that the price will double after three days.
This increase in price is designed to manipulate the victims into paying, but you shouldn’t. There are other ways to remove Erqw ransomware and decrypt .erqw files, after all. The guide below lists a few.
![Masons ransom note:
Attention! All your files are encrypted!
To restore your files and access them,
send an SMS with the text [REDACTED] to the User Telegram
@mineralIaha/@root_king1
You have 1 attempts to enter the code. If this
amount is exceeded, all data will irreversibly deteriorate. Be
careful when entering the code!
Glory @six62ix
This is the end of the note. Below you will find a guide explaining how to remove Masons ransomware.](https://www.computips.org/wp-content/uploads/2023/02/how-to-remove-masons-ransomware.png)
![ZFX ransom note:
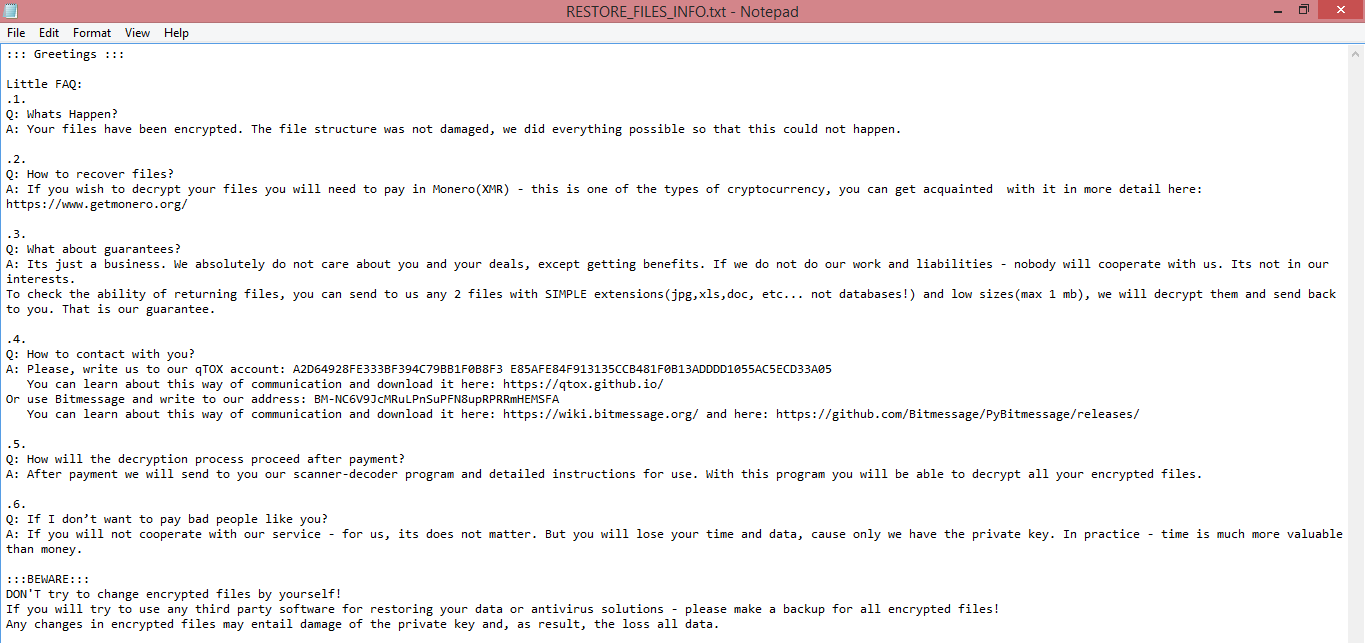
::: Hey :::
Small FAQ:
.1.
Q: What's going on?
A: Your files have been encrypted. The file structure was not affected, we did our best to prevent this from happening.
.2.
Q: How to recover files?
A: If you want to decrypt your files, you will need to pay us.
.3.
Q: What about guarantees?
A: It's just business. We are absolutely not interested in you and your transactions, except for profit. If we do not fulfill our work and obligations, no one will cooperate with us. It's not in our interest.
To check the possibility of returning files, you can send us any 2 files with SIMPLE extensions (jpg, xls, doc, etc... not databases!) and small sizes (max 1 mb), we will decrypt them and send them back to you. This is our
guarantee.
.4.
Q: How to contact you?
A: You can write to us at our mailboxes: CryptedData@tfwno.gf
.5.
Q: How will the decryption process take place after payment?
A: After payment, we will send you our scanner-decoder program and detailed instructions for use. With this program you will be able to decrypt all your encrypted files.
.6.
Q: If I don't want to pay bad people like you?
A: If you do not cooperate with our service - it does not matter to us. But you will lose your time and data because only we have the private key. In practice, time is much more valuable than money.
:::BEWARE:::
DO NOT try to modify encrypted files yourself!
If you try to use third party software to recover your data or antivirus solutions - back up all encrypted files!
Any changes to the encrypted files may result in damage to the private key and, as a result, the loss of all data.
Note:
::::::IF WE HAVE NOT RESPONSE YOU BY MAIL WITHIN 24 HOURS::::::
Spare contact for communication:
If we have not answered your email within 24 hours, you can contact us via the free messenger qTox
Download from the link https://tox.chat/download.html
Next go qTox 64-bit
after downloading the program, install it and go through a short registration.
Our Tox ID
[REDACTED]
This is the end of the note. Below you will find a guide explaining how to remove ZFX ransomware.](https://www.computips.org/wp-content/uploads/2023/01/how-to-remove-zfx-ransomware.png)