What Is Powerpcsupport.com?
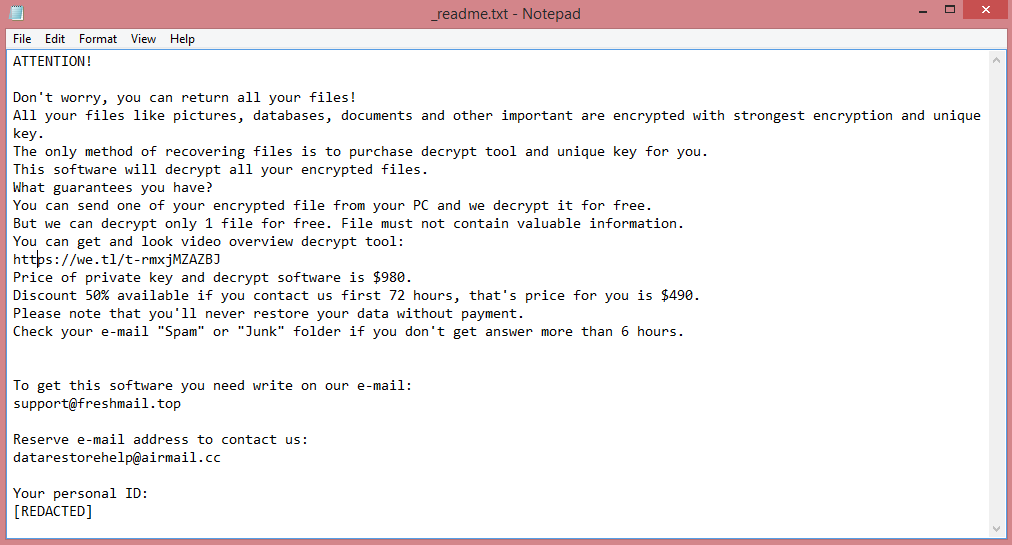
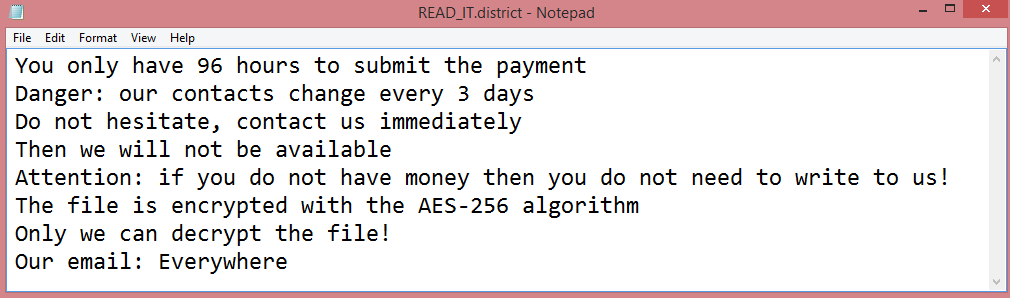
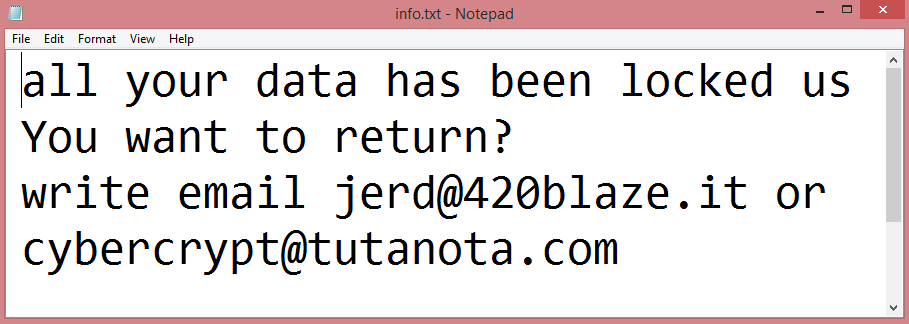
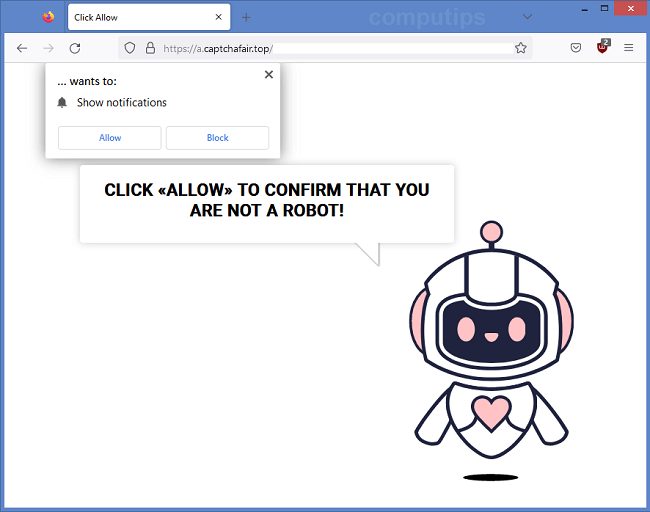
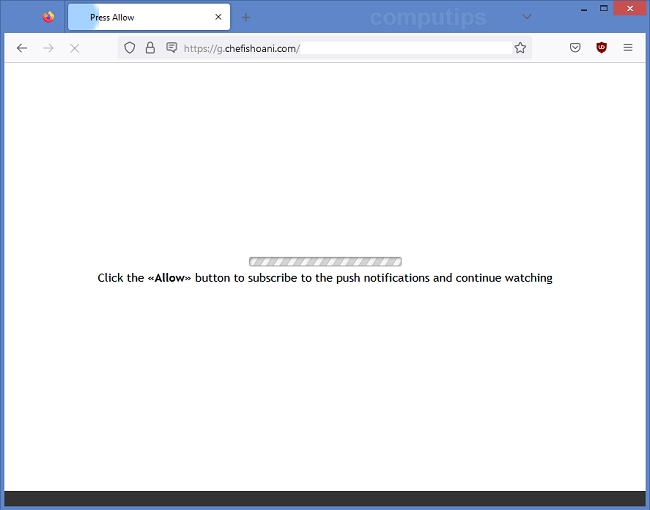
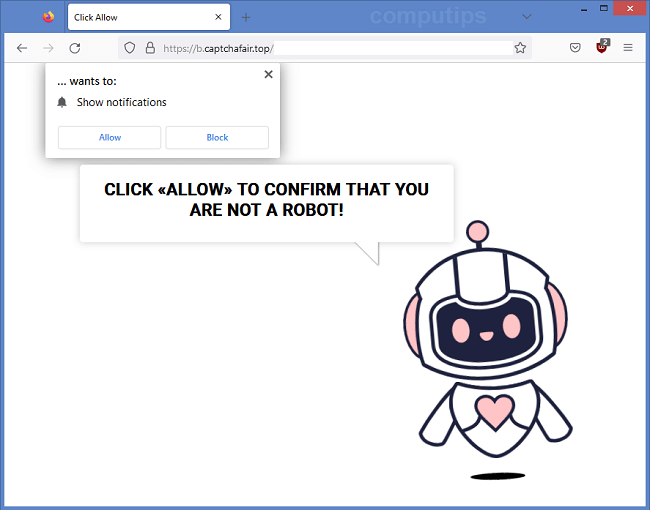
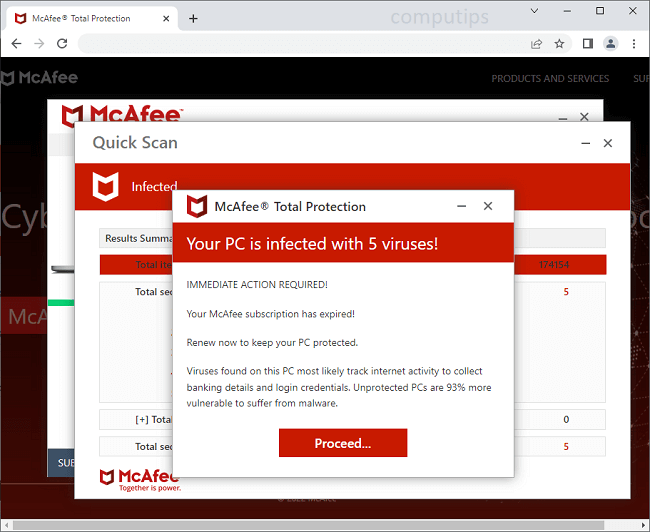
Powerpcsupport.com is a shady site which claims that users have malware on their computers and need to download an antivirus. There are numerous sites like that on the Internet: some of them provide affiliate links to actual antiviruses, while others push malware packages which may consist of adware, mining software, ransomware, etc. A user may get redirected to Powerpcsupport.com after following a dubious link or visiting a hacked webpage, or there may be adware on the user’s machine which keeps redirecting the user to various shady sites including Powerpcsupport.com. This step-by-step guide will help you uninstall adware and remove Powerpcsupport.com pop-ups or redirects from your browser.