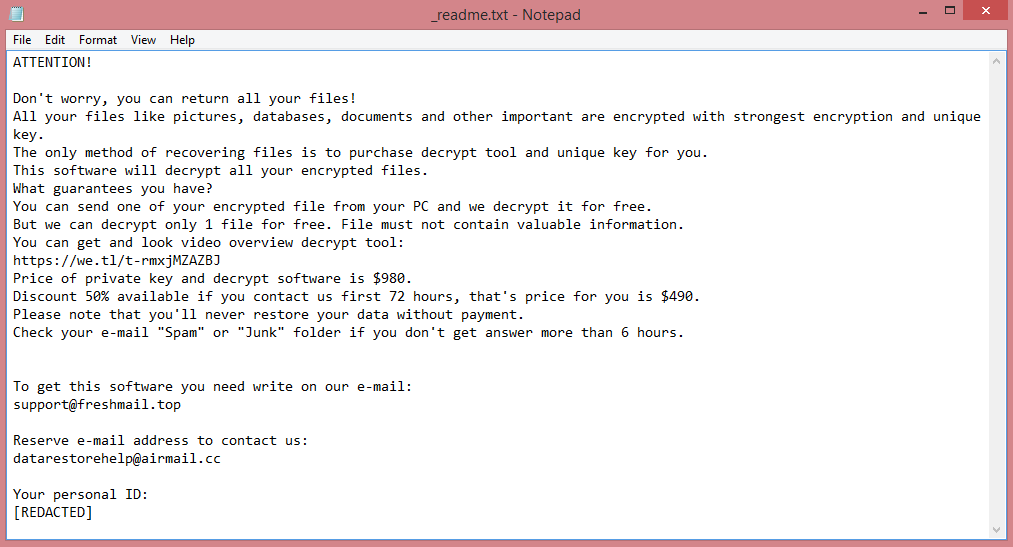
![Zendaya ransomware:
Your Files Are Has Been Locked
Your Files Has Been Encrypted with cryptography Algorithm
If You Need Your Files And They are Important to You, Dont be shy Send Me an Email
Send Test File + The Key File on Your System (File Exist in C:/ProgramData example : RSAKEY-SE-24r6t523 pr RSAKEY.KEY) to Make Sure Your Files Can be Restored
Make an Agreement on Price with me and Pay
Get Decryption Tool + RSA Key AND Instruction For Decryption Process
Attention:
1- Do Not Rename or Modify The Files (You May loose That file)
2- Do Not Try To Use 3rd Party Apps or Recovery Tools ( if You want to do that make an copy from Files and try on them and Waste Your time )
3-Do not Reinstall Operation System(Windows) You may loose the key File and Loose Your Files
4-Do Not Always Trust to Middle mans and negotiators (some of them are good but some of them agree on 4000usd for example and Asked 10000usd From Client) this Was happened
Your Case ID : [REDACTED]
OUR Email :Decryption.helper@aol.com
in Case of no answer: Decryption.help@cyberfear.com
This is the end of the note. Below you will find a guide explaining how to remove Zendaya ransomware.](https://www.computips.org/wp-content/uploads/2023/01/how-to-remove-zendaya-ransomware.png)
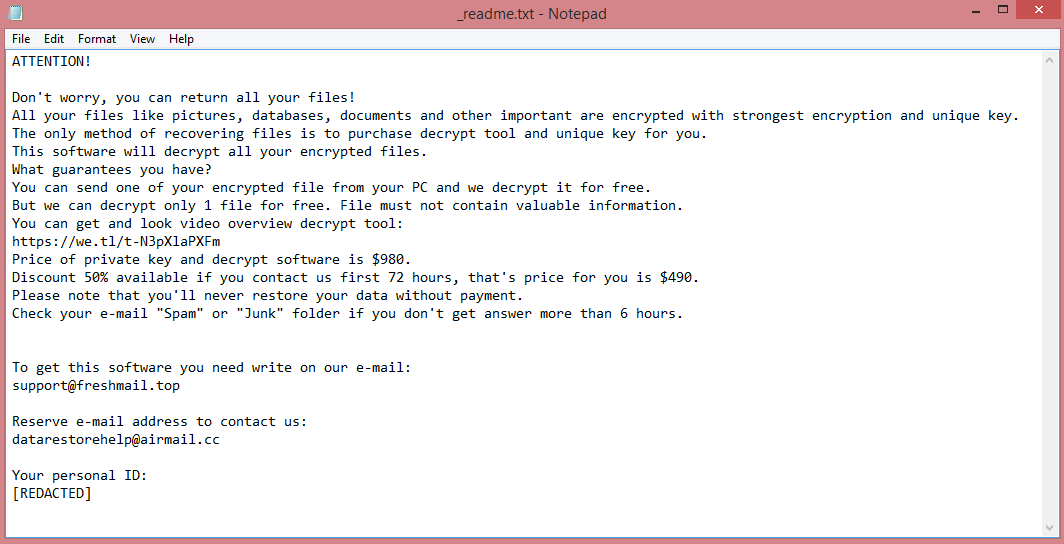
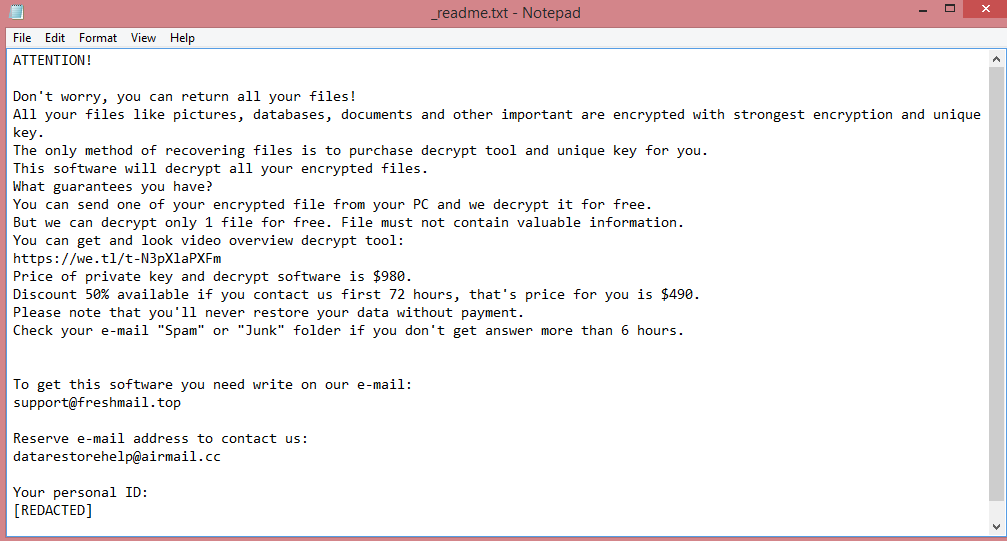
What is Zendaya ransomware?
Zendaya is a malicious program categorized as ransomware. This means that it encrypts all user files on the victims’ computers so that it can demand money for their decryption.
Ransomware viruses number in thousands, however, not all of them are unique. Many share parts of their code so that more variants can be produced. Groups of viruses that share code with each other are called families. Zendaya is a part of the VoidCrypt ransomware family; as such, it is similar to other viruses in it.
When Zendaya encrypts the files, it also renames them. Three pieces of information get appended to the end of each name: an ID, the victim’s e-mail, and .Zendaya file extension.
After this, two ransom notes are created, “Decryption-Guide.HTA” and “Decryption-Guide.txt”. Although they look different, they contain the same text (which you can read on the image above). The notes contain some instructions, but do not mention any specific price; the hacker intends to negotiate the price with each victim.
However, contacting the hacker involves several risks. For example, they can attack you again in the future, or simply take payment and not decrypt any files. This is why you may be interested in alternative ways to remove Zendaya ransomware and decrypt .Zendaya files. Some are described in the guide below.
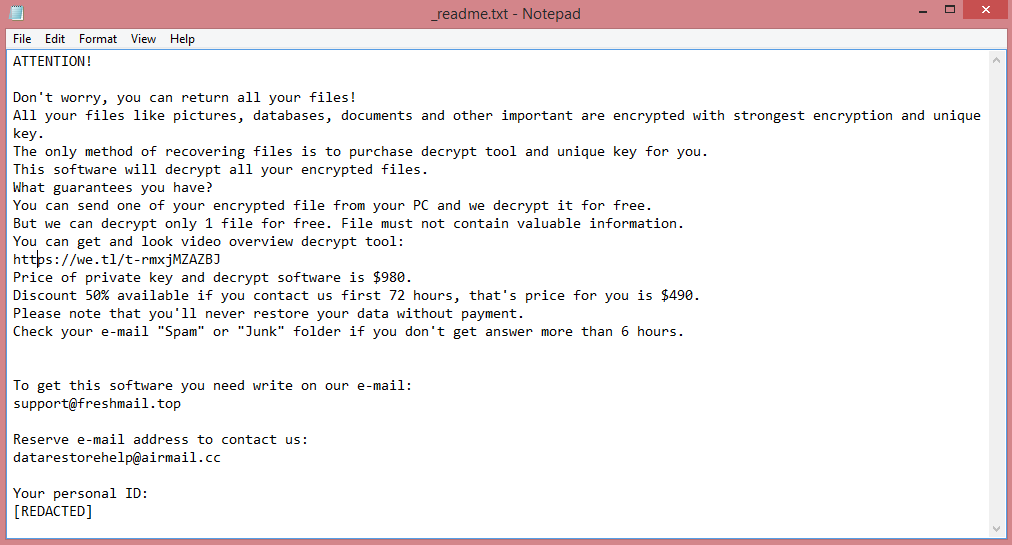
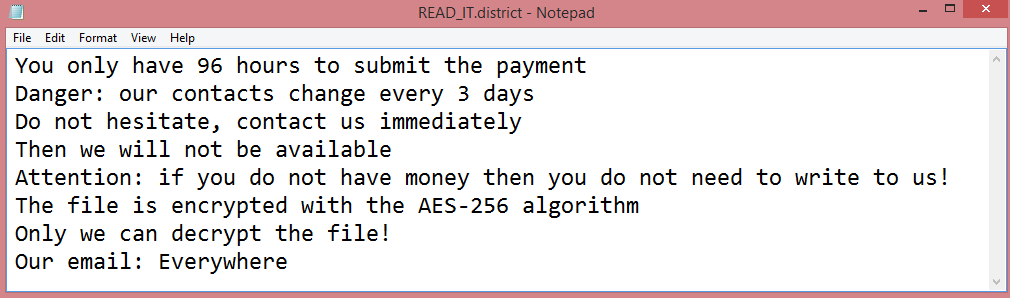
![Theva ransom note:
All your files have been encrypted due to a security problem with your PC.
If you want to restore them, write us to the e-mail: sql772@aol.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
FREE DECRYPTION AS GUARANTEE
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
and their total size must be less than 10Mb
How to obtain Bitcoins
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller
by payment method and price
https://localbitcoins.com/buy_bitcoins
Attention!
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 3 days - your key has been deleted and you cant decrypt your files
Your ID:
[REDACTED]
This is the end of the note. Below, you will find a guide explaining how to remove Theva ransomware.](https://www.computips.org/wp-content/uploads/2022/12/how-to-remove-theva-ransomware.png)
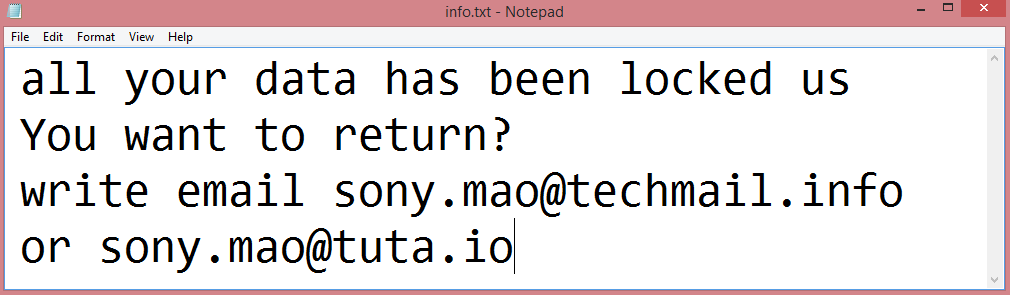
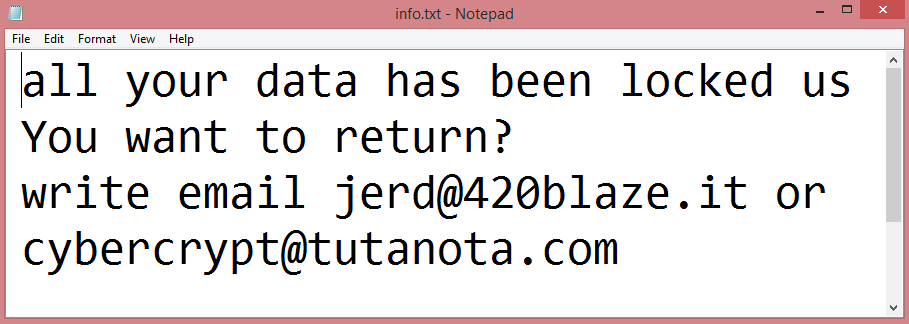
![Rans_recovery ransom note:
~~~ Hello! Your company has been hacked! ~~~
Your data are stolen and encrypted
What guarantees that we will not deceive you?
We are not a politically motivated group and we do not need anything other than your money.
If you pay, we will provide you the programs for decryption and we will delete your data.
Life is too short to be sad. Be not sad, money, it is only paper.
If we do not give you decrypters, or we do not delete your data after payment, then nobody will pay us in
the future.
Therefore to us our reputation is very important. We attack the companies worldwide and there is no
dissatisfied victim after payment.
You need to contact us by email rans_recovery@aol.com and decrypt some files for free
Your personal ID:
[REDACTED]
Provide your personal ID in the email
Warning! Do not DELETE or MODIFY any files, it can lead to recovery problems!
Warning! If you do not pay the ransom we will attack your company repeatedly again!
This is the end of the note. Below you will find a guide explaining how to remove Rans_recovery ransomware.](https://www.computips.org/wp-content/uploads/2022/12/how-to-remove-rans_recovery-ransomware.png)