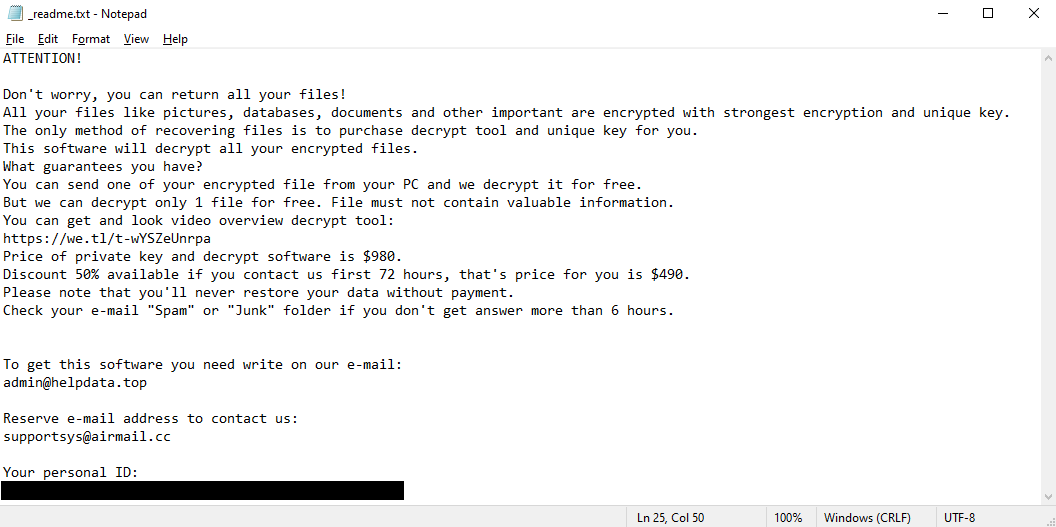
![IceFire ransom note:
********************Your network has been infected!!!********************
IMPORTANT : DO NOT DELETE THIS FILE UNTIL ALL YOUR DATA HAVE BEEN RECOVERED!!!
All your important files have been encrypted. Any attempts to restore your files with thrid -party software will be fatal for your files!
Restore your data possible only buying private key from us. We have also downloaded a lot of private data from your network. If you
do not contact us in a 5 days, we will post information about your breach on our public news webs.
You should get more information on our page, which is located in a Tor hidden network.
1.Download Tor browser - https://www.torproject.org/
2.Install Tor browser
3.Open link in Tor browser : kf6x3mjeqljqxjznaw65jixin7dpcunfxbbakwuitizytcpzn4iy5bad.onion
4. Follow the instructions on this page
Your account on our website
*******************************************************************************
username: [REDACTED]
password: [REDACTED]
ATTENTION:
1.Do not try to recover files yourself, this process can damage your data and recovery will become impossible.
2.Do not waste time trying to find the solution on the internet. The longer you wait, the higher will become the decryption key price.
3.Tor Browser may be blocked in your country or corporate network. Use Tor Browser over VPN.
This is the end of the ransom note. The guide below will explain how to remove IceFire ransomware.](https://www.computips.org/wp-content/uploads/2022/08/how-to-remove-icefire-ransomware.png)
What is IceFire ransomware
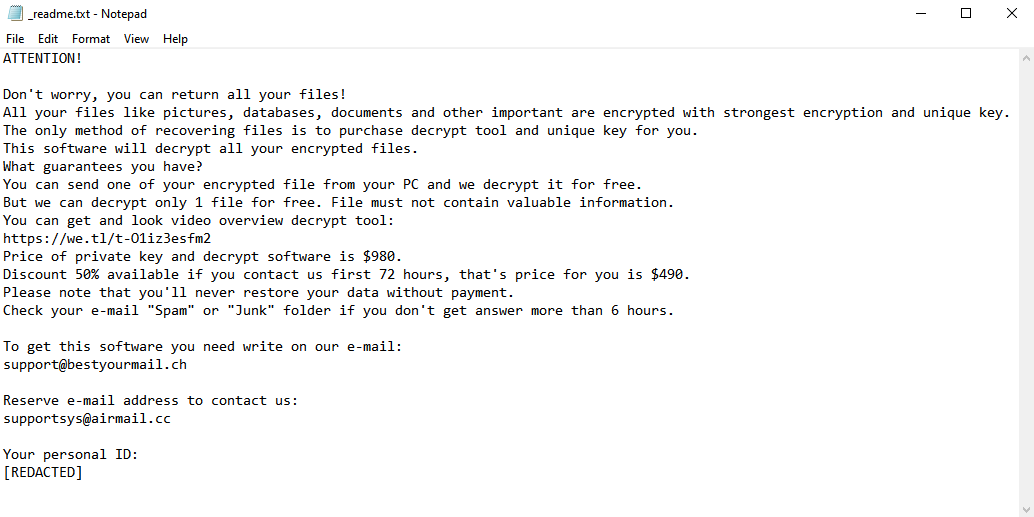
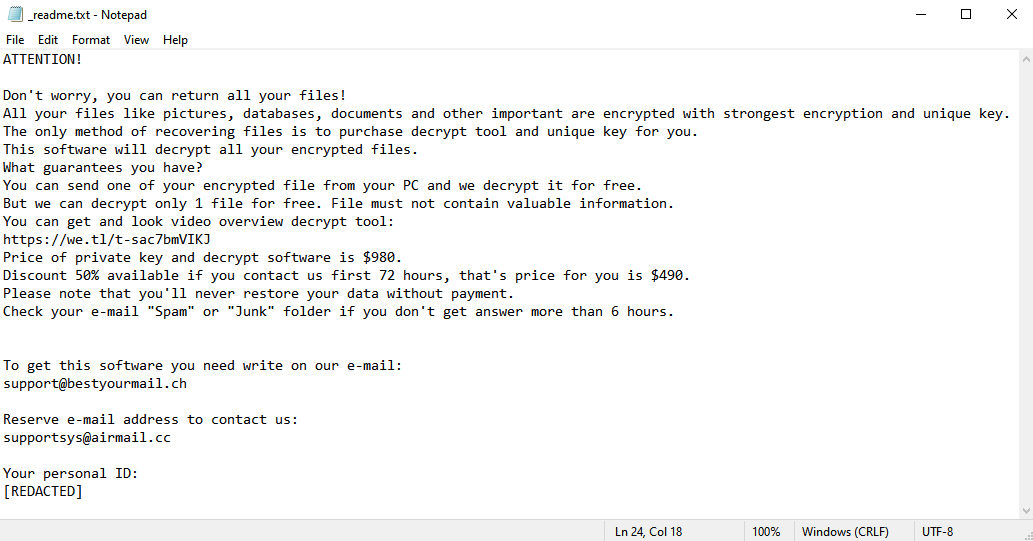
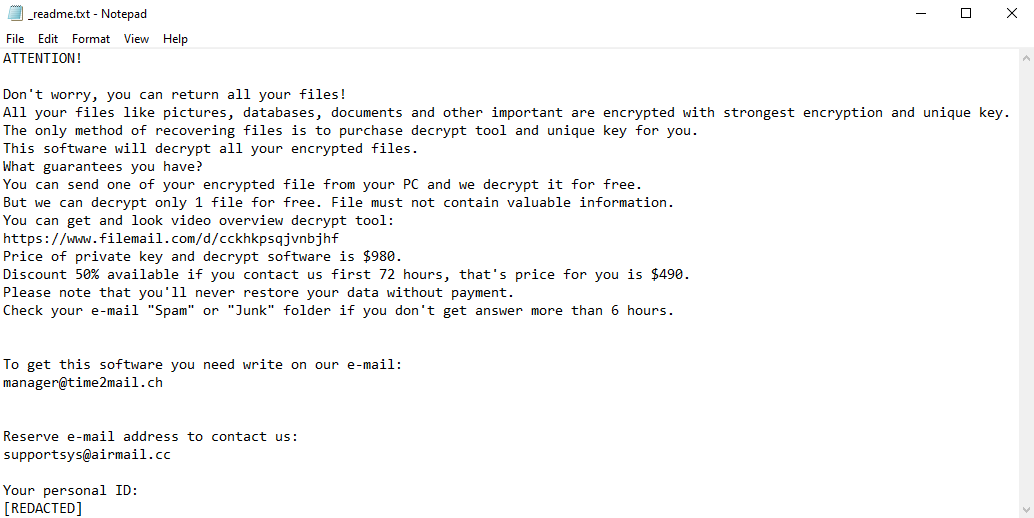
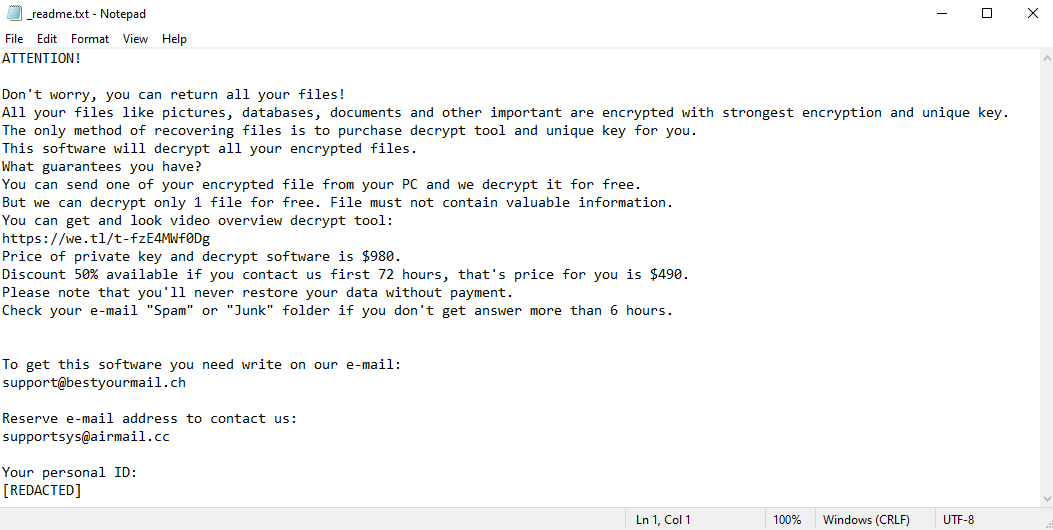
IceFire is a malicious program designed to infect computers and encrypt data on them. After this, the victim of the attack is prompted to pay a sum of money (often quite substantial) to the cybercriminal if they want to recover their valuable files. Due to this behavior, it is classified as ransomware. Unlike many ransomware programs, IceFire appears to be completely unique; it does not belong to any ransomware family. Unfortunately, this limits your options when it comes to recovering the files, but you will still be able to recover some files and remove IceFire without paying.
IceFire does a few more things beyond just encrypting the files. It gives all encrypted files the .iFire extension, to make the encrypted files easier for the victim to identify. And, of course, it leaves the ransom note (named “iFire-readme.txt”) with the instructions to follow. The image above contains full text of the note, but in short, the hackers simply tell the victims that they have to visit a Dark Web site for further instructions.
If you have been infected with IceFire, you will likely be unable to recover all of your data – unless you’ve kept backups – but you can still remove IceFire and recover some of the files without paying. Read this article to learn how to do it.
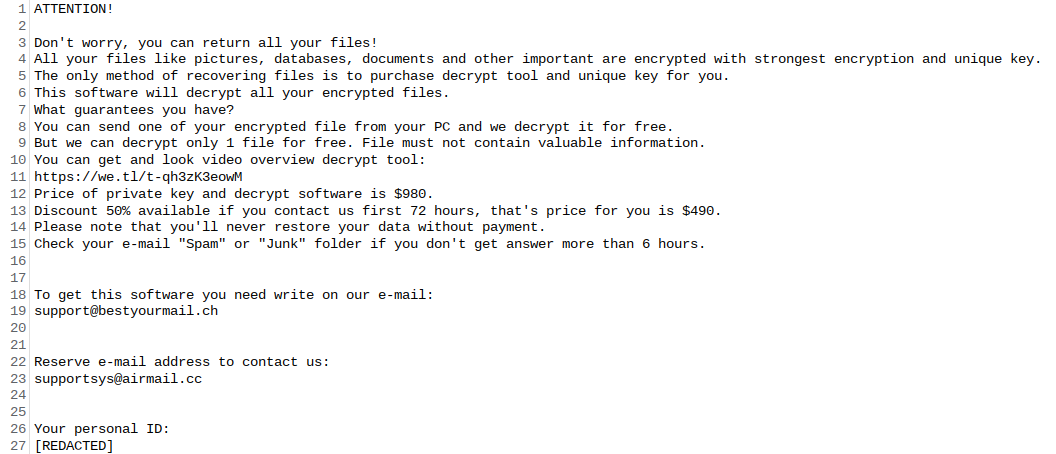
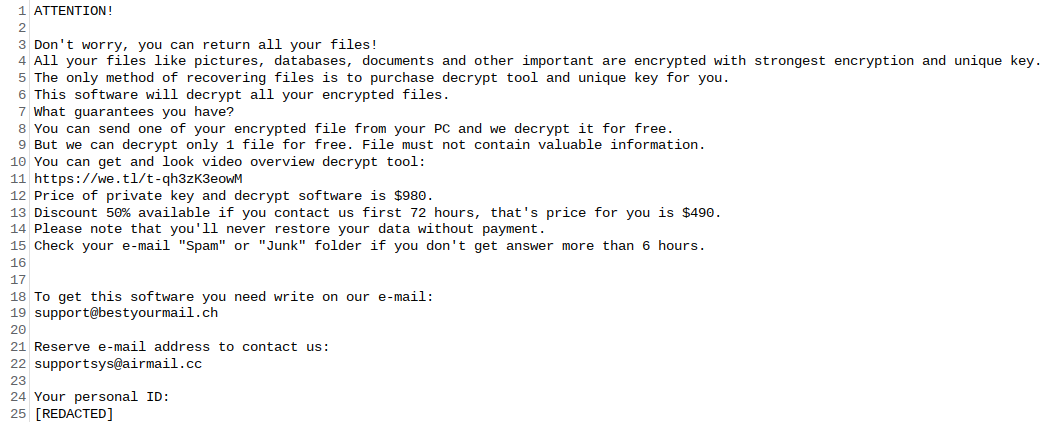
![Nqedrmt's ransom note:
ALL YOUR DOCUMENTS PHOTOS DATABASES AND OTHER IMPORTANT FILES HAVE BEEN ENCRYPTED!
====================================================================================================
Your files are NOT damaged! Your files are modified only. This modification is reversible.
The only 1 way to decrypt your files is to receive the private key and decryption program.
Any attempts to restore your files with the third party software will be fatal for your files!
====================================================================================================
To receive the private key and decryption program follow the instructions below:
1. Download 'Tor Browser' from https://www.torproject.org/ and install it.
2. In the 'Tor Browser' open your personal page here:
[REDACTED]
Note! This page is available via 'Tor Browser' only.
====================================================================================================
Also you can use temporary addresses on your personal page without using 'Tor Browser':
[REDACTED]
Note! There are temporary addresses! They will be available for a limited amount of time!](https://www.computips.org/wp-content/uploads/2022/06/how-to-remove-nqedrmt-ransomware-632x419.png)