What is Tywd ransomware?
Tywd is a recent variant of STOP/Djvu ransomware virus. All of these variants are nearly identical, since they are made using the same template. You can verify this by checking out Tycx, another recent STOP/Djvu virus.
But what does Tywd actually do? Well, as a ransomware virus, its goal is to encrypt the files on the infected computer, which makes them inaccessible (impossible to open and edit). That, in turn, is done so that the hacker responsible for the virus could demand money to restore these files (decrypt them).
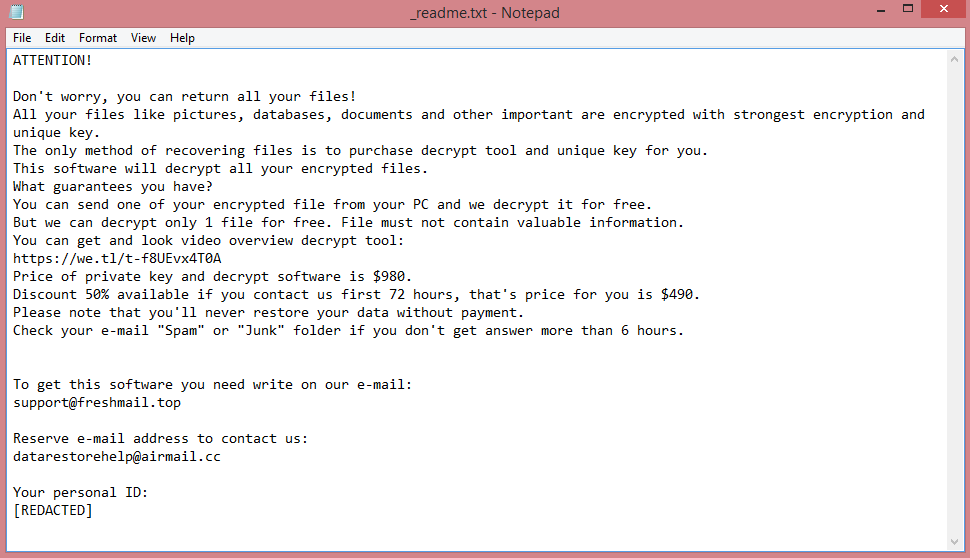
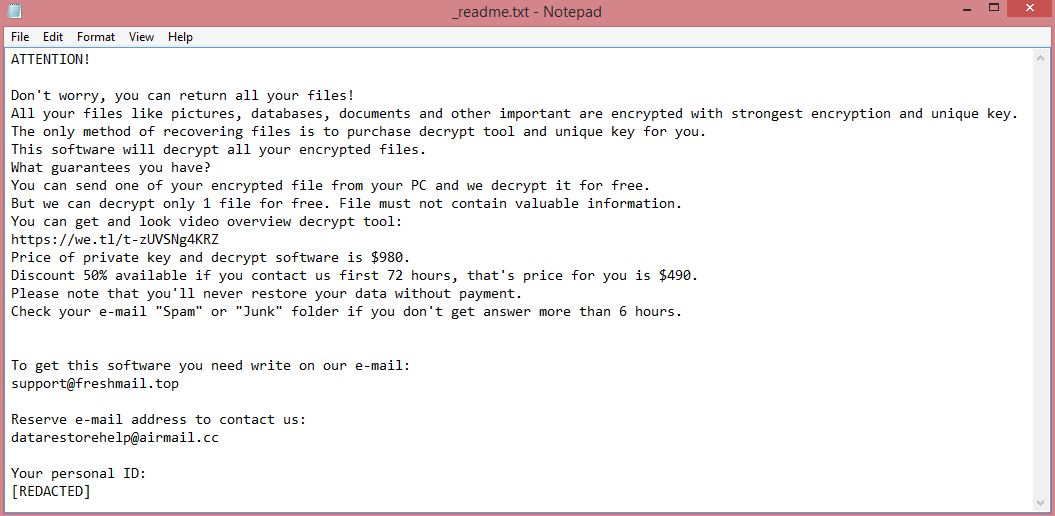
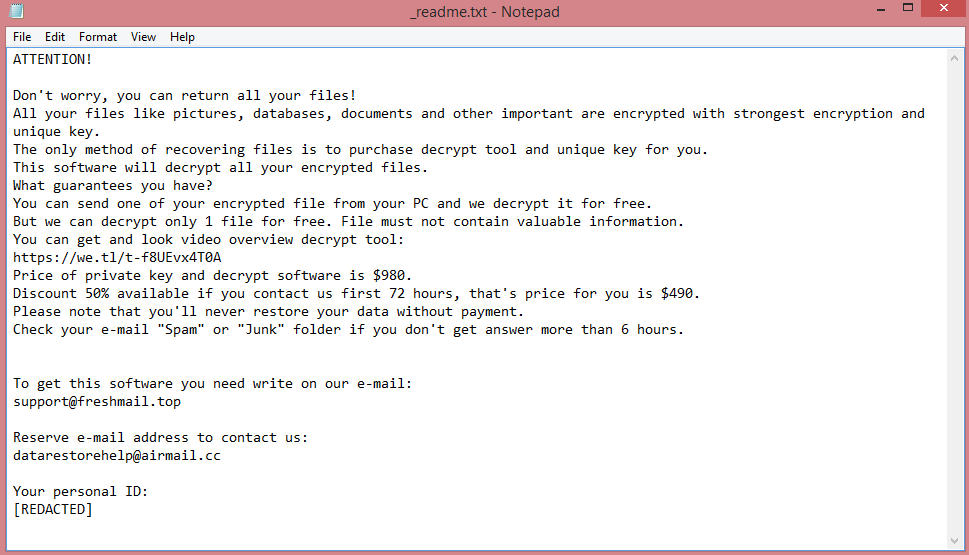
This, essentially, is all Tywd does. It encrypts the victim’s files, gives them .tywd file extension, and creates a ransom note to let the victim know how to contact the hacker and how much money he wants. This note can be read on the image above; however, the paragraph below provides a brief summary.
Tywd’s ransom note, “_readme.txt”, is identical to the notes left by other STOP/Djvu viruses. It provides the victim with two e-mail addresses for contacting the hackers and demands $980 in ransom. Alternatively, the victim can pay $490, provided they message the hackers within 3 days of infection.
Still, that is quite expensive. If you’re not willing to pay, or can’t afford to, there are alternative options. The guide below will explain how to remove Tywd ransomware and decrypt .tywd files without paying the criminals.