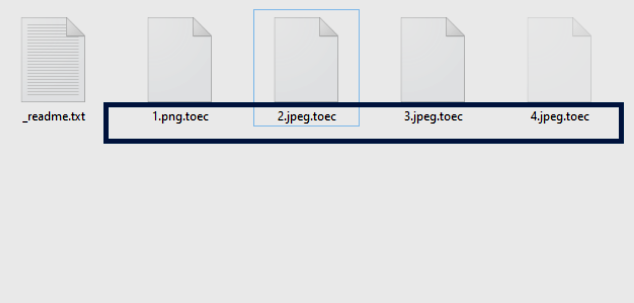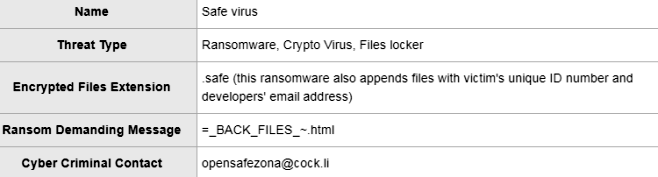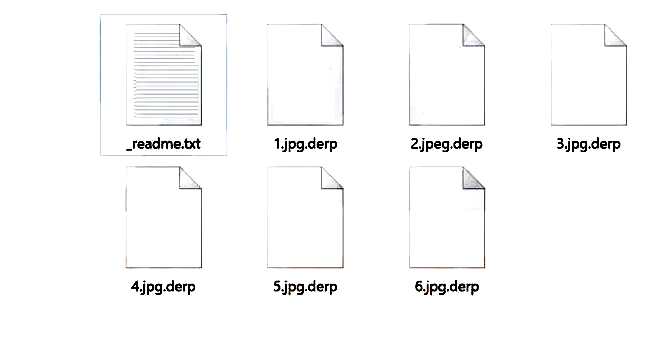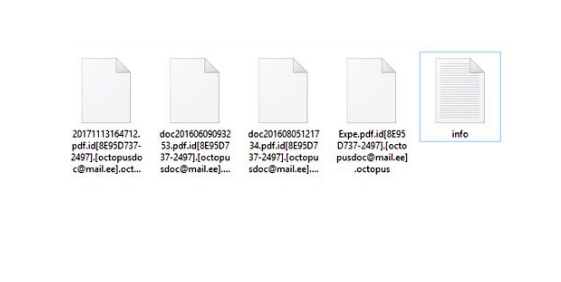
What is Octopus ransomware
Octopus ransomware is a computer pest that is able to encrypt all your files. Unlike other types of viruses, it focuses only on files (images, audio, video), it does not touch the entire system as a whole, but it infects files so that you can never use them again while Octopus ransomware is on your computer. Developers will send users a fake hint on how to recover files. To do this, they must contact the developers via octopusdoc@airmail.cc or octopusdoc@mail.ee email address. The price of the decryption tool depends on how quickly the victims contact the developers. Not at once and far from all users understand that these are tricks for extorting money. Our article was created specifically to protect you from fraud. Read on to find out how to safely remove Octopus ransomware from your computer.