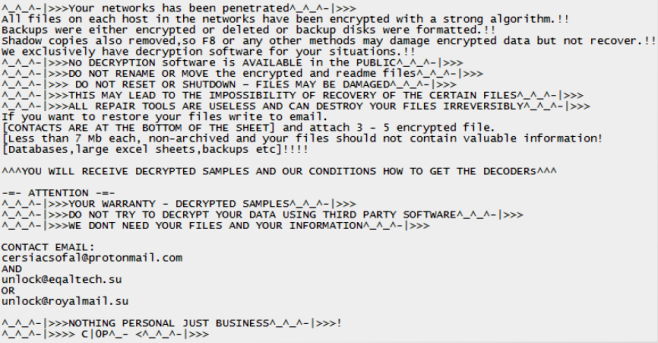
What Is Cephalo?
Cephalo is a ransomware type of malware that will change your computer system without permission and leads to serious problems. Its main goal is to trick your money by stealing your files and encrypting them. When Cephalo locks your files, they become useless. To get the money, Cephalo will display a ransom request message on your desktop to describe the decryption method and payment details. When you click on any of your locked files, Cephalo will display an error message and ask you to buy a decryption key to unlock your data. We want to warn you that the only way to get rid of this virus and its tricks is to remove it. Our article will help you with this.



![How to remove [Restdoc@protonmail.com].ZOH Ransomware](https://www.computips.org/wp-content/uploads/2017/12/arena-ransomware.png)