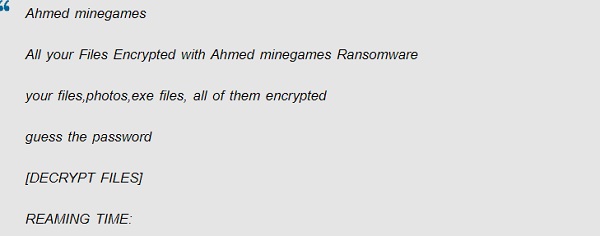
What is Lalaland ransomware?
Lalaland is a dangerous virus that has the features of a computer ransomware. Systems infected with this application are subject to data loss by encrypting files with the infected algorithm. Lalaland ransomware blocks access to files by adding the extension “.lalaland” and issues ransom demands for decryption tools so that you can use files again.