What is INT ransomware?
INT ransomware is a new strain of the Makop virus. As a ransomware program, it encrypts the files of its victims’ computers in order to demand payment for their decryption. However, these programs tend to do more than that; for example leaving a ransom note is pretty essential to this criminal operation.
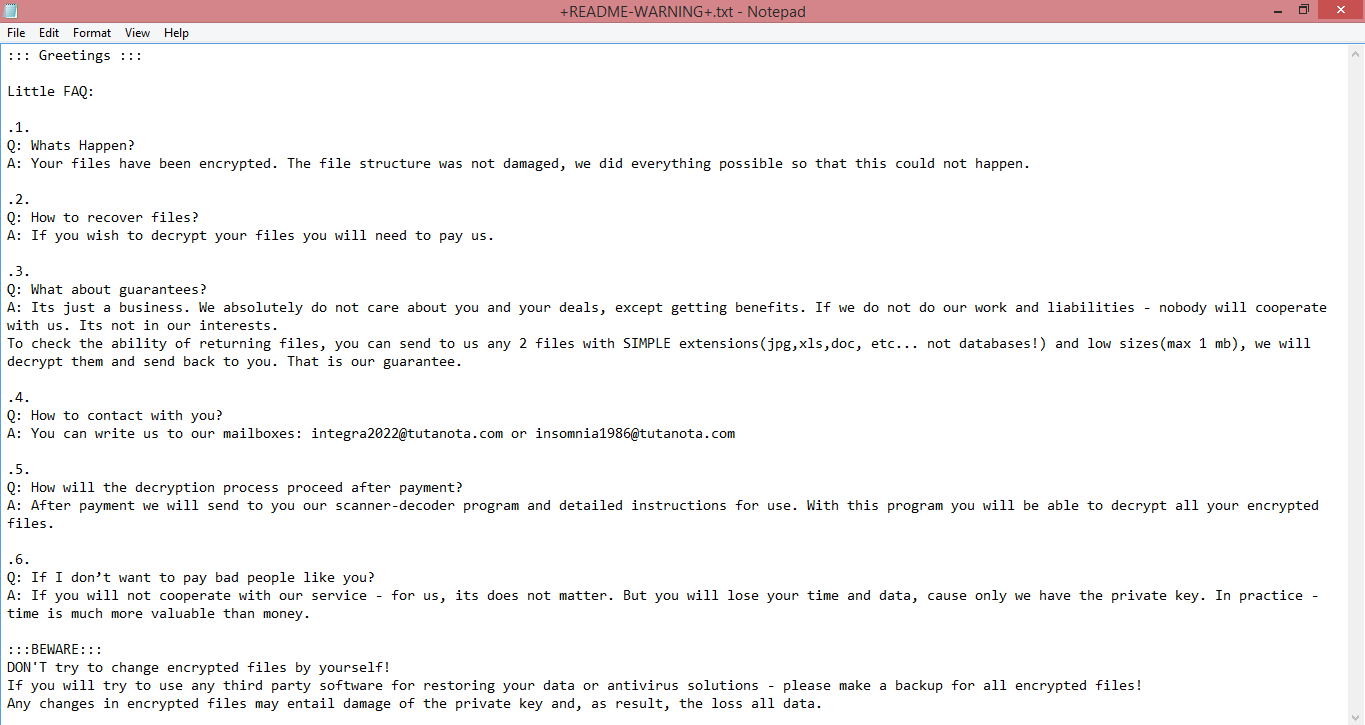
INT is not an exception to this rule; it leaves a simple, if somewhat lengthy, note called “+README-WARNING+.txt”. You may read the full text of the note on the image above, if you wish. To recap, the hackers simply tell the victim to contact them, and do not mention any specific sum of money.
Files encrypted by INT have their name changed. The virus adds an ID, one of the hackers’ e-mails, and finally the .INT file extension to the names. This is how the virus got its name.
Paying these hackers is generally a bad idea. You will, obviously, lose money, but also open yourself to more attacks in the future, and might not even get your files back at all. So we’ve prepared a guide explaining other ways to remove INT ransomware and decrypt .INT files.