What is Hvzgbo ransomware?
Hvzgbo is a new version of Snatch ransomware, one that became active only recently. Older versions of this ransomware include Gqlmcwnhh and Bkqfmsahpt.
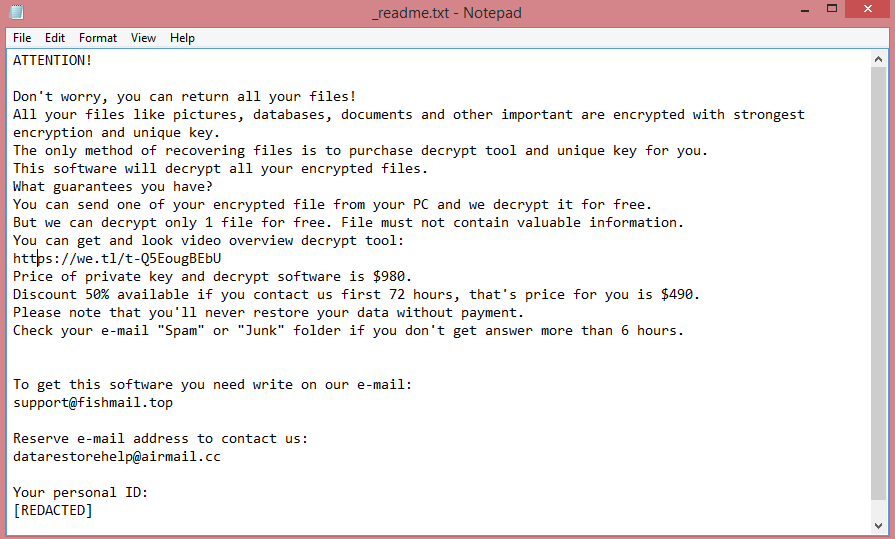
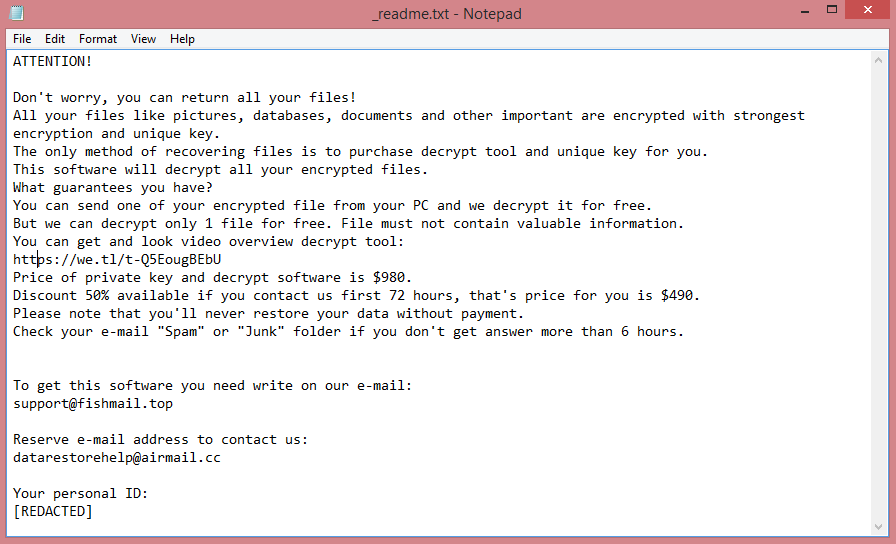
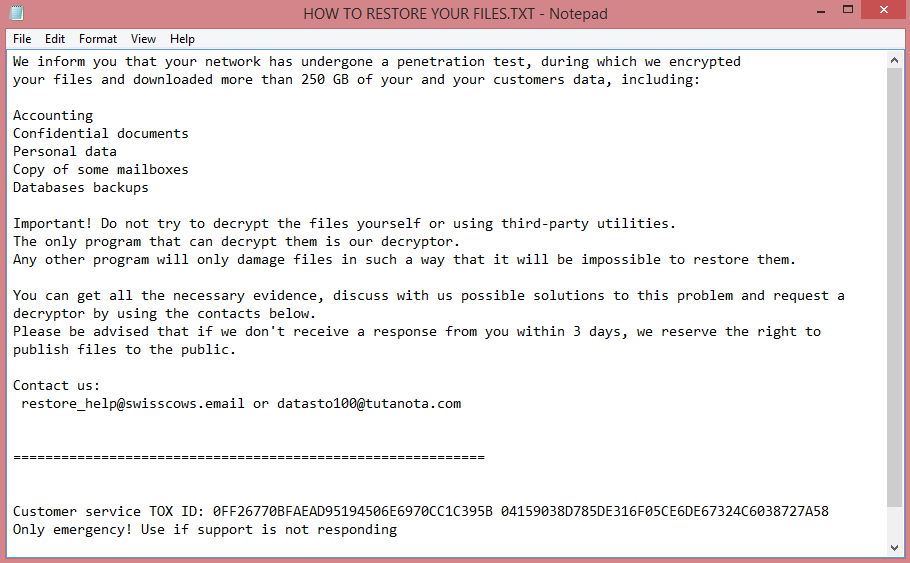
Ransomware-type viruses all behave according to a specific algorithm. The first step is to encrypt the files on the victim’s computer. The second step is to rename them (in this case, add .hvzgbo file extension). The third and the final step is to create a ransom note. We will elaborate on Hvzgbo’s note in the next paragraph. You can also read its text on the image above.
The note left by Hvzgbo is called “HOW TO RESTORE YOUR FILES.TXT” and indicates that Hvzgbo is targeting companies and not individuals, which is typical for Snatch ransomware. Although it is unlikely that the virus will target a normal person’s computer, the risk is not zero.
So, what should you do in this case? You may try to contact the hackers but, since you’re a low-value target, they will likely ignore you. This is why you should read the guide below; it offers several other methods to remove Hvzgbo ransomware and decrypt .hvzgbo files.