How to remove MILIHPEN ransomware
What is MILIHPEN ransomware
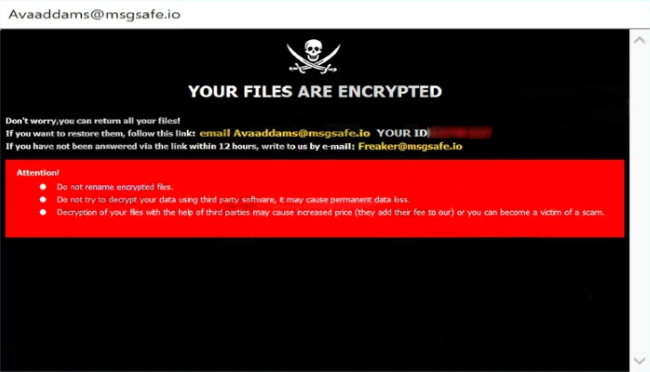
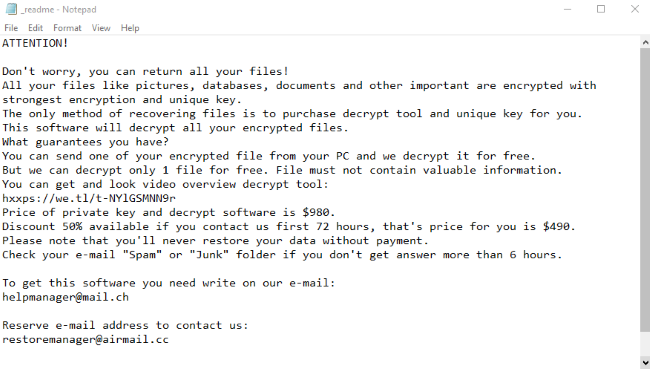
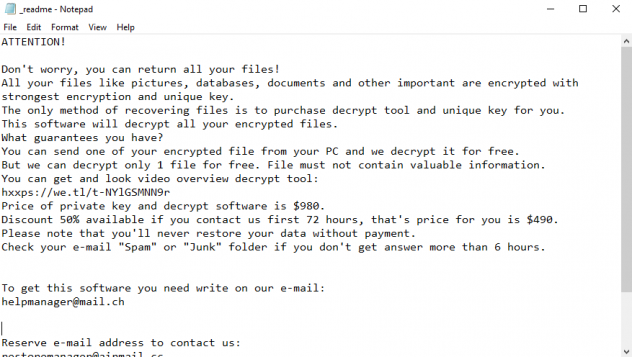
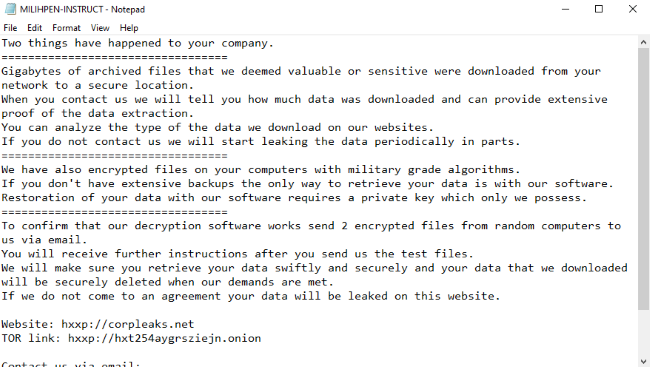
MILIHPEN is a new virus, the function of which is restricting an access to data. We characterize this virus as a ransomware. In the most cases MILIHPEN ransomware spreads by the means of fake installers. Criminals often promote them as free or cracked software and distribute them through file sharing services and torrent trackers. However, criminals can also use botnets and remote access terminals to infect devices and even networks. When MILIHPEN virus gets into the system, it modifies registry folder and system processes. Then, by the means of these modifications, MILIHPEN encrypts the data. As the result, your files get new “.MILIHPEN” extensions. At the same time MILIHPEN drops the ransom note called “MILIHPEN-INSTRUCT.txt”. Don’t try to decrypt your data and to remove MILIHPEN ransomware by yourself. Without a guide, you can easily damage your files without any possibility to restore them. And if you need one, read our MILIHPEN removal guide!