What is Kifr ransomware?
Kifr is a newly-discovered virus that infects computers through suspicious e-mail attachments, untrustworthy websites (especially 18+ websites), phishing links, and other means. Once it has infected a computer, Kifr virus encrypts all files it can find. These encrypted files can’t be opened. To reverse the procedure, Kifr demands money.
Kifr is very similar to other viruses that were released recently, like Kitz and Kiwm. That is not a coincidence; all of them belong to the STOP/Djvu ransomware family.
Despite this similarity, you can easily identify Kifr virus. It renames the files after encrypting them; all encrypted files have .kifr extension. Though, considering you’re reading this article, you already know that you’re dealing with Kifr ransomware.
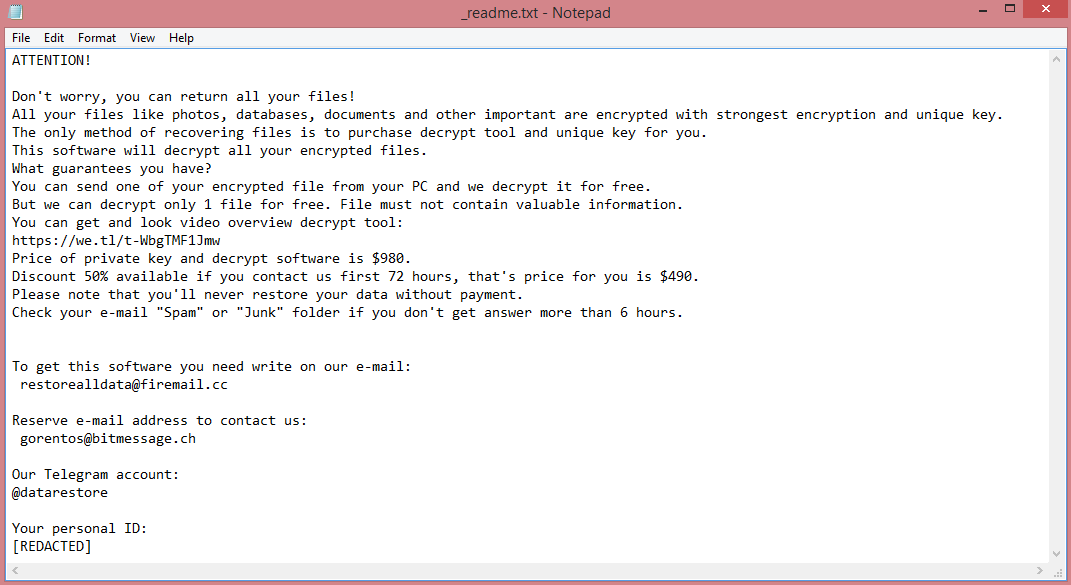
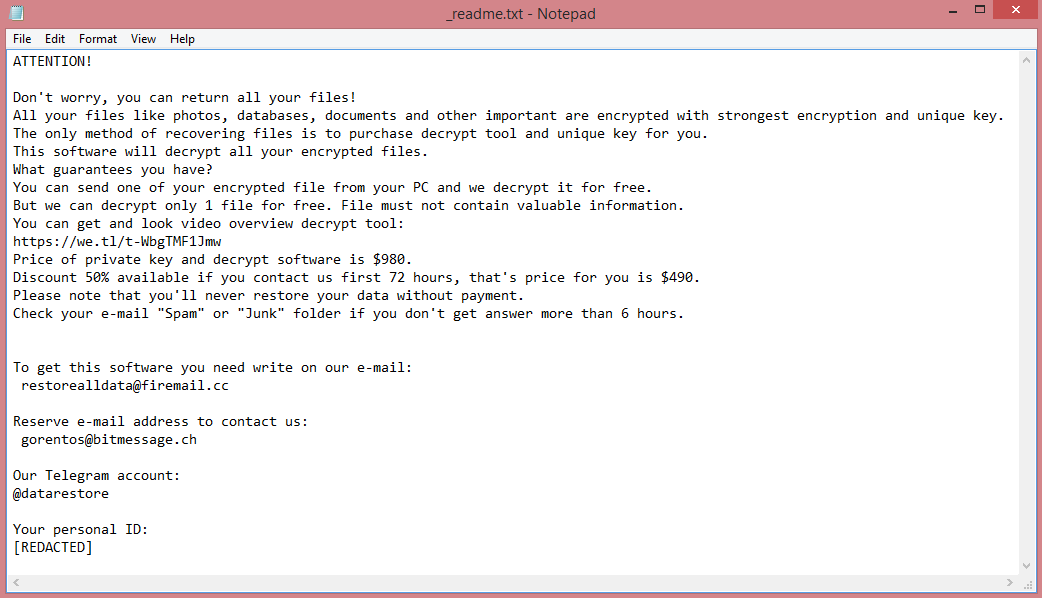
So, what should you do about it? In the ransom note left by the virus (“_readme.txt”, see image above), the hackers suggest that you pay them $980 (or $490, but that’s still a lot). Not a very appealing prospect.
But there’s another way; several of them, in fact. The guide below contains methods that you can employ to remove Kifr ransomware and decrypt .kifr files without giving a single cent to the damned criminals.
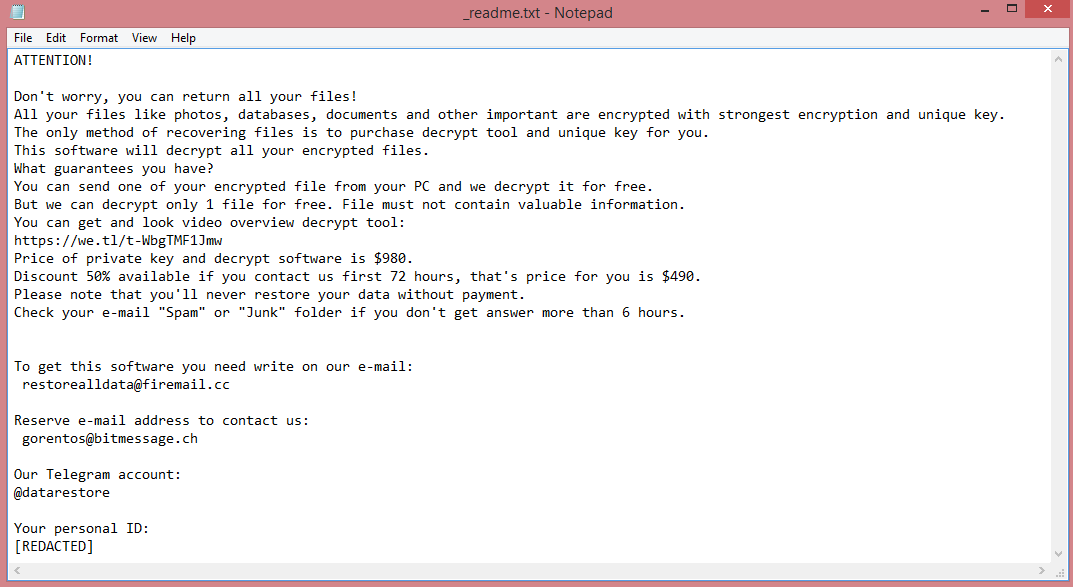
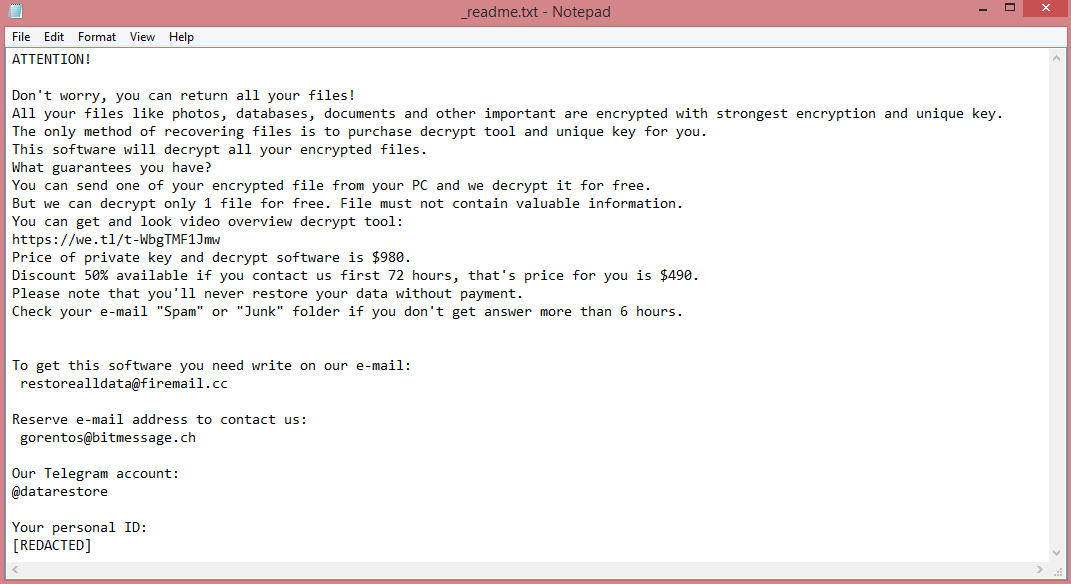
![Proton ransom note:
~~~ Proton ~~~
What happened?
We encrypted and stolen all of your files.
We use AES and ECC algorithms.
Nobody can recover your files without our decryption service.
How to recover?
We are not a politically motivated group and we want nothing more than money.
If you pay, we will provide you with decryption software and destroy the stolen data.
What guarantees?
You can send us an unimportant file less than 1 MG, We decrypt it as guarantee.
If we do not send you the decryption software or delete stolen data, no one will pay us in future so we will keep our promise.
How to contact us?
Our Telegram ID: @ransom70
Our email address: Kigatsu@tutanota.com
In case of no answer within 24 hours, contact to this email: Kigatsu@mailo.com
Write your personal ID in the subject of the email.
Your personal ID: [REDACTED]
Warnings!
- Do not go to recovery companies, they are just middlemen who will make money off you and cheat you.
They secretly negotiate with us, buy decryption software and will sell it to you many times more expensive or they will simply scam you.
- Do not hesitate for a long time. The faster you pay, the lower the price.
- Do not delete or modify encrypted files, it will lead to problems with decryption of files.
This is the end of the note. Below you will find a guide explaining how to remove Proton ransomware and decrypt .kigatsu files.](https://www.computips.org/wp-content/uploads/2023/04/how-to-remove-proton-ransomware.png)
![BlackByteNT ransom note:
BLACKBYTE NT
All your files have been encrypted, your confidential data has been stolen,
in order to decrypt files and avoid leakage, you must follow our steps.
1) Download and install TOR Browser from this site: https://torproject.org/
2) Paste the URL in TOR Browser and you will be redirected to our chat with all information that you need.
3) If you read this message thats means your files already for sell in our Auction.
Everyday of delaying will cause higer price. after 4 days if you wont connect us,
We will remove your chat access and you will lose your chance to get decrypted
Warning! Communication with us occurs only through this link, or through our mail on our Auction.
We also strongly DO NOT recommend using third-party tools to decrypt files,
as this will simply kill them completely without the possibility of recovery.
I repeat, in this case, no one can help you!
Your URL: [REDACTED]
Your Key to access the chat: [REDACTED]
Find our Auction here (TOR Browser): [REDACTED]
This is the end of the note. Below you will find a guide explaining how to remove BlackByteNT ransomware and decrypt .blackbytent files.](https://www.computips.org/wp-content/uploads/2023/04/how-to-remove-blackbytent-ransomware.png)
![WiKoN ransom note:
ATTENTION!
All your files have been encrypted
And their decryption will cost you 0.05 bitcoin.
To start the decryption process follow the steps below
Step 1) Make sure you send 0.05 bitcoin to this wallet:
bc1q0u997r79ylv9hrc7zcth0mvr3mjua6324hxnkc
Step 2) Contact me at this email address: wikon@tuta.io
With this Subject: [REDACTED]
After the payment has been confirmed,
you will receive the decryptor and the keys for decryption!
Other information:
If you don't own bitcoin, you can buy it here very easily
www.coinmama.com
www.bitpanda.com
www.localbitcoins.com
www.paxful.com
You can find a larger list here:
https://bitcoin.org/en/exchanges
If the payment is not made in 2 days, I will consider that you do not want to decrypt your files,
and therefore the keys generated for your PC will be permanently.deleted.
This is the end of the note. Below you will find a guide explaining how to remove WiKoN ransomware and decrypt .WiKoN files.](https://www.computips.org/wp-content/uploads/2023/04/how-to-remove-wikon-ransomware.png)