The MSDT exploit is a dangerous vulnerability in Microsoft Windows that allows hackers to perform “remote code execution”. In layman’s terms – this means that the MSDT exploit allows hackers to do anything they want with your computer. Maybe they’ll mine cryptocurrency, maybe they’ll steal your accounts, maybe they’ll install a ransomware program… anything is possible. It affects all modern Windows versions – Windows 7 and the newer versions are all vulnerable.
The exploit allows hackers to corrupt .docx and .rtf files (text documents), as well as Windows shortcuts, in such a way that it allows them to control your computer. This is done through a vulnerability in Microsoft Support Diagnostic Tool (MSDT), which is why it is called the MSDT exploit. In case of .docx files and shortcuts, the hacker needs the victim to open the file. However, .rtf files are even more dangerous – simply clicking on the file once, without opening it, is enough to be hacked.
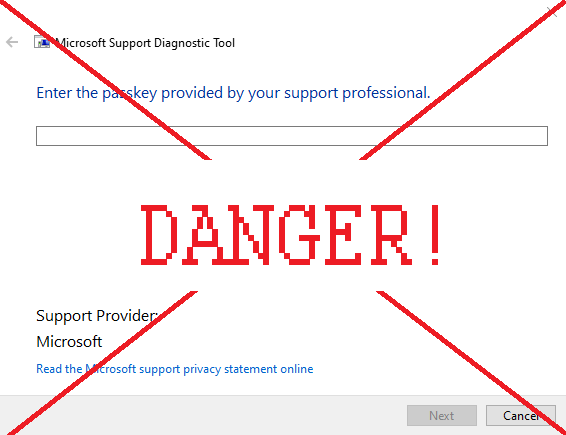
Note that Microsoft Support Diagnostic Tool by itself is not dangerous. However, you should never see the window on the image above unless you’re interacting with Microsoft Support. If you saw this window randomly appear, or appear after you’ve opened a file – you’ve been infected.
This vulnerability is also known as Follina, and in the cybersecurity world, as CVE-2022-30190 and Mesdetty. So if you’ve heard one of these names – these are all just different names for this vulnerability.
Although this is a very serious flaw in Windows’s security, it can be easily fixed. This article will teach you how to fix MSDT exploit so you can be safe from the hackers trying to use this vulnerability.
Install Advanced System Repair Pro
You can use Advanced System Repair Pro to fix your PC issues, clean it up and remove malware.
How to fix the MSDT exploit
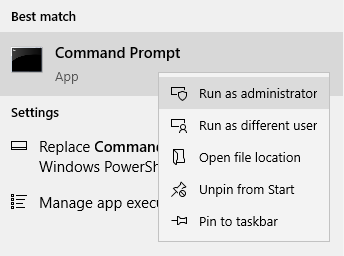
First, open the Start menu and type in “command prompt” or “cmd”. This will perform a search for the program with this name. Right-click on the first search result and select Run as administrator.
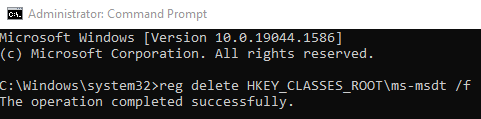
A black window should appear. Copy this line:
reg delete HKEY_CLASSES_ROOT\ms-msdt /f
Then, right-click on the black window to paste it. Note that Ctrl+V will not work. Once you’ve pasted the line, press Enter.
After this, you should see a new line of text appear. If the line says “The operation completed successfully”, then you’ve done everything right and are now safe from the vulnerability. See the image above for reference.
However, if the line says “ERROR: Access is denied”, then you’ve made a mistake. Specifically, you ran Command Prompt as a regular user, not as an administrator. Re-do the steps, running Command Prompt as an administrator this time.
What to do if you’re already hacked
As we already mentioned, the symptoms of being hacked using this vulnerability is the Microsoft Diagnostic Support Tool opening randomly or after opening a file. Another bad sign is seeing a window titled “Program Compatibility Troubleshooter” after opening a text document – this too means you’ve been hacked.
If this happened to you, this means a hacker has done something to your computer. It is impossible to say what has been done. To detect and remove any malicious programs the hacker might’ve installed, you should install an antivirus.
Alternative antiviruses:
Malwarebytes (Windows)
However, this is not enough. You should also change all your passwords, because the hacker might’ve learned them. While you’re at it, enable two-factor authentication on all websites that support it, assuming you haven’t already. If you performed any online purchases from the infected computer, or used online banking, you should also immediately freeze all cards that could potentially be affected, then contact your bank(s).