What is ZFX ransomware?
![ZFX ransom note:
::: Hey :::
Small FAQ:
.1.
Q: What's going on?
A: Your files have been encrypted. The file structure was not affected, we did our best to prevent this from happening.
.2.
Q: How to recover files?
A: If you want to decrypt your files, you will need to pay us.
.3.
Q: What about guarantees?
A: It's just business. We are absolutely not interested in you and your transactions, except for profit. If we do not fulfill our work and obligations, no one will cooperate with us. It's not in our interest.
To check the possibility of returning files, you can send us any 2 files with SIMPLE extensions (jpg, xls, doc, etc... not databases!) and small sizes (max 1 mb), we will decrypt them and send them back to you. This is our
guarantee.
.4.
Q: How to contact you?
A: You can write to us at our mailboxes: CryptedData@tfwno.gf
.5.
Q: How will the decryption process take place after payment?
A: After payment, we will send you our scanner-decoder program and detailed instructions for use. With this program you will be able to decrypt all your encrypted files.
.6.
Q: If I don't want to pay bad people like you?
A: If you do not cooperate with our service - it does not matter to us. But you will lose your time and data because only we have the private key. In practice, time is much more valuable than money.
:::BEWARE:::
DO NOT try to modify encrypted files yourself!
If you try to use third party software to recover your data or antivirus solutions - back up all encrypted files!
Any changes to the encrypted files may result in damage to the private key and, as a result, the loss of all data.
Note:
::::::IF WE HAVE NOT RESPONSE YOU BY MAIL WITHIN 24 HOURS::::::
Spare contact for communication:
If we have not answered your email within 24 hours, you can contact us via the free messenger qTox
Download from the link https://tox.chat/download.html
Next go qTox 64-bit
after downloading the program, install it and go through a short registration.
Our Tox ID
[REDACTED]
This is the end of the note. Below you will find a guide explaining how to remove ZFX ransomware.](https://www.computips.org/wp-content/uploads/2023/01/how-to-remove-zfx-ransomware.png)
ZFX is a new ransomware program; this means it’s a virus that encrypts the victims’ files and holds them ransom.
The virus performs several actions. The most important one is file encryption, but it also renames the files (adding information to the filenames and giving them .ZFX file extension), changes the desktop wallpaper (for visibility purposes), and creates a ransom note named “+README-WARNING+.txt”.
The note, which can be read in full on the image above, contains a rather lengthy FAQ as well as some contact information. Despite this, it does not mention how much money hackers want for decryption. Perhaps the hackers intend to negotiate with each victim, or don’t want to scare people away by mentioning their high prices.
Either way, you should not pay these criminals as it is not a reliable procedure. They can take the payment and disappear without decrypting your data, or they can choose to attack you again afterwards. Instead, perhaps you should learn about other ways to remove ZFX ransomware and decrypt .ZFX files. The guide below contains several such methods.
How to Remove ZFX Ransomware
If you have working backups of your encrypted files or you are not going to try and recover lost files, then scan your computer with one or several antivirus and anti-malware programs or reinstall the operating system altogether.
Alternative antiviruses:
Malwarebytes (Windows)
How to Recover Files Encrypted by ZFX Ransomware
If you want to recover files encrypted by ransomware you can either try to decrypt them or use methods of file recovery.
Ways to decrypt the files:
- Contact the ransomware authors, pay the ransom and possibly get the decryptor from them. This is not reliable: they might not send you the decryptor at all, or it might be poorly done and fail to decrypt your files.
- Wait for security researchers to find some vulnerability in the ransomware that would allow you to decrypt files without paying. This turn of events is possible but not very probable: out of thousands of known ransomware variants only dozens were found to be decryptable for free. You can visit NoMoreRansom site from time to time to see if free decryptor for ZFX exists.
- Use paid services for decryption.
Other ways to recover encrypted files:
- Restore from backup. If you make regular backups to a separate device and check from time to time that those are in working order and files can be successfully restored – well, you probably won’t have any problems getting back your files. Just scan your computer with a couple of AVs and anti-malware programs or reinstall the operating system, and then restore from backup.
- Recover some files from cloud storage (DropBox, Google Drive, OneDrive, etc.) if you have one connected. Even if encrypted files were already synced to the cloud, a lot of cloud services keep old versions of altered files for some time (usually 30 days).
- Recover Shadow Volume Copies of your files if those are available – ransomware usually tries to delete them too. Volume Shadow Copy Service (VSS) is a Windows technology that periodically creates snapshots of your files and allows you to roll back changes made on those files or recover deleted files. VSS is enabled together with System Restore: it’s turned on by default on Windows XP to Windows 8 and disabled by default on Windows 10.
- Use file recovery software. This probably won’t work for Solid State Drives (SSD – a newer, faster and more expensive type of data-storage devices) but is worth a try if you store your data on a Hard Disc Drive (HDD – an older type of storage device which generally has more capacity). When you delete a file from your computer – and I mean completely delete: use Shift + Del or empty the Recycle Bin – on an SSD, it gets wiped from the drive right away. On an HDD however, it rather gets marked as deleted, and the space it occupies on a hard drive – as available for writing, but the data is still there and is usually recoverable by special software. However, the more you use the computer, especially if you do something that writes new data on the hard drive, the more chance that your deleted file gets overwritten and will be gone for good. That is why, in this guide we will try to recover deleted files (as you remember, ransomware creates an encrypted copy of a file and deletes the original file) without installing anything on a disk. Just know that this still might not be enough to successfully recover your files – after all, when ransomware creates encrypted files it writes new information on a disk, possibly on top of files it just deleted. This actually depends on how much free space is there on your hard drive: the more free space, the less chance that new data will overwrite the old data.
- This might void your warranty.
- It’s harder to do with laptops, and you’ll need a special case (disk enclosure) to put a hard drive in before connecting it to another machine.
- It is possible to infect the other computer if you open a file from the infected drive before scanning the drive with AVs and removing all found malware; or if all AVs fail to find and delete the malware.
- Restart the computer.
- Once you see a boot screen tap F8 key continuously until a list of options appears.
- Using arrow keys, select Safe Mode with Networking.
- Press Enter.
- Hold down Windows key
 and hit X key.
and hit X key. - Select Shut down or sign out.
- Press Shift key and click on Restart.
- When asked to choose an option, click on Advanced options => Startup Settings.
- Click Restart in the bottom right corner.
- After Windows reboots and offers you a list of options, press F5 to select Enable Safe Mode with Networking.
- Launch Shadow Explorer.
- On the top left part of the window you can select a disk (C:\, D:\, etc.) and a date when a snapshot of files was taken.
- To recover a file or a folder right-click on it and select Export’.
- Choose where do you want to put the files.
Going further, we need to 1) stop ransomware from encrypting files that we recover, if malware is still active; 2) try not to overwrite files deleted by ransomware. The best way to do it is disconnect your hard drive and connect it to another computer. You will be able to browse all your folders, scan them with antivirus programs, use file recovery software or restore data from Shadow Volume Copies. Although it is better to download all tools you’ll need beforehand and disconnect the computer from the Internet before connecting the infected hard drive, just to be safe.
Disadvantages of this method:
Another, easier, way is to load into Safe Mode and do all file recovery measures from there. However, that will mean using the hard drive and potentially overwriting some data. In this case it’s preferable to use only portable versions of recovery software (the ones that don’t require installation), download them onto an external device, and save any recovered files onto an external device too (external hard drive, thumb drive, CD, DVD, etc.).
Boot Into Safe Mode:
 Windows XP,
Windows XP,  Windows Vista,
Windows Vista,  Windows 7:
Windows 7:
 Windows 8,
Windows 8,  Windows 8.1,
Windows 8.1,  Windows 10:
Windows 10:
Back up Your Encrypted Files
It is alwayse advisable to create a copy of the encrypted files and put it away. That might help you if free ransomware decryptor becomes available in the future, or if you decide to pay and get the decryptor but something goes wrong and files get irreparably damaged in the process of decryption.
Use File Recovery Tools to Recover Files
Screenshot:
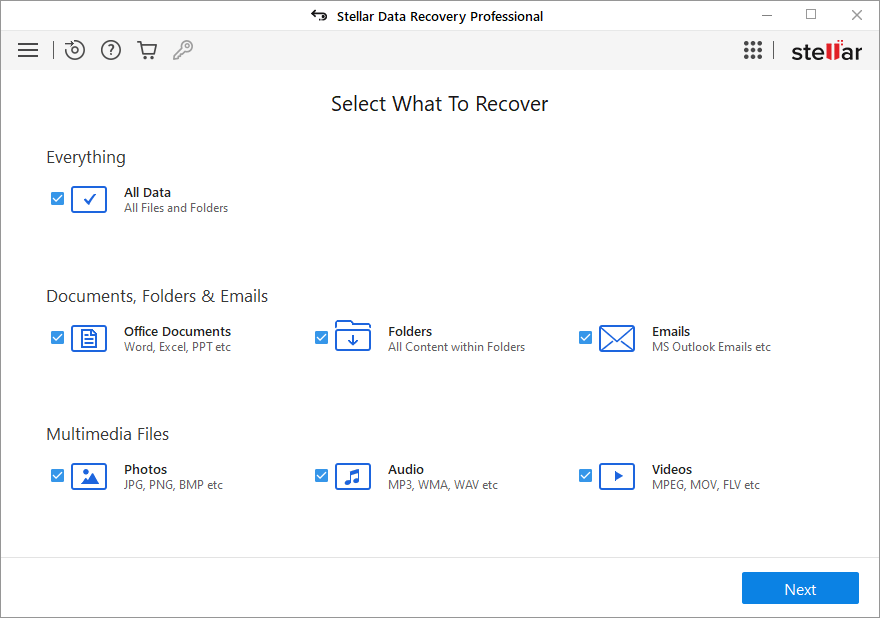
About Stellar Data Recovery
R-Undelete
How to recover deleted files with R-Undelete
Recover Encrypted Files From Shadow Copies.
The easiest way to access Shadow Volume Copies is by using a free tool called Shadow Explorer. Just download the latest version and install it (or download the portable version).
How to Prevent A Ransomware Infection In the Future
Attachments in spam emails are one of the most common ways ransomware ends up on users’ computers. MailWasher filters spam and lets you preview emails on a server without downloading them onto your computer. MailWasher has customizable spam filters, uses bayesian filtering and works with all major email programs: Outlook, Outlook Express, Thunderbird, GMail, etc.
Remove ZFX Ransomware
Now that you have your recovered the files or at least stored the still encrypted files on an external device, it is time to scan your computer with AV and anti-malware software or, better yet, reinstall the operating system, to fully remove ZFX ransomware and get rid of any possible traces. Remember to also scan your external device before putting files back on your computer!