What is Cyber_Puffin ransomware?
Cyber_Puffin is a ransomware program, which means it makes money by infecting computers, encrypting all files on them with cryptographic algorithms, and demanding payment for their decryption. Remarkably, this particular piece of ransomware is very similar to another recent one, Exploit6. Perhaps they’re written by the same hacker, or perhaps we’re seeing a birth of a new ransomware family.
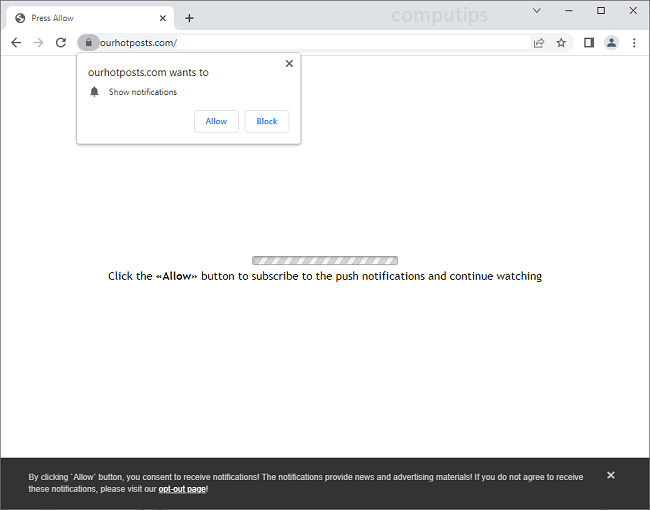
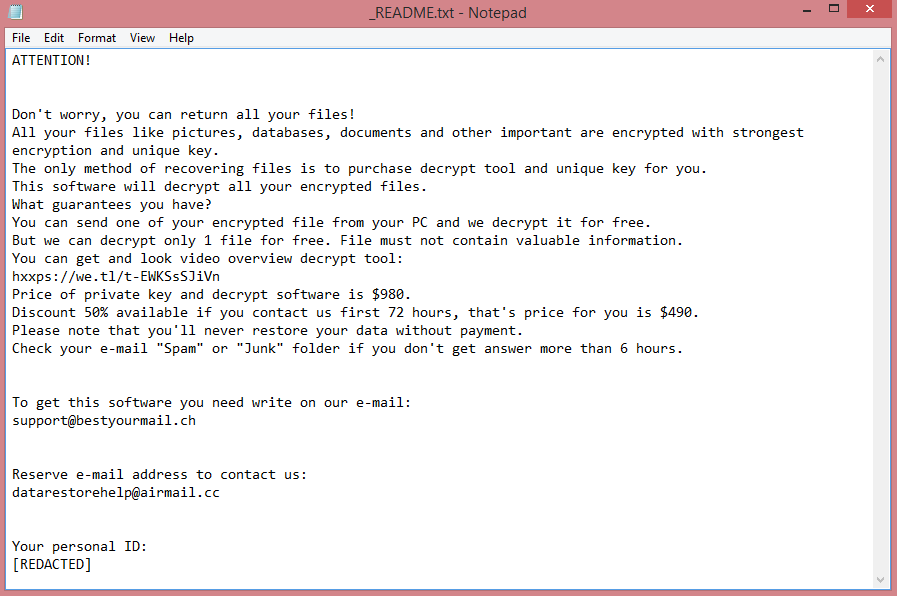
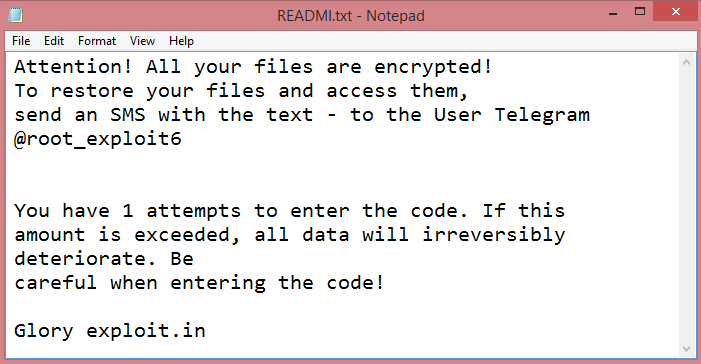
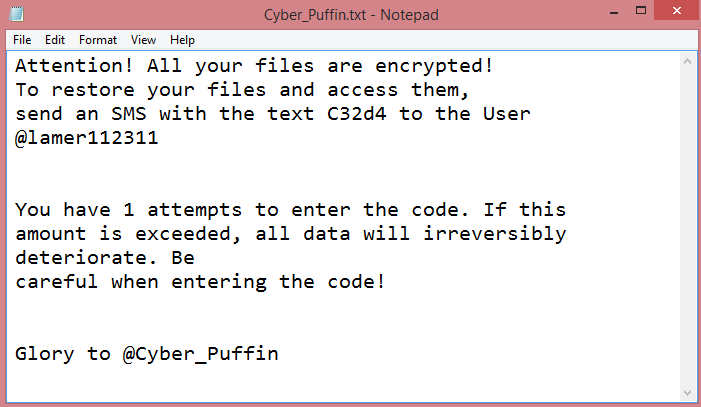
Either way, let’s move on to more practical concerns and details. On the image above, you can see the ransom note Cyber_Puffin leaves on infected computers. It is called “Cyber_Puffin.txt”, and doesn’t contain much information; merely an instruction to send a text message to a certain Telegram user. This might mean that the hackers negotiate decryption prices individually, or perhaps they just want to get the victim engaged before mentioning the price.
The ransomware also changes the encrypted files’ names, or, more specifically, extensions. They are all given a new .Cyber_Puffin file extension, with their old one remaining intact as well. So a file named “note.txt” would be changed to “note.txt.Cyber_Puffin”.
It is best not to contact the hackers, especially since they want you to use Telegram and not e-mail; you might get your account stolen. Beyond that, the criminals often simply don’t decrypt the files even after the payment.
But it is possible to remove Cyber_Puffin ransomware for free, and even decrypt .Cyber_Puffin files. Read the guide below for instructions.