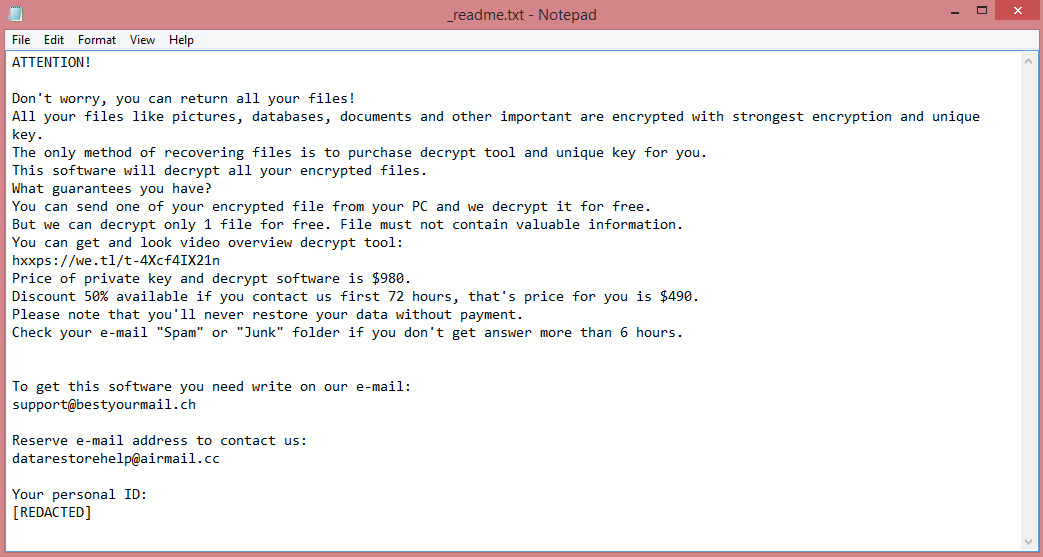
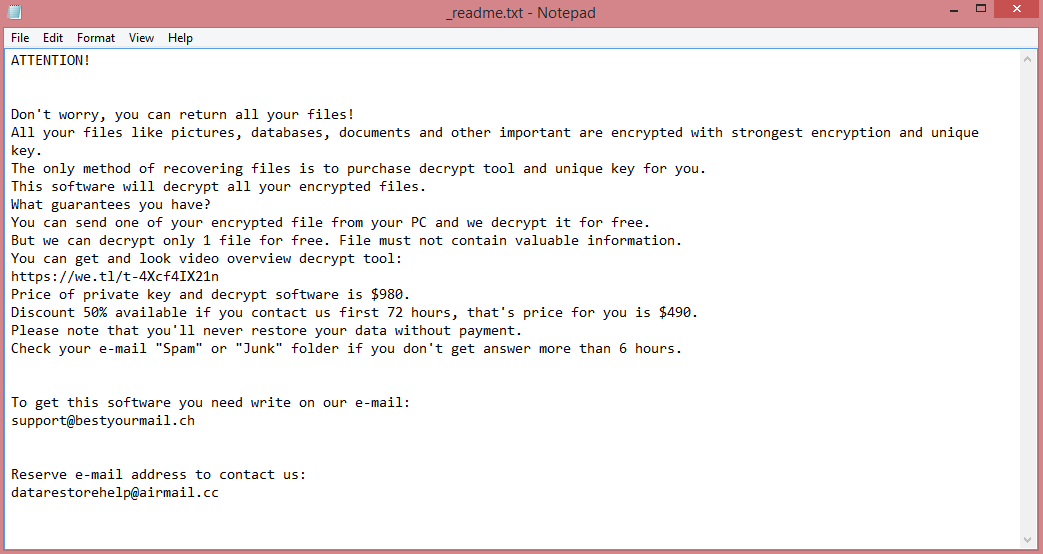
![62IX ransom note:
Attention! All your files are encrypted!
To restore your files and access them,
send an SMS with the text [REDACTED] to the User
Telegram @Verve_is_God
You have 1 attempts to enter the code. If this
amount is exceeded, all data will irreversibly
deteriorate. Be
careful when entering the code!
Glory @ixix6262
This is the end of the note. The guide below will explain how to remove 62IX ransomware.](https://www.computips.org/wp-content/uploads/2022/09/how-to-decrypt-62ix-ransomware.png)
What is 62IX ransomware?
62IX is a harmful ransomware program that encrypts all files on the computer infected with it. This means that the files can no longer be opened, edited, or even previewed. But this is a reversible procedure; which is where the hackers’ profit motivation comes in. The program doesn’t just encrypt all these files, it also offers a way to decrypt them by leaving a ransom note. The note, called “КАК РАСШИФРОВАТЬ FILES.txt”, merely points the victim at the hacker’s Telegram account (the full text of the note is available on the image above). Also of interest is the note’s name: “КАК РАСШИФРОВАТЬ” means “HOW TO DECRYPT” in Russian. Perhaps it is a clue to the program’s origin.
Either way, we also know that the virus renames the files it encrypts, adding .62IX file extension to them. This means that “photo.png” would be renamed to “photo.png.62IX”, for example. This is pretty typical; this gives the victim a clear hint that something is wrong, as all file icons change to blank ones as a result.
Paying hackers, especially ones with potentially Russian origins, is a bad idea. And contacting them over Telegram could be dangerous for your account there. Thankfully, there is a way to remove 62IX ransomware and decrypt .62IX files without paying the hacker. Read the guide below for details.
![Joker ransom note:
Your Files Are Has Been Locked
Your Files Has Been Encrypted with cryptography Algorithm
If You Need Your Files And They are Important to You, Dont be shy Send Me an Email
Send Test File + The Key File on Your System (File Exist in C:/ProgramData example : RSAKEY-SE-24r6t523 pr RSAKEY.KEY) to
Make Sure Your Files Can be Restored
Make an Agreement on Price with me and Pay
Get Decryption Tool + RSA Key AND Instruction For Decryption Process
Attention:
1- Do Not Rename or Modify The Files (You May loose That file)
2- Do Not Try To Use 3rd Party Apps or Recovery Tools ( if You want to do that make an copy from Files and try on them and
Waste Your time )
3-Do not Reinstall Operation System(Windows) You may loose the key File and Loose Your Files
4-Do Not Always Trust to Middle mans and negotiators (some of them are good but some of them agree on 4000usd for example and
Asked 10000usd From Client) this Was happened
Your Case ID :[REDACTED]
OUR Email :suppransomeware@tutanota.com
in Case of no answer: suppransomeware@mailfence.com
This is the end of the note. The following is a guide explaining how to remove Joker ransomware.](https://www.computips.org/wp-content/uploads/2022/09/how-to-remove-joker-ransomware.png)