Dracula is a type of malware that infects computers and operates as a ransomware program. Once a computer is infected with Dracula, the malware encrypts files on the system, making them inaccessible to the user. The victim is then prompted to pay a ransom in order to receive a decryption key to unlock their files. Dracula is a particularly dangerous form of malware because it can quickly spread through a network, affecting multiple computers within an organization.
How to remove X-finder.pro
X-finder.pro adware is a type of potentially unwanted program that displays intrusive advertisements and redirects users to potentially harmful websites. This adware is often bundled with free software downloads and can be unknowingly installed by users when they install other programs. Once installed, X-finder.pro adware starts displaying pop-up ads, banners, and sponsored links on the affected computer, making browsing the internet a frustrating experience.
How to remove GrowthStyle (Mac)
GrowthStyle is a type of adware that specifically targets Mac computers. This malicious software infects Mac systems by disguising itself as a legitimate program or browser extension. Once installed, GrowthStyle starts displaying intrusive and unwanted advertisements to the user, often in the form of pop-ups or banners. These ads can be very annoying and disruptive to the user's browsing experience.
How to remove Switch To New Server pop-ups
Switch To New Server is a common message that appears on web browsers when a website is undergoing maintenance or is being moved to a new server. This typically happens when the website owner decides to switch hosting providers or upgrade to a more powerful server to handle increased traffic or improve performance. When this message appears, it means that the website is temporarily unavailable as the migration process is being completed.
How to remove Ghostly
Ghostly is a type of malicious software, commonly referred to as malware, that infects computers and disrupts their normal operations. This type of malware is designed to secretly infiltrate a computer system and perform various harmful activities, such as stealing sensitive information, corrupting files, and slowing down the system's performance. Ghostly can be especially dangerous as it often operates in the background without the user's knowledge, making it difficult to detect and remove.
How to remove Elon Musk Crypto Giveaway pop-ups
Elon Musk Crypto Giveaway is a scam that has been circulating on the internet, particularly on social media platforms and websites. The scam claims that Elon Musk is giving away cryptocurrency, typically Bitcoin or Ethereum, to individuals who participate in the giveaway. This scheme is designed to trick unsuspecting individuals into providing personal information or sending cryptocurrency to the scammers, with the promise of receiving even more in return. However, there is no actual giveaway being conducted by Elon Musk or any legitimate entity associated with him.
How to remove Shadow (Ran_jr_som) Ransomware and decrypt .shadow files
Shadow (Ran_jr_som) Ransomware is a malicious software that infects computers by encrypting files and demanding a ransom for their decryption. This ransomware typically enters a system through phishing emails, malicious websites, or software vulnerabilities. Once inside a computer, Shadow Ransomware adds a specific file extension to encrypted files, such as .shadow, making them inaccessible to the user.
How to remove SHINRA Ransomware and decrypt random files
SHINRA ransomware is a dangerous form of malware that infects computers through various means, such as malicious email attachments, fake software downloads, or exploiting vulnerabilities in the system. Once the ransomware gains access to a computer, it encrypts the files on the system, making them inaccessible to the user. SHINRA ransomware typically adds specific file extensions to the encrypted files, such as .shinra or .locked, to indicate that they have been compromised.
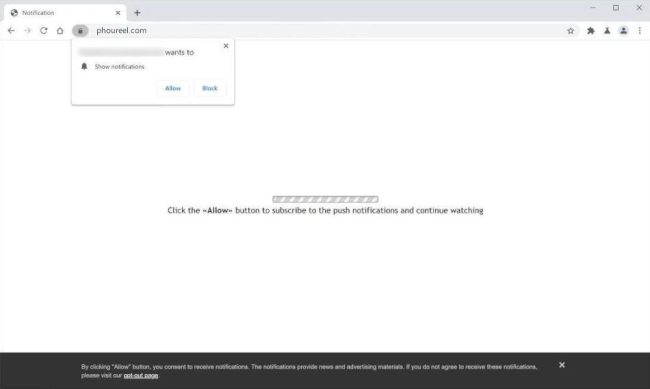
How to remove Phoureel.com
Phoureel.com is a malicious website that infects computers through various means, commonly through malicious downloads or deceptive pop-up ads. Once a user visits the website, it may prompt them to allow browser notifications, which, if granted, can lead to a barrage of unwanted pop-ups and advertisements. These notifications can be difficult to remove and can significantly disrupt the user's browsing experience.
How to stop Agreement Update email scam
Agreement Update email spam is a type of phishing scam that aims to trick users into clicking on malicious links or downloading malware by posing as a legitimate agreement or update notification. These emails often appear to be from well-known companies or organizations and claim that the user's account or agreement needs to be updated urgently. The email typically contains a sense of urgency to prompt the user to take immediate action, such as providing personal information or clicking on a link to update their account.