What is Shadow (Ran_jr_som) Ransomware?
Shadow (Ran_jr_som) Ransomware is a malicious software that infects computers by encrypting files and demanding a ransom for their decryption. This ransomware typically enters a system through phishing emails, malicious websites, or software vulnerabilities. Once inside a computer, Shadow Ransomware adds a specific file extension to encrypted files, such as .shadow, making them inaccessible to the user.
The ransomware uses strong encryption algorithms, such as RSA or AES, to lock the files and prevent their decryption without the unique decryption key. A ransom note is then created and displayed on the user’s desktop or in a text file within the encrypted folders, instructing the victim on how to pay the ransom to obtain the decryption key. While some decryption tools may be available for certain ransomware variants, it is important to note that there is no guaranteed way to decrypt files encrypted by Shadow Ransomware. It is always recommended to maintain regular backups of important data and to seek assistance from cybersecurity professionals in case of a ransomware attack.
Ransom note:
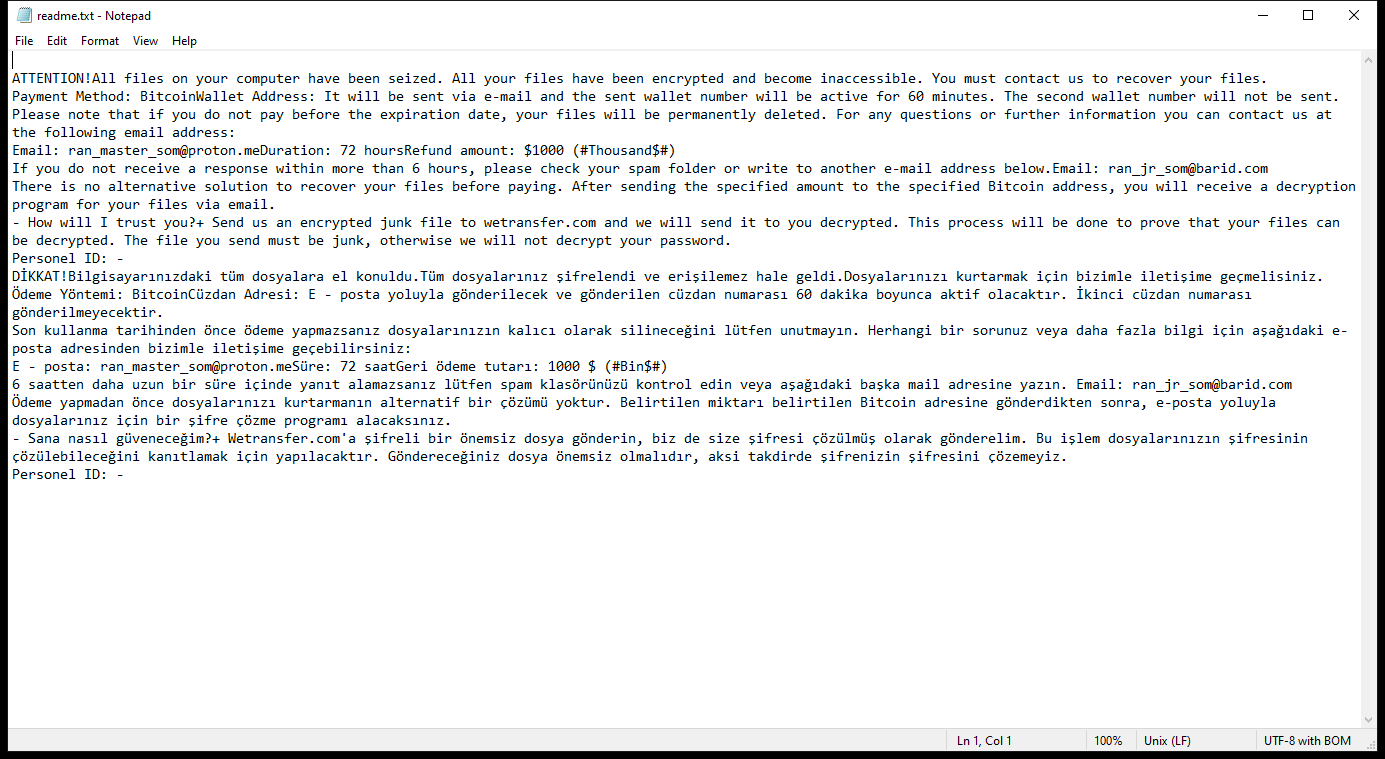
readme.txt contents:
ATTENTION!All files on your computer have been seized. All your files have been encrypted and become inaccessible. You must contact us to recover your files.
Payment Method: BitcoinWallet Address: It will be sent via e-mail and the sent wallet number will be active for 60 minutes. The second wallet number will not be sent.
Please note that if you do not pay before the expiration date, your files will be permanently deleted. For any questions or further information you can contact us at the following email address:
Email: ran_master_som@proton.meDuration: 72 hoursRefund amount: $1000 (#Thousand$#)
If you do not receive a response within more than 6 hours, please check your spam folder or write to another e-mail address below.Email: ran_jr_som@barid.com
There is no alternative solution to recover your files before paying. After sending the specified amount to the specified Bitcoin address, you will receive a decryption program for your files via email.
– How will I trust you?+ Send us an encrypted junk file to wetransfer.com and we will send it to you decrypted. This process will be done to prove that your files can be decrypted. The file you send must be junk, otherwise we will not decrypt your password.
Personel ID: –
DİKKAT!Bilgisayarınızdaki tüm dosyalara el konuldu.Tüm dosyalarınız şifrelendi ve erişilemez hale geldi.Dosyalarınızı kurtarmak için bizimle iletişime geçmelisiniz.
Ödeme Yöntemi: BitcoinCüzdan Adresi: E – posta yoluyla gönderilecek ve gönderilen cüzdan numarası 60 dakika boyunca aktif olacaktır. İkinci cüzdan numarası gönderilmeyecektir.
Son kullanma tarihinden önce ödeme yapmazsanız dosyalarınızın kalıcı olarak silineceğini lütfen unutmayın. Herhangi bir sorunuz veya daha fazla bilgi için aşağıdaki e-posta adresinden bizimle iletişime geçebilirsiniz:
E – posta: ran_master_som@proton.meSüre: 72 saatGeri ödeme tutarı: 1000 $ (#Bin$#)
6 saatten daha uzun bir süre içinde yanıt alamazsanız lütfen spam klasörünüzü kontrol edin veya aşağıdaki başka mail adresine yazın. Email: ran_jr_som@barid.com
Ödeme yapmadan önce dosyalarınızı kurtarmanın alternatif bir çözümü yoktur. Belirtilen miktarı belirtilen Bitcoin adresine gönderdikten sonra, e-posta yoluyla dosyalarınız için bir şifre çözme programı alacaksınız.
– Sana nasıl güveneceğim?+ Wetransfer.com’a şifreli bir önemsiz dosya gönderin, biz de size şifresi çözülmüş olarak gönderelim. Bu işlem dosyalarınızın şifresinin çözülebileceğini kanıtlamak için yapılacaktır. Göndereceğiniz dosya önemsiz olmalıdır, aksi takdirde şifrenizin şifresini çözemeyiz.
Personel ID: –
How Ransomwares Like Shadow (Ran_jr_som) Ransomware Ends Up on Users’ Computers:
Ransomware employs various methods to infect computers, exploiting vulnerabilities in both software and human behavior. One common tactic involves malicious email attachments or links, where unsuspecting users inadvertently download and execute the ransomware payload. Additionally, attackers may exploit software vulnerabilities, exploiting security flaws in outdated systems or applications to gain unauthorized access. Another avenue is through malicious websites or ads, which can silently install ransomware when visited. Furthermore, ransomware can spread through networked devices, leveraging weak passwords or unsecured connections to infiltrate entire systems.
- Remove Shadow (Ran_jr_som) Ransomware Automatically
- Back up Your Encrypted Files
- Decrypt .shadow Files
- Restore .shadow Files With File Recovery Tools
- Recover Encrypted Files From Shadow Copies
- How to Protect Your PC From Malware and Prevent Ransomware Infections In the Future
Remove Shadow (Ran_jr_som) Ransomware
First, we advise you to scan your computer with an antivirus to find and remove all remaining instances of Shadow (Ran_jr_som) Ransomware.
Other anti-malware software that may be able to get rid of Shadow (Ran_jr_som) Ransomware:
Norton (Windows, macOS, iOS, Android) The link may not work correctly in some countries.
Malwarebytes (Windows)
Back up Your Encrypted Files:
We advise you to create a copy of the encrypted files and put it away. That might help you if free ransomware decryptor becomes available in the future, or if you decide to pay and get the decryptor but something goes wrong and files get irreparably damaged in the process of decryption.
Decrypt .shadow Files:
Most ransomware use very complex encryption methods. Only the creators have the special key needed to unlock the files. Without this key, it’s impossible to get the data back. Usually, the hackers keep these keys on their own servers, not on the infected computers. Some ransomware is so well-made that it’s almost impossible to recover files without the hackers’ help. But some are not so good and have mistakes, like using the same key for everyone or keeping keys on the infected computer. That’s why it’s a good idea to look for tools to unlock your files if you get hit by ransomware. You can use NoMoreRansom site to find if a specific decryption tool for Shadow (Ran_jr_som) Ransomware exists.
Restore .shadow Files With File Recovery Tools:
Screenshot:
About Stellar Data Recovery
- Retrieves data from formatted, encrypted, or corrupted drives.
- Free trial version allows user to scan, preview and download up to 1GB of data.
- Supports Windows 11, 10, 8 and 7. A Mac variant is also available.
Recover Encrypted Files From Shadow Copies:
Shadow Explorer is a free tool designed to access Shadow Volume Copies in Windows systems. It allows users to retrieve previous versions of files and folders stored in these shadow copies. By selecting a specific disk and date, users may be able to recover lost or overwritten data. Download and install the latest version of Shadow Explorer, or opt for the portable version.
- Launch Shadow Explorer.
- On the top left part of the window pick a disk (C:\, D:\, etc.) and a date when a snapshot of files was captured.
- To retrieve file or a folder, right-click on it and select Export.
- Select the destination where you want to store the files
How to Protect Your PC From Malware and Prevent Ransomware Infections In the Future:
- Keep software updated: Regularly update your operating system, antivirus software, and other applications to patch security vulnerabilities.
- Use antivirus and anti-malware software: Install reputable antivirus and anti-malware programs to detect and remove ransomware threats.
- Enable firewall: Activate and properly configure a firewall to monitor and block suspicious network traffic.
- Backup data regularly: Create and maintain regular backups of important files and data on separate storage devices or cloud services to mitigate the impact of a ransomware attack.
- Exercise caution with email: Be cautious when opening email attachments or clicking on links, especially from unknown or suspicious senders.
- Stay informed: Stay up-to-date on the latest ransomware threats, tactics, and prevention strategies to adapt your defenses accordingly.
