What Is Locky Ransomware?
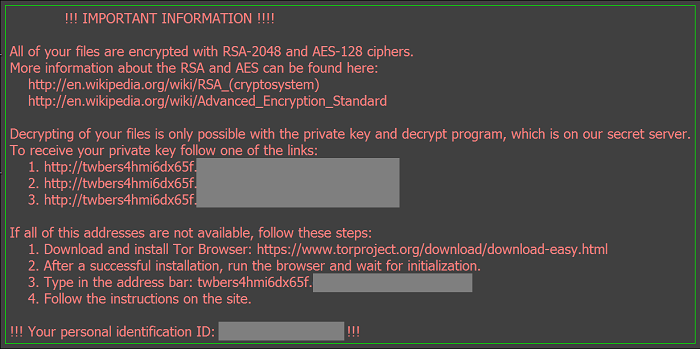
Locky is ransomware not different from many others: it encrypts user’s files and demands payment for a decryption tool. Files stored in cloud services and shared files on local networks are also encrypted, so the only sure way to get back the files is to restore from offline backups. Even paying the ransom is not a reliable method: some users reported that the decryption tool wasn’t able to decrypt all of the files. However, some methods, like restoring the files from shadow copies, might work in some cases. If you were hit and want to find out how to remove Locky and decrypt your files, you can read this article.
How Does Locky Ransomware Work
Locky is distributed primarily via Word documents attached to emails, although infections by visiting malicious websites have been happening too. If macroses are enabled in user’s Word settings, a specific macros is executed that downloads an executable file. This file then is launched, and it starts to encrypt all user’d documents with certain extensions. The files’ names are changed to strings of numbers and letters, and .locky extensions are added.
How to Get Rid of Locky
You can remove all files and registry values left by Locky using a malware removal tool, or do it by hand.
Delete Files and Registry Keys Left by Locky
Delete These Files:
%Temp%\(random).exe
%UserpProfile%\Desktop\_Locky_recover_instructions.bmp
%UserpProfile%\Desktop\_Locky_recover_instructions.txt
Delete These Registry Keys and Values:
HKEY_CURRENT_USER\Software\Locky
HKEY_CURRENT_USER\Control Panel\Desktop\Wallpaper "%UserProfile%\Desktop\_Locky_recover_instructions.bmp"
How to Get Back Files Encrypted by Locky
Use a Decryption Utility
At the time this article was written no decryption tools for Locky existed; however, there is always a possibility of one to be created in the future.
Restore From Cloud Service
Locky encrypts files stored on cloud services, however, you can try to use previous versions feature some of the services (such as Google Drive, DropBox, SkyDrive) offer. You’ll have to use the service’s website for that: right-click a file and select Previous versions, Manage revisions or something similar. See if there’s any un-encrypted versions of the file available.
Use Previous Versions Utility
While Locky deletes shadow copies of files created through this Windows feature, sometimes errors occur or the user is able to stop Locky from finishing its work, and previous versions of files stay accessible. In Windows 7 you can right-click on a file or folder, select Properties => Previous Versions and choose the latest available version. For other versions of Windows you’ll need to use Shadow Explorer tool to access shadow copies of your files.
Please note that shadow copies of your files are only created if you have System Restore turned on.
How to Protect Yourself From Locky and Similar Ransomware in the Future:
- Make regular backups of your data. At least one of the backups should be on a removable media, stored away from the computer (not connected to it).
- Don’t open attachments in emails from people you don’t know. In fact, even if you get an email from a friend and there is an attachment in it you didn’t expect, better make sure your friend really sent it, before clicking on the attached file.
- Use www.virustotal.com to scan email attachments before opening them.
- Have a powerful anti-malware installed.
- Keep your OS, browsers and security utilities updated. Sometimes ransomware is distributed using software vulnerabilities. Malware writers find new browser and OS vulnerabilities to exploit all the time. Software writers, in turn, release patches and updates to get rid of the known vulnerabilities and lesser the chance of malware penetration. Antivirus program’s signature databases get updated every day and even more often to include new virus signatures.
- Adjust your browsers’ settings to block pop-ups, don’t load plug-ins automatically, don’t download files without asking.
- Download and use Adblock, Adblock Plus, uBlock or one of similar trustworthy extensions for blocking third-party advertisements on web-sites.
- Don’t just click on any link you see while browsing the web. That especially applies to links in comments, on forums or in instant messengers. Pretty often these are spam links. Sometimes they are used for increasing the traffic to the sites, but often enough they will land you on malicious pages that will try to execute a malicious code and infect your computer.
- Don’t download software from unverified web-sites. You can easily download a trojan (a program, that is not what it pretends to be, and is a malware instead). Or some unwanted programs could get installed along with the app.