What is MALARIA VIRUS Ransomware?
MALARIA VIRUS Ransomware is a type of malicious software that infects computers through various methods such as phishing emails, malicious websites, and software vulnerabilities. Once a computer is infected, the ransomware encrypts files on the system and adds specific file extensions to them, making them inaccessible to the user. MALARIA VIRUS Ransomware typically uses strong encryption algorithms such as AES or RSA to lock the files, making it difficult for victims to decrypt them without the decryption key.
After encrypting the files, MALARIA VIRUS Ransomware usually creates a ransom note that instructs the victim on how to pay a ransom in exchange for the decryption key. The ransom note is typically displayed on the desktop or in folders containing encrypted files. While there may be some decryption tools available online, it is important to exercise caution when using them as they may not always work or could potentially harm your computer further. To decrypt files encrypted by MALARIA VIRUS Ransomware without paying the ransom, it is recommended to first remove the ransomware from your system using antivirus software and then attempt to restore files from a backup, if available.
Ransom note:
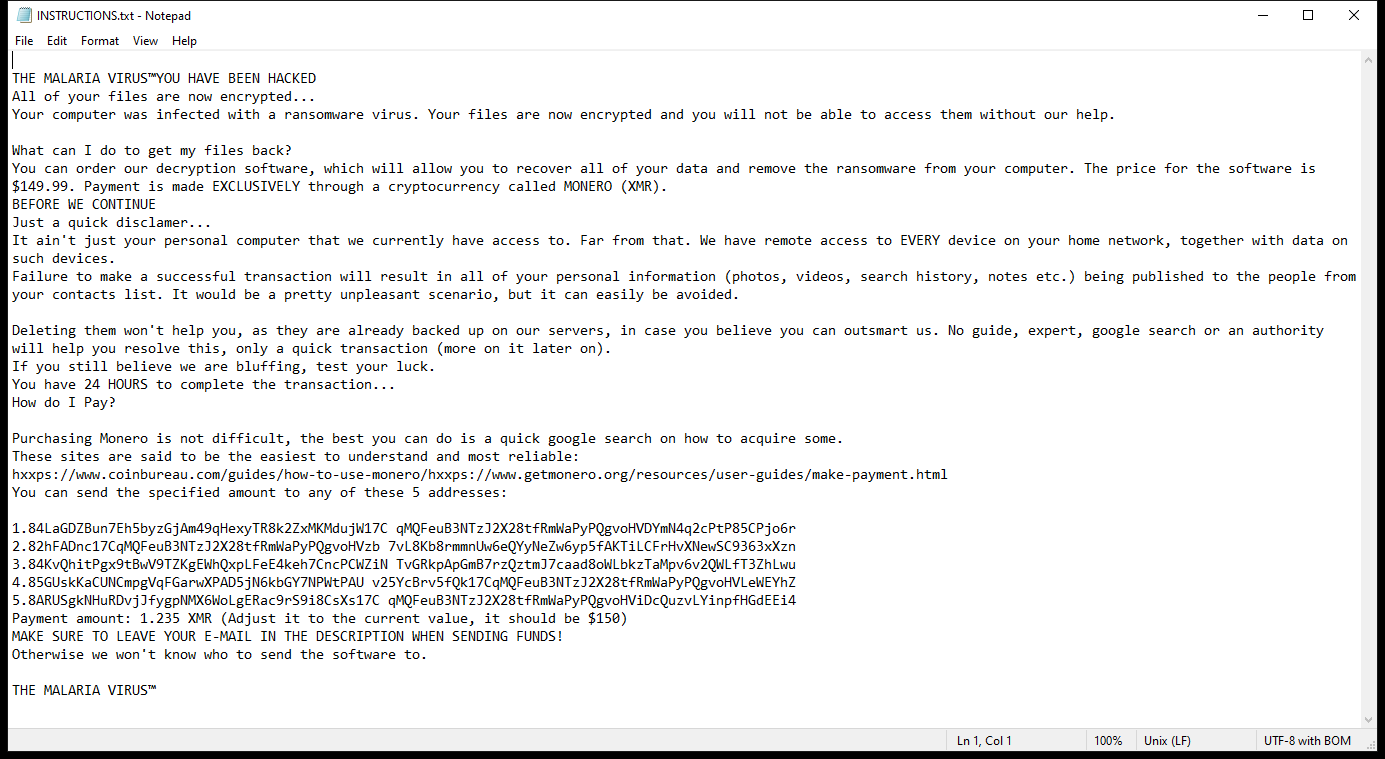
INSTRUCTIONS.txt contents:
THE MALARIA VIRUS™YOU HAVE BEEN HACKED
All of your files are now encrypted…
Your computer was infected with a ransomware virus. Your files are now encrypted and you will not be able to access them without our help.
What can I do to get my files back?
You can order our decryption software, which will allow you to recover all of your data and remove the ransomware from your computer. The price for the software is $149.99. Payment is made EXCLUSIVELY through a cryptocurrency called MONERO (XMR).
BEFORE WE CONTINUE
Just a quick disclamer…
It ain’t just your personal computer that we currently have access to. Far from that. We have remote access to EVERY device on your home network, together with data on such devices.
Failure to make a successful transaction will result in all of your personal information (photos, videos, search history, notes etc.) being published to the people from your contacts list. It would be a pretty unpleasant scenario, but it can easily be avoided.
Deleting them won’t help you, as they are already backed up on our servers, in case you believe you can outsmart us. No guide, expert, google search or an authority will help you resolve this, only a quick transaction (more on it later on).
If you still believe we are bluffing, test your luck.
You have 24 HOURS to complete the transaction…
How do I Pay?
Purchasing Monero is not difficult, the best you can do is a quick google search on how to acquire some.
These sites are said to be the easiest to understand and most reliable:
hxxps://www.coinbureau.com/guides/how-to-use-monero/hxxps://www.getmonero.org/resources/user-guides/make-payment.html
You can send the specified amount to any of these 5 addresses:
1.84LaGDZBun7Eh5byzGjAm49qHexyTR8k2ZxMKMdujW17C qMQFeuB3NTzJ2X28tfRmWaPyPQgvoHVDYmN4q2cPtP85CPjo6r
2.82hFADnc17CqMQFeuB3NTzJ2X28tfRmWaPyPQgvoHVzb 7vL8Kb8rmmnUw6eQYyNeZw6yp5fAKTiLCFrHvXNewSC9363xXzn
3.84KvQhitPgx9tBwV9TZKgEWhQxpLFeE4keh7CncPCWZiN TvGRkpApGmB7rzQztmJ7caad8oWLbkzTaMpv6v2QWLfT3ZhLwu
4.85GUskKaCUNCmpgVqFGarwXPAD5jN6kbGY7NPWtPAU v25YcBrv5fQk17CqMQFeuB3NTzJ2X28tfRmWaPyPQgvoHVLeWEYhZ
5.8ARUSgkNHuRDvjJfygpNMX6WoLgERac9rS9i8CsXs17C qMQFeuB3NTzJ2X28tfRmWaPyPQgvoHViDcQuzvLYinpfHGdEEi4
Payment amount: 1.235 XMR (Adjust it to the current value, it should be $150)
MAKE SURE TO LEAVE YOUR E-MAIL IN THE DESCRIPTION WHEN SENDING FUNDS!
Otherwise we won’t know who to send the software to.
THE MALARIA VIRUS™
How Ransomwares Like MALARIA VIRUS Ransomware Ends Up on Users’ Computers:
Ransomware employs various methods to infect computers, exploiting vulnerabilities in both software and human behavior. One common tactic involves malicious email attachments or links, where unsuspecting users inadvertently download and execute the ransomware payload. Additionally, attackers may exploit software vulnerabilities, exploiting security flaws in outdated systems or applications to gain unauthorized access. Another avenue is through malicious websites or ads, which can silently install ransomware when visited. Furthermore, ransomware can spread through networked devices, leveraging weak passwords or unsecured connections to infiltrate entire systems.
- Remove MALARIA VIRUS Ransomware Automatically
- Back up Your Encrypted Files
- Decrypt random Files
- Restore random Files With File Recovery Tools
- Recover Encrypted Files From Shadow Copies
- How to Protect Your PC From Malware and Prevent Ransomware Infections In the Future
Remove MALARIA VIRUS Ransomware
First, we advise you to scan your computer with an antivirus to find and remove all remaining instances of MALARIA VIRUS Ransomware.
Other anti-malware software that may be able to get rid of MALARIA VIRUS Ransomware:
Norton (Windows, macOS, iOS, Android) The link may not work correctly in some countries.
Malwarebytes (Windows)
Back up Your Encrypted Files:
We advise you to create a copy of the encrypted files and put it away. That might help you if free ransomware decryptor becomes available in the future, or if you decide to pay and get the decryptor but something goes wrong and files get irreparably damaged in the process of decryption.
Decrypt random Files:
Most ransomware use very complex encryption methods. Only the creators have the special key needed to unlock the files. Without this key, it’s impossible to get the data back. Usually, the hackers keep these keys on their own servers, not on the infected computers. Some ransomware is so well-made that it’s almost impossible to recover files without the hackers’ help. But some are not so good and have mistakes, like using the same key for everyone or keeping keys on the infected computer. That’s why it’s a good idea to look for tools to unlock your files if you get hit by ransomware. You can use NoMoreRansom site to find if a specific decryption tool for MALARIA VIRUS Ransomware exists.
Restore random Files With File Recovery Tools:
Screenshot:
About Stellar Data Recovery
- Retrieves data from formatted, encrypted, or corrupted drives.
- Free trial version allows user to scan, preview and download up to 1GB of data.
- Supports Windows 11, 10, 8 and 7. A Mac variant is also available.
Recover Encrypted Files From Shadow Copies:
Shadow Explorer is a free tool designed to access Shadow Volume Copies in Windows systems. It allows users to retrieve previous versions of files and folders stored in these shadow copies. By selecting a specific disk and date, users may be able to recover lost or overwritten data. Download and install the latest version of Shadow Explorer, or opt for the portable version.
- Launch Shadow Explorer.
- On the top left part of the window pick a disk (C:\, D:\, etc.) and a date when a snapshot of files was captured.
- To retrieve file or a folder, right-click on it and select Export.
- Select the destination where you want to store the files
How to Protect Your PC From Malware and Prevent Ransomware Infections In the Future:
- Keep software updated: Regularly update your operating system, antivirus software, and other applications to patch security vulnerabilities.
- Use antivirus and anti-malware software: Install reputable antivirus and anti-malware programs to detect and remove ransomware threats.
- Enable firewall: Activate and properly configure a firewall to monitor and block suspicious network traffic.
- Backup data regularly: Create and maintain regular backups of important files and data on separate storage devices or cloud services to mitigate the impact of a ransomware attack.
- Exercise caution with email: Be cautious when opening email attachments or clicking on links, especially from unknown or suspicious senders.
- Stay informed: Stay up-to-date on the latest ransomware threats, tactics, and prevention strategies to adapt your defenses accordingly.
