What is NAKW ransomware?
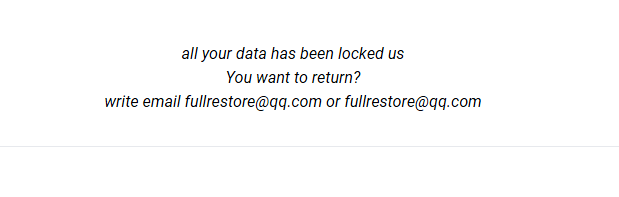
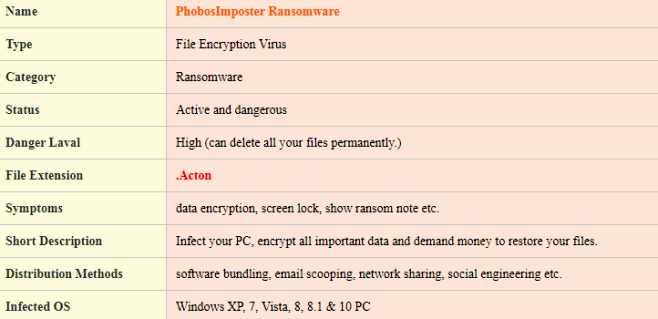
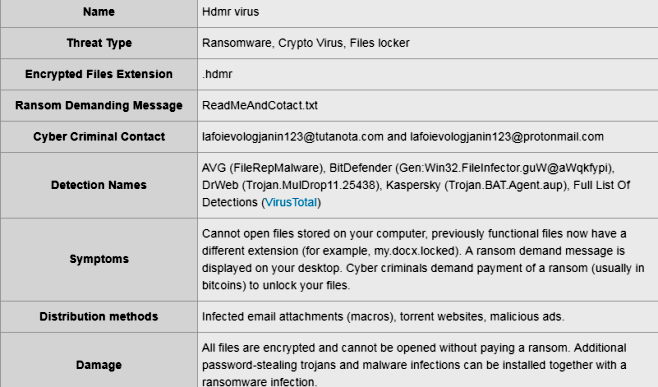
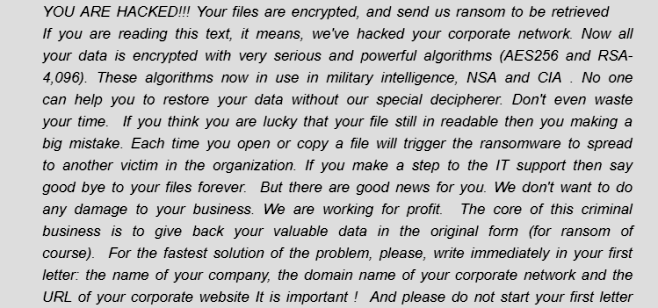
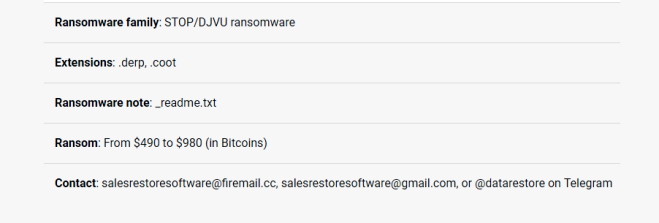
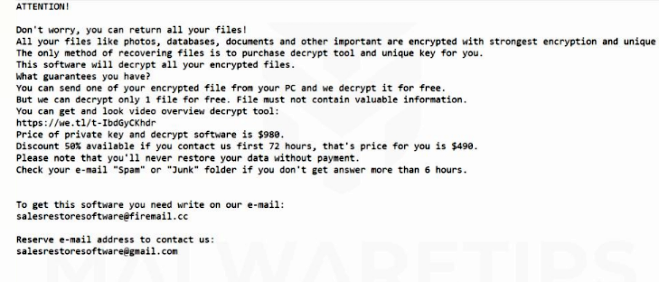
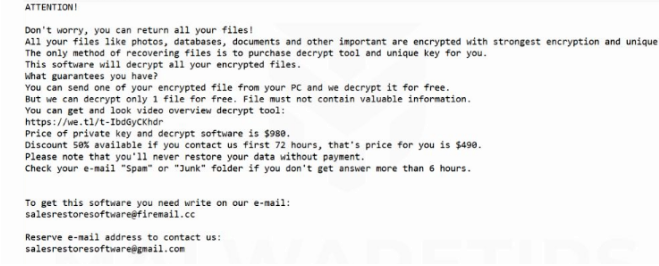
NAKW ransomware is an extortion application with an online extortion scheme for user files. The main goal of NAKW ransomware is penetration into the computer and encryption of important files. It will add the .nakw extension to the files and leave ransom notes called _readme.txt asking you for the payment of about $ 1000 for returning your files. This article was created specifically to shield users from the tricks of NAKW ransomware. Do not pay money to ransomware developers. There is always a chance that they will receive money and leave you alone with problems. To try and get rid of problems and NAKW ransomware, read our article.