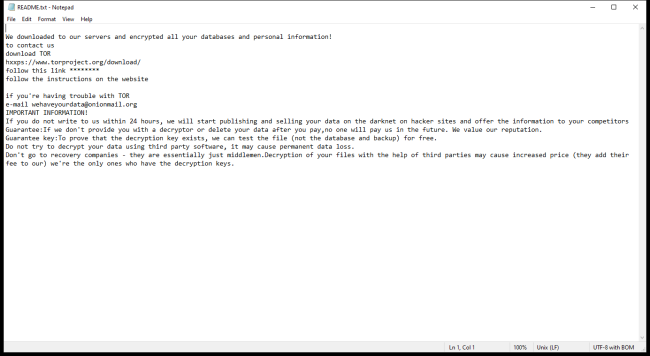
L3MON Ransomware is a dangerous type of malware that infects computers through various methods, such as phishing emails, malicious downloads, or exploiting vulnerabilities in software. Once installed on a system, L3MON Ransomware encrypts files on the computer, adding specific file extensions to them to indicate that they have been encrypted. The ransomware uses a strong encryption algorithm to lock the files, making them inaccessible to the user.
Category: Ransomware
Articles about ransomware – malware encrypting your personal files or stopping you from accessing your computer – and ways to remove it
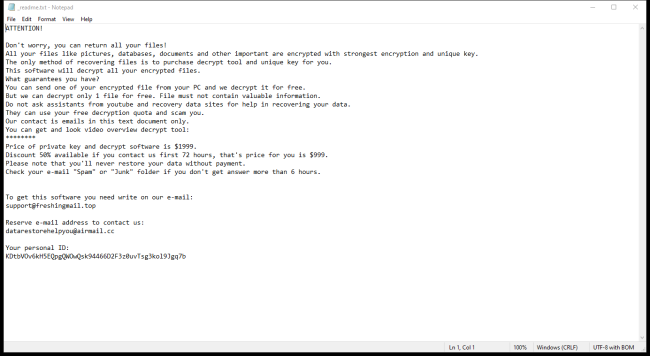
How to remove Trinity Ransomware and decrypt .trinitylock files
Trinity Ransomware is a malicious software that infects computers through various means, such as phishing emails, malicious websites, or software vulnerabilities. Once installed on a system, Trinity Ransomware encrypts the victim's files using a strong encryption algorithm, making them inaccessible without the decryption key. The ransomware adds the ".trinitylock" extension to the encrypted files, making it easy for the victim to identify which files have been affected.
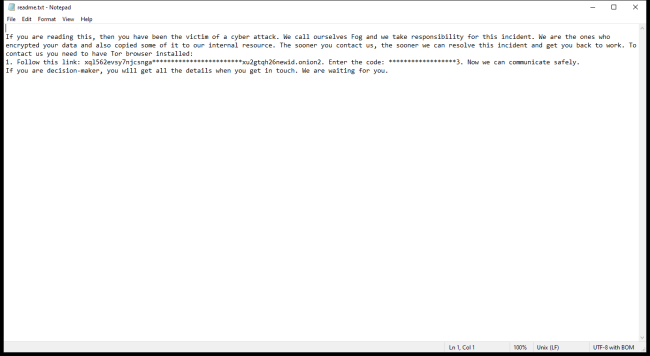
How to remove Fog Ransomware and decrypt .fog files
Fog ransomware is a malicious software that infects computers by encrypting files and demanding a ransom for their decryption. This type of ransomware typically enters a computer through phishing emails, malicious websites, or infected downloads. Once installed, Fog ransomware adds a ".fog" extension to encrypted files, making them inaccessible to the user.
How to remove DORRA Ransomware and decrypt .dorra files
DORRA Ransomware is a dangerous malware that infects computers by encrypting files and demanding a ransom for their release. It typically spreads through malicious email attachments, fake software updates, or compromised websites. Once infected, DORRA Ransomware adds the .dorra file extension to encrypted files, making them inaccessible to the user.
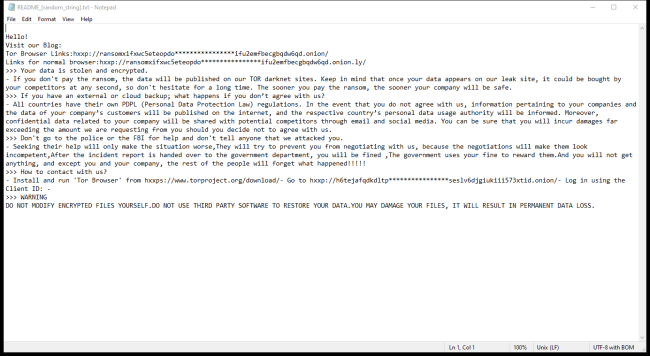
How to remove RansomHub Ransomware and decrypt random files
RansomHub Ransomware is a malicious software that infects computers by encrypting files and demanding a ransom for their release. It typically spreads through phishing emails, malicious websites, or software vulnerabilities. Once installed on a system, RansomHub encrypts files with extensions such as .docx, .xlsx, .jpg, .pdf, and more, rendering them inaccessible without the decryption key.
How to remove Orbit Ransomware and decrypt .orbit files
Orbit Ransomware is a malicious software that infects computers by encrypting files on the system and demanding a ransom in exchange for the decryption key. It typically spreads through malicious email attachments, compromised websites, or fake software downloads. Once installed on a computer, Orbit Ransomware adds the .orbit file extension to encrypted files, making them inaccessible to the user.
How to remove Watz Ransomware and decrypt .watz files
Watz Ransomware is a type of malicious software that infects computers by encrypting files and demanding a ransom for their release. It typically spreads through email attachments, malicious websites, or software vulnerabilities. Once a computer is infected, Watz Ransomware will add a specific file extension to all affected files, making them inaccessible to the user. The ransomware uses a strong encryption algorithm to lock the files, making it nearly impossible to decrypt them without the decryption key.
How to remove PartiZAN32 Ransomware and decrypt .xqwertzuioplkjhgfyxcvbnmd files
PartiZAN32 Ransomware is a dangerous malware that infects computers through various methods, such as phishing emails, malicious downloads, or software vulnerabilities. Once it infiltrates a system, PartiZAN32 Ransomware adds specific file extensions to the encrypted files, such as .xqwertzuioplkjhgfyxcvbnmd. It uses a strong encryption algorithm to lock the files, making them inaccessible to the victim.
How to remove Waqa Ransomware and decrypt .waqa files
Waqa Ransomware is a type of malicious software that infects computers by encrypting files and demanding a ransom in exchange for the decryption key. This ransomware typically spreads through phishing emails, malicious websites, or software vulnerabilities. Once infected, Waqa Ransomware adds a unique file extension to encrypted files, making them inaccessible to the user without the decryption key.
How to remove Chaddad Ransomware and decrypt .chaddad files
Chaddad Ransomware is a malicious software that infects computers through email attachments, malicious websites, or software vulnerabilities. Once installed on a computer, Chaddad Ransomware encrypts files using a strong encryption algorithm, making them inaccessible to the user. It adds the .chaddad file extension to the encrypted files, making it easy to identify which files have been affected.