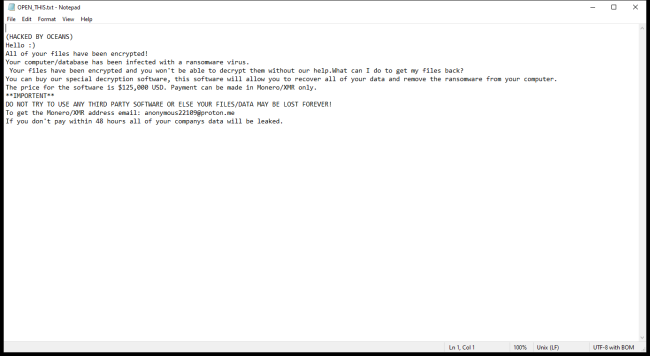
OCEANS Ransomware is a type of malicious software that encrypts files on infected computers and demands a ransom in exchange for the decryption key. It typically infects computers through phishing emails, malicious downloads, or exploiting vulnerabilities in software. Once a computer is infected, OCEANS Ransomware encrypts files by adding specific file extensions such as .oceans or .locked to them, making them inaccessible to the user.
Category: Ransomware
Articles about ransomware – malware encrypting your personal files or stopping you from accessing your computer – and ways to remove it
How to remove Veza Ransomware and decrypt .veza files
Veza Ransomware is a type of malware that infects computers through deceptive email attachments, malicious websites, or software downloads. Once it infiltrates a system, Veza Ransomware encrypts the files on the computer, making them inaccessible to the user. It adds the .veza file extension to the encrypted files, indicating that they have been compromised. The ransomware uses a sophisticated encryption algorithm to lock the files, making it extremely difficult to decrypt them without the decryption key.
How to remove EDHST Ransomware and decrypt .edhst files
EDHST ransomware is a malicious software that encrypts files on the infected computer, making them inaccessible to the user. It typically infiltrates computers through phishing emails, malicious websites, or software vulnerabilities. Once the ransomware is activated, it adds the .edhst file extension to encrypted files, such as photos, documents, and videos, rendering them unreadable. EDHST ransomware uses a strong encryption algorithm to lock the files, making it nearly impossible to decrypt without the decryption key.
How to remove OPIX Ransomware and decrypt random files
OPIX Ransomware is a malicious software that encrypts files on a victim's computer and demands a ransom in exchange for decrypting them. This type of ransomware typically infects computers through phishing emails, malicious attachments, or by exploiting vulnerabilities in outdated software. Once infected, OPIX Ransomware adds specific file extensions to encrypted files, making them inaccessible to the user.
How to remove Capibara Ransomware and decrypt .capibara files
Capibara Ransomware is a type of malicious software that encrypts files on a computer, making them inaccessible to the user. This ransomware typically spreads through email attachments, malicious websites, or software vulnerabilities. Once a computer is infected, Capibara Ransomware adds a specific file extension, such as .capibara, to the encrypted files. The ransomware uses a strong encryption algorithm to lock the files, making it nearly impossible for the user to access them without the decryption key.
How to remove Vehu Ransomware and decrypt .vehu files
Vehu ransomware is a malicious software program that infects computers by encrypting files and demanding a ransom for their decryption. It typically spreads through phishing emails, malicious websites, or software vulnerabilities. Once a computer is infected, Vehu ransomware adds a specific file extension to the encrypted files, making them inaccessible to the user. The encryption used by Vehu ransomware is typically strong and difficult to break without the decryption key.
How to remove Paaa Ransomware and decrypt .paaa files
Paaa Ransomware is a dangerous malware that infects computers through various means such as malicious email attachments, fake software updates, or exploiting vulnerabilities in the system. Once it infiltrates a computer, Paaa Ransomware adds specific file extensions to the files it encrypts, making them inaccessible to the user. It uses a strong encryption method to lock the files, making it nearly impossible to decrypt them without the decryption key.
How to remove Vepi Ransomware and decrypt .vepi files
Vepi Ransomware is a malicious software that infects computers by exploiting vulnerabilities in the system or through phishing emails. Once it infiltrates a system, Vepi Ransomware encrypts files on the infected computer, making them inaccessible to the user. It typically adds extensions such as .vepi to the encrypted files, making it easy for the attackers to identify which files have been compromised.
How to remove EnigmaWave Ransomware and decrypt .enigmawave files
EnigmaWave Ransomware is a dangerous form of malware that encrypts files on a victim's computer, making them inaccessible until a ransom is paid to the cybercriminals behind the attack. This ransomware typically infects computers through malicious email attachments, fake software updates, or through vulnerabilities in outdated software. Once a computer is infected, EnigmaWave Ransomware will add a specific file extension to all encrypted files, such as .enigmawave, making them easily distinguishable.
How to remove Qeza Ransomware and decrypt .qeza files
Qeza Ransomware is a malicious software that infects computers through various means, such as phishing emails, malicious websites, or software vulnerabilities. Once it infiltrates a system, Qeza encrypts files on the infected machine, adding a ".qeza" extension to each encrypted file. The ransomware uses a strong encryption algorithm to lock the files, making them inaccessible to the user.