Crypdrops Airdrops are a type of promotional campaign in the cryptocurrency space where companies distribute free tokens or coins to holders of a particular cryptocurrency. These airdrops are typically used to generate awareness, drive adoption, and reward loyal users. Participants in Crypdrops Airdrops may need to perform certain tasks such as following a company on social media, joining a Telegram group, or referring friends in order to receive the free tokens.
How to remove PartitionActivity (Mac)
PartitionActivity is a type of malware that infects Mac computers by creating hidden partitions on the system. These hidden partitions are used to store malicious files and processes that can run in the background without the user's knowledge. PartitionActivity is designed to evade detection by traditional antivirus software and can be difficult to remove once it has infected a computer.
How to remove Claim Your Merlin Chain ($MERL) Token pop-ups
Claim Your Merlin Chain ($MERL) Token is a cryptocurrency token that is part of the Merlin ecosystem. The Merlin ecosystem is a decentralized finance (DeFi) platform that aims to provide users with a range of services, including yield farming, staking, and swapping. The $MERL token is used within the Merlin ecosystem to incentivize users to participate in these services and to govern the platform through voting on proposals.
How to remove Ledger wallet stealer
A Ledger wallet stealer is a type of malicious software designed to target users of Ledger hardware wallets, which are popular devices used to securely store cryptocurrency. These stealers are specifically designed to infect computers and steal sensitive information such as private keys, passwords, and seed phrases used to access and manage cryptocurrency stored on the wallet. Once installed on a computer, the Ledger wallet stealer can silently monitor user activity, log keystrokes, and even take screenshots to capture sensitive information.
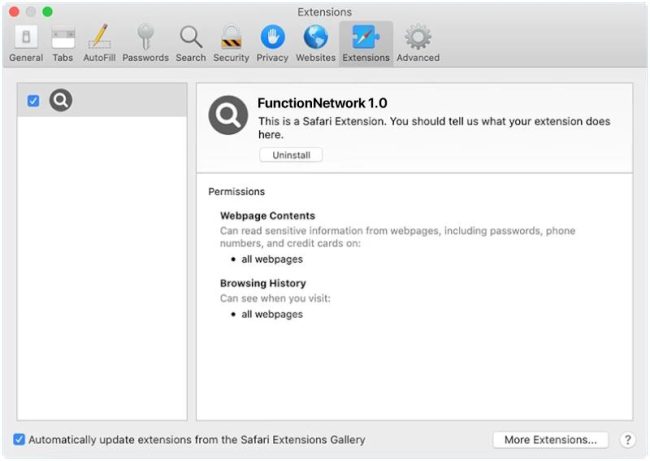
How to remove FunctionNetwork (Mac)
FunctionNetwork is a type of malware that specifically targets Mac computers. This malware is designed to infiltrate a user's system and steal sensitive information, such as personal data, login credentials, and financial information. FunctionNetwork is usually distributed through malicious email attachments, fake software downloads, or infected websites. Once the malware is installed on a Mac, it can run in the background without the user's knowledge, silently collecting data and sending it to the attackers.
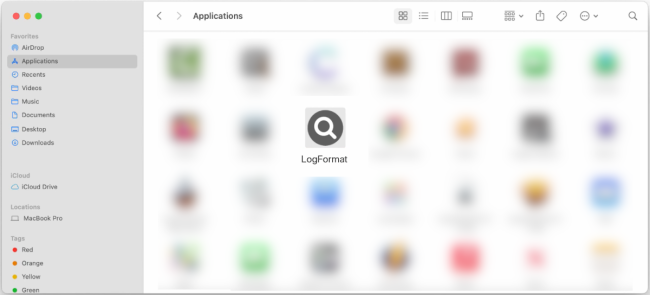
How to remove LogFormat (Mac)
LogFormat is a type of malware that targets Mac computers, specifically those running macOS. This malicious software can infect a system through various means, such as phishing emails, malicious websites, or software downloads. Once installed on a Mac, LogFormat can gather sensitive information from the infected computer, including login credentials, personal data, and browsing history. This information can then be used for identity theft, financial fraud, or other malicious activities.
How to remove HelperSignal (Mac)
HelperSignal is a malicious software that targets Mac operating systems. It is classified as adware, which means it displays unwanted advertisements and pop-ups on the infected device. HelperSignal typically infects Macs through deceptive methods such as software bundling, where it is packaged with legitimate software downloads and installed without the user's knowledge or consent.
How to stop Your Password Changed email scam
Your Password Changed email spam is a type of phishing scam that tricks users into believing that their password has been changed and prompts them to click on a link to verify or reset their password. These emails often appear to be from a legitimate source, such as a popular website or service, and may even include the company's logo and branding to make them look more convincing. However, clicking on the link in the email will not lead to a password reset page, but rather a malicious website designed to steal the user's login credentials.
How to remove MALARIA VIRUS Ransomware and decrypt random files
MALARIA VIRUS Ransomware is a type of malicious software that infects computers through various methods such as phishing emails, malicious websites, and software vulnerabilities. Once a computer is infected, the ransomware encrypts files on the system and adds specific file extensions to them, making them inaccessible to the user. MALARIA VIRUS Ransomware typically uses strong encryption algorithms such as AES or RSA to lock the files, making it difficult for victims to decrypt them without the decryption key.
How to remove TAMECAT
TAMECAT is a type of malware that infects computers and can cause a variety of harmful consequences. This malicious software is typically distributed through email attachments, downloads from untrustworthy websites, or through exploiting vulnerabilities in outdated software. Once TAMECAT infiltrates a computer system, it can replicate itself and spread to other devices on the same network.