DefaultOptimization is a type of malware that specifically targets Mac computers. This malicious software is designed to infiltrate a Mac system and make unauthorized changes to the default settings of the operating system. DefaultOptimization can infect a Mac computer through various means, such as downloading infected files or visiting compromised websites.
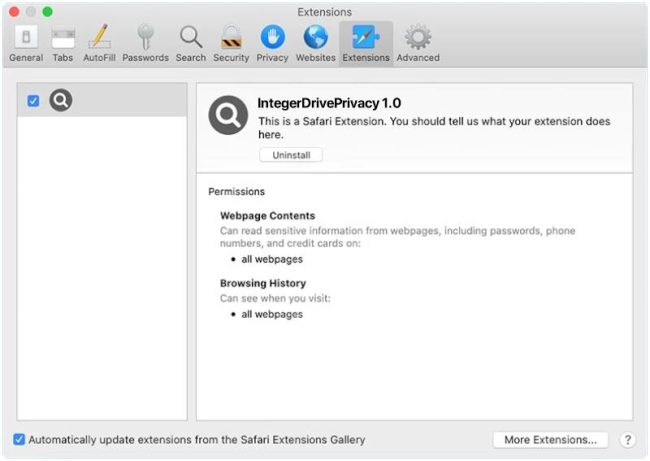
How to remove IntegerDrivePrivacy (Mac)
IntegerDrivePrivacy is a type of malware that specifically targets Mac systems. This malicious software is designed to infiltrate a user's computer without their knowledge or consent, with the primary goal of collecting sensitive personal information and compromising the user's online privacy. Once installed, IntegerDrivePrivacy can track the user's browsing habits, keystrokes, and even steal login credentials, putting the user at risk of identity theft and other cybercrimes.
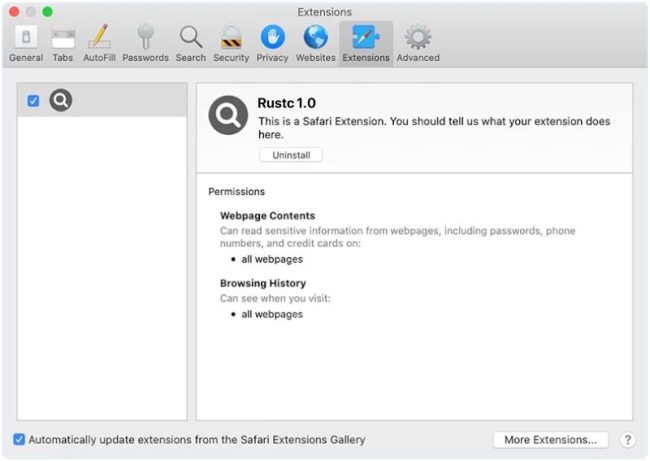
How to remove Rustc (Mac)
Rustc is a type of malware that specifically targets macOS devices. It is a form of ransomware that encrypts files on the infected computer, making them inaccessible to the user. Once the files are encrypted, the malware will display a message demanding payment in exchange for the decryption key. Rustc is typically spread through malicious email attachments, fake software downloads, or compromised websites.
How to remove VersionTrust (Mac)
VersionTrust is a type of malware that specifically targets Mac computers. It is a form of adware that sneaks onto a user's system through deceptive methods, such as bundling with other software or disguising itself as a legitimate program. Once installed, VersionTrust displays intrusive pop-up ads, redirects users to unwanted websites, and tracks their browsing habits for targeted advertising.
How to remove Arbitrum (ARB) NFT Airdrop pop-ups
Arbitrum (ARB) NFT Airdrop is a promotional campaign organized by the Arbitrum project to distribute non-fungible tokens (NFTs) to users. NFTs are unique digital assets that can represent ownership of various items such as art, collectibles, and in-game assets. The Arbitrum team aims to increase awareness and adoption of their platform by rewarding participants with these exclusive NFTs.
How to remove MP3 Cutter Joiner Free
MP3 Cutter Joiner Free is a popular software tool used for cutting and joining MP3 audio files. It allows users to easily trim and merge audio tracks, making it convenient for editing and customizing music files. However, despite its useful features, MP3 Cutter Joiner Free can also pose a risk to computer systems.
How to remove EnigmaWave Ransomware and decrypt .enigmawave files
EnigmaWave Ransomware is a dangerous form of malware that encrypts files on a victim's computer, making them inaccessible until a ransom is paid to the cybercriminals behind the attack. This ransomware typically infects computers through malicious email attachments, fake software updates, or through vulnerabilities in outdated software. Once a computer is infected, EnigmaWave Ransomware will add a specific file extension to all encrypted files, such as .enigmawave, making them easily distinguishable.
How to remove Riot Games & Twitch Giveaway pop-ups
Riot Games & Twitch Giveaway is a promotional campaign organized by Riot Games, the developer of popular online multiplayer games such as League of Legends and Valorant, in collaboration with Twitch, a popular streaming platform. The giveaway offers players a chance to win exclusive in-game items, skins, and other rewards by participating in various activities such as watching designated streams, following specific channels, or completing certain tasks within the games.
How to remove Bc20 (Mac)
Bc20 is a type of malware that specifically targets Mac computers. This malicious software is designed to infect Mac systems and can cause a range of harmful effects, including stealing sensitive information, spying on user activity, and even disrupting system functionality. Bc20 is often distributed through phishing emails, malicious websites, or software downloads, and once it infiltrates a Mac device, it can be difficult to detect and remove.
How to stop Treasures For Safekeeping email scam
Treasures For Safekeeping email spam is a type of phishing scam that attempts to trick recipients into believing they have won a prize or treasure. These emails typically claim that the recipient has been selected as a winner and must provide personal information or pay a fee in order to claim their prize. In reality, there is no prize and the scammers are only looking to steal personal information or money from unsuspecting victims.