What is Zfdv ransomware
Zfdv is a new strain of the STOP/Djvu ransomware. For this reason, it is very similar to other ransomware programs in this family, such as Ribd or Ygkz. Ransomware, as you probably already know, is a class of illegal programs that make hackers money by encrypting files and asking for payment to decrypt them.
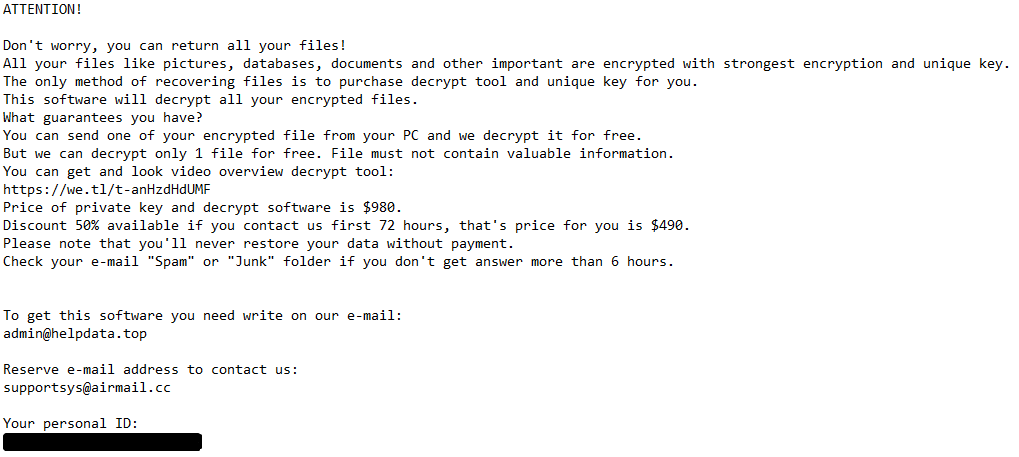
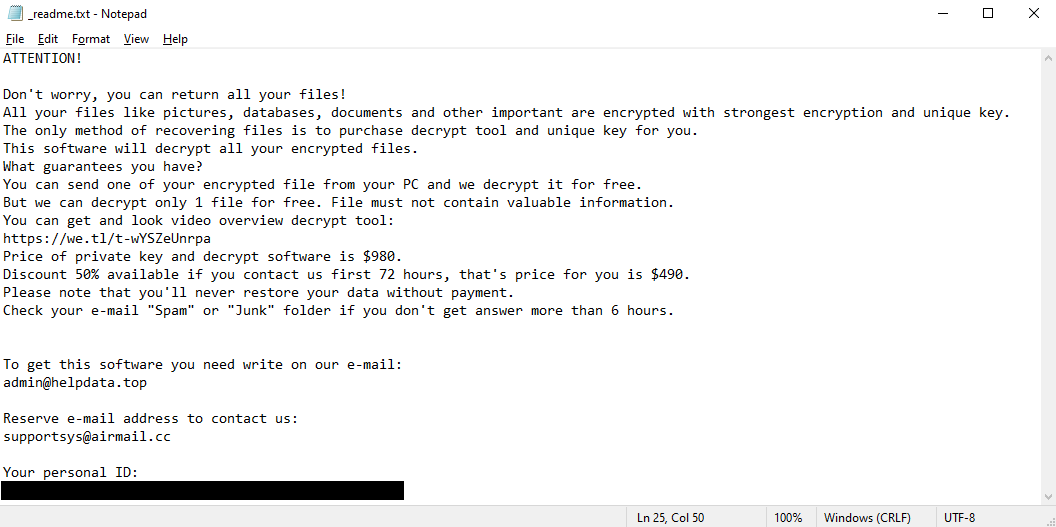
Zfdv in specific asks for $980, though the ransom note also states that victim who act quickly will get a 50% discount and will only have to pay $490. This, too, is typical for STOP/Djvu. Speaking of the ransom note, it is called “_readme.txt”, and is placed on the Desktop. For those that are interested in details, the image above contains the full text of the note – though once you’ve seen one STOP/Djvu ransom note, you’ve seen them all.
When Zfdv encrypts the files, is also changes the files’ extensions. Many ransomware programs do this, presumably to make it more evident to the victim that an attack has happened. The files Zfdv encrypts are given the extension .zfdv – hence the name.
The “good” thing about being infected with Zfdv is that STOP/Djvu is a well-known ransomware family that is relatively easy to get rid of. This article will explain how to remove Zfdv from your computer and how you can try to decrypt .zfdv files.
![LV's ransom note:
---=== Welcome. Again. ===---
[+] What's Happened? [+]
Your files have been encrypted and currently unavailable. You can check it. All files in your system have 0nzo8yk extension. By the way, everything is possible to recover (restore) but you should follow our instructions. Otherwise you can NEVER return your data.
[+] What are our guarantees? [+]
It's just a business and we care only about getting benefits. If we don't meet our obligations, nobody will deal with us. It doesn't hold our interest. So you can check the ability to restore your files. For this purpose you should visit our website where you can decrypt one file for free. That is our guarantee.
It doesn't metter for us whether you cooperate with us or not. But if you don't, you'll lose your time and data cause only we have the private key to decrypt your files. In practice - time is much more valuable than money.
[+] How to get access to our website? [+]
Use TOR browser:
1. Download and install TOR browser from this site: https://torproject.org/
2. Visit our website: http://4to43yp4mng2gdc3jgnep5bt7lkhqvjqiritbv4x2ebj3qun7wz4y2id.onion
When you visit our website, put the following data into the input form:
Key:
[REDACTED]
!!! DANGER !!!
DON'T try to change files by yourself, DON'T use any third party software or antivirus solutions to restore your data - it may entail the private key damage and as a result all your data loss!
!!! !!! !!!
ONE MORE TIME: It's in your best interests to get your files back. From our side we (the best specialists in this sphere) ready to make everything for restoring but please do not interfere.
!!! !!! !!](https://www.computips.org/wp-content/uploads/2022/06/how-to-remove-lv-ransomware.png)