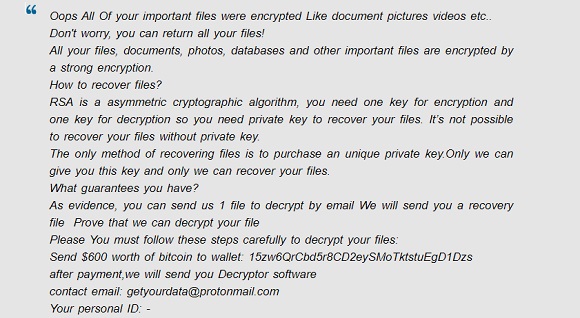
What is Sext ransomware?
Sext ransomware got the name ransomware because its main goal is to get money from users by fraud and blackmail.
Articles about ransomware – malware encrypting your personal files or stopping you from accessing your computer – and ways to remove it

Sext ransomware got the name ransomware because its main goal is to get money from users by fraud and blackmail.

Howareyou is a ransomware program. It encrypts victim`s data found on the device and manages access to them
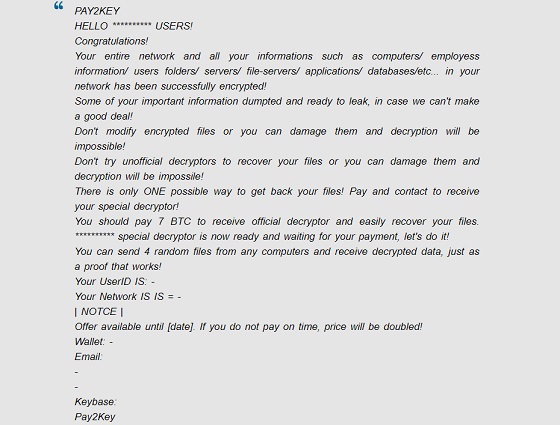
Pay2Key ransomware enters the system and blocks files to restrict access to them. The “.pay2key” extension is added to encrypted files to mark files that are not available for use or even opening. After encryption ends, the scammers create a ransom note. They add this note to the folders where the infected files are and to the desktop:

Uhofbgpgt is named ransomware because it extorts money from victims in exchange for the files it infects and restricts access.

This program is called a ransomware virus because it illegally locks files and blackmails by decrypting victims to extort money.

This malware is designed to encrypt files. DUSK 2 is called ransomware because it illegally encrypts files and then demands a ransom from users and demands payment for decryption. The extension “.DUSK” is added to all encrypted files, which indicates that they are not viewable. After the encryption process is complete, the virus creates a ransom note "README.txt" which it places on the screen and in the folders where there are encrypted files
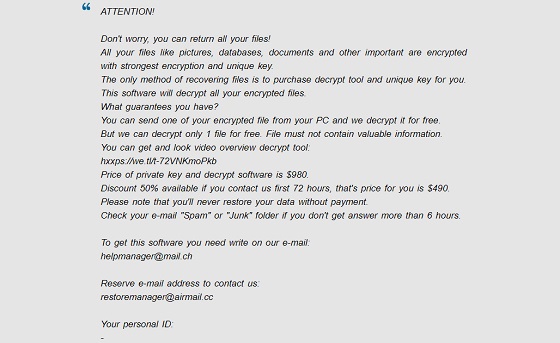
Agho is a malicious program from the Djvu family. It is designed to encrypt important files. During the encryption process, the extension “.agho” is added to all files to mark files that cannot be opened. After encryption is complete, virus sends a ransom note – “_readme.txt” to the folders with encrypted files and to the desktop:

Recoverydatas ransomware is a type of malicious application that acts by encrypting files in order to then blackmail victims by extorting money

This is a ransomware program. Ransomware is viruses that infect a device and then require payment to return the device to its original form.

Termit is a program that is named ransomware because of the method of infection. Virus encrypts files in order to later demand money for them. Termit renames files by adding the extension “.termit”. After the end of the encryption process, Termit ransomware creates a ransom note and sends it to the desktop and to each daddy with encrypted files