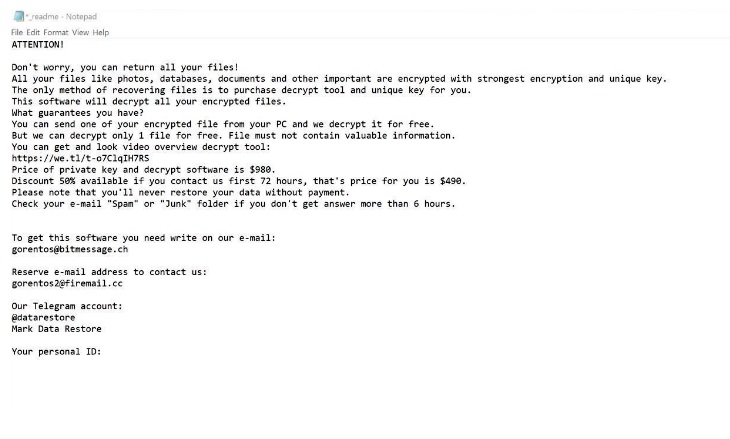
What Is LONDEC ransomware?
LONDEC ransomware is a virus that preys on Windows, including Windows 7, Windows 8, and Windows 10. LONDEC ransomware enters the computer without any warning and creates an infencial file that, when launched, starts scanning all drive letters on your computer for data files for encryption. When your files are finally encrypted, they will become inaccessible for use. Bringing users to panic, LONDEC ransomware will offer you help in decoding, making it clear that this is the only solution so that you can use your files again. For decryption you have to pay $ 490 to $ 980 in Bitcoins. Most users believe LONDEC ransomware, but this virus deceives money and continues to infect your system. The only thing you need to do to save your system from infection is to remove LONDEC ransomware.