![ZeRy ransom note:
HELLO!
As you can see all your files are encrypted
To get them back, you have to pay me 0.05 bitcoins
At this address: bc1qgfef9nlwffftl6m5qet95yxa0x7arah0h580gs
After you have made the payment, contact me at this email address: zery@tuta.io
with this topic: [REDACTED]
After payment confirmation, you will receive the keys and a tutorial to decrypt your files.
If you don't own bitcoin, you can buy it very easily here:
www.localbitcoins.com
www.paxful.com
www.coinmama.com
You can find a larger list here:
hxxps://bitcoin.org/en/exchanges
If you don't contact me or you won't make the payment in 5 days
I will assume that you do not want to recover your files
and as a result I will delete the keys generated for your PC.
This is the end of the note. Below you will find a guide explaining how to remove ZeRy ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-zery-ransomware.png)
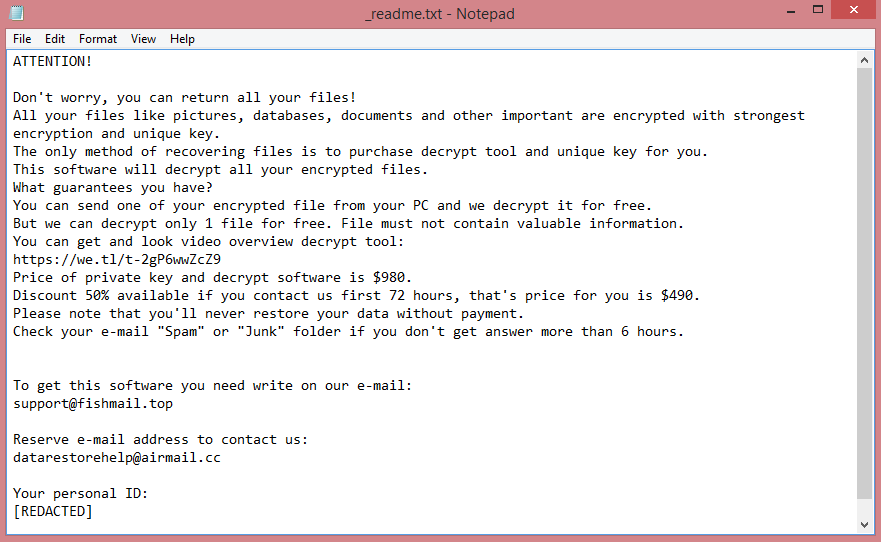
What is ZeRy ransomware?
ZeRy is a malicious program that falls under the ransomware category. This means that it encrypts the files on the target computer and then demands money for their decryption. Additionally, files affected by this ransomware program get renamed; specifically, they receive .ZeRy file extension. This is how the virus got its name.
ZeRy belongs to the Xorist ransomware family. Many ransomware viruses in this family have ransom notes written in Russian, but ZeRy is not one of them. Its ransom note, written in plain and understandable English, can be read on the image above.
The short version is, the hackers want 0.05 Bitcoin, which is approximately $830 at the time of writing. However, as cryptocurrencies are highly unstable, this may no longer be accurate by the time you’re reading this. They also threaten to delete the decryption keys if not contacted within 5 days after infection.
You should know, however, that contacting these criminals is a risky affair, and paying them is even riskier. You may become a target for future attacks, and they might not even decrypt your files. The guide below will explain what other options you have to remove ZeRy ransomware and decrypt .ZeRy files.
![RAMP ransom note:
Увага! Всі ваші файли зашифровані!
Щоб відновити свої файли та отримати до них доступ,
надішліть SMS з текстом [REDACTED] Користувачеві Telegram @WHITE_ROS4
У вас є 1 спроба ввести код. Якщо це
кількість буде перевищено, всі дані необоротно зіпсуються. Бувши
обережні при введенні коду!
Channels: @white_ros4bio | @vip_swatting |
привет от Killnet
Keygroup привет
This is the end of the note. Below you will find a guide explaining how to remove RAMP ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-ramp-ransomware.png)
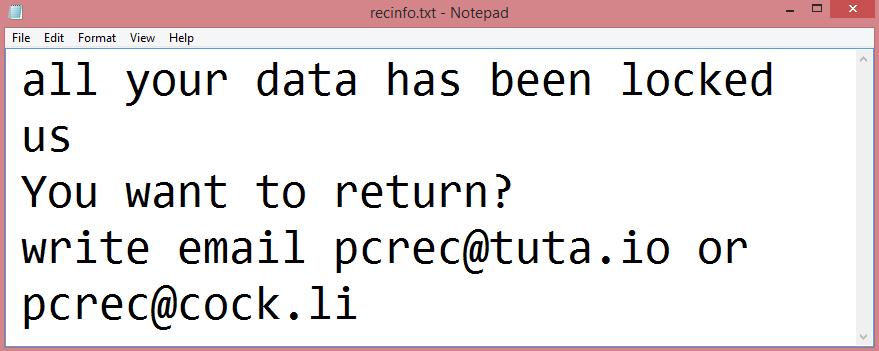
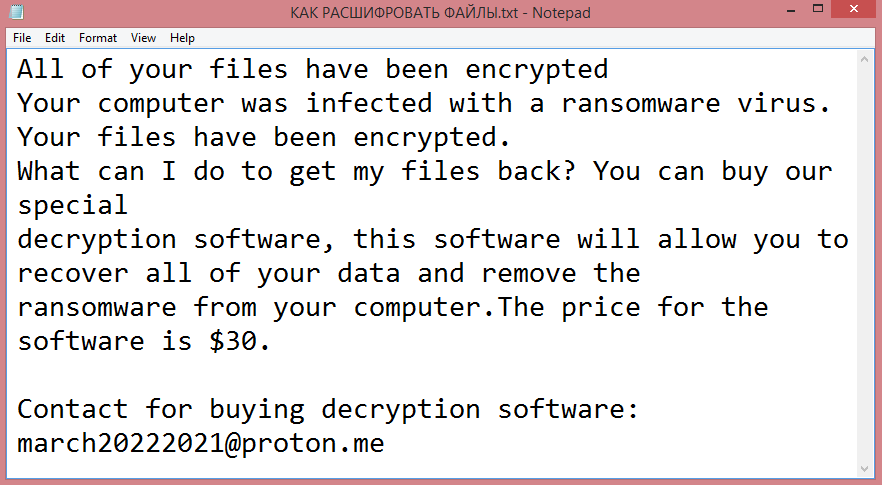
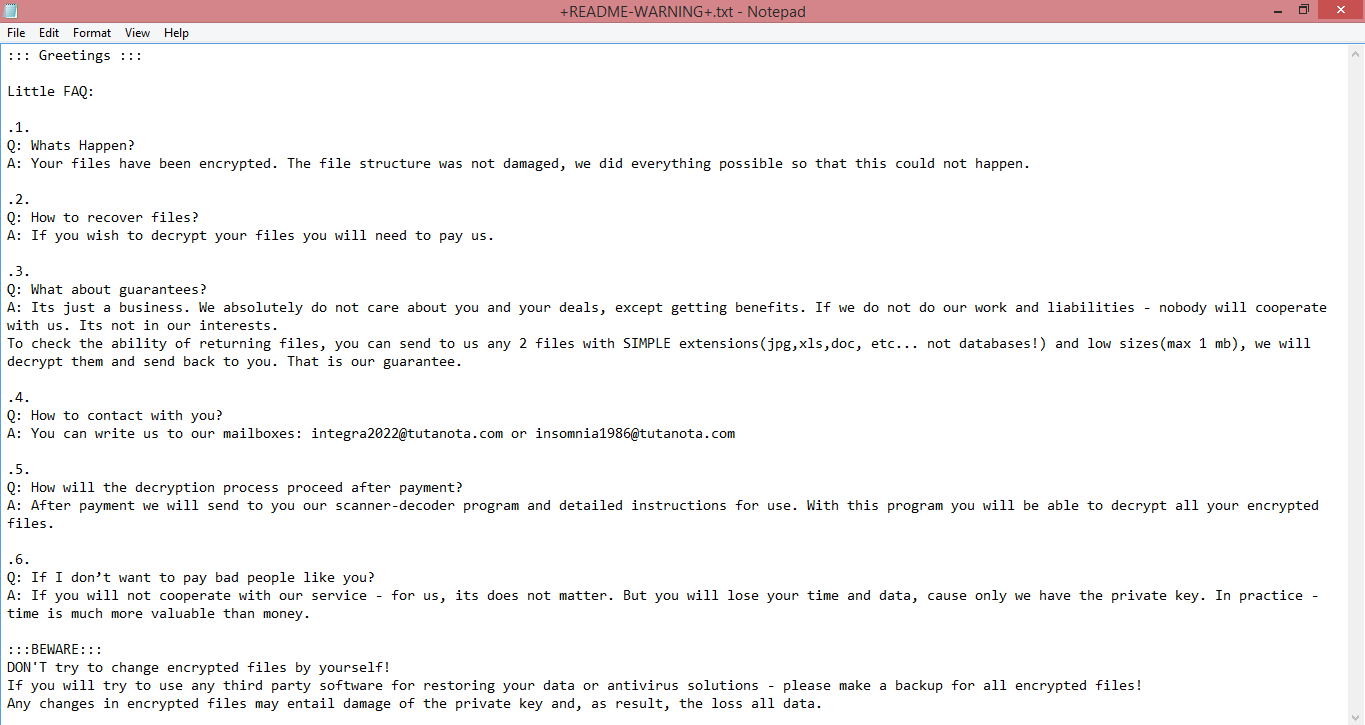
![Rar ransom note:
All your files have been encrypted. If you want to restore them, write us to the e-
mail:spystar1@onionmail.com
Write this ID in the title of your message [REDACTED]
You can also write us using this Telegram Username: @Rar_support
Do not rename encrypted files.
Do not try to decrypt your data using third-party software and sites. It may cause permanent data loss.
The decryption of your files with the help of third parties may cause increased prices (they add their
fee to our), or you can become a victim of a scam.
This is the end of the note. Below you will find a guide explaining how to remove Rar ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-rar-ransomware.png)
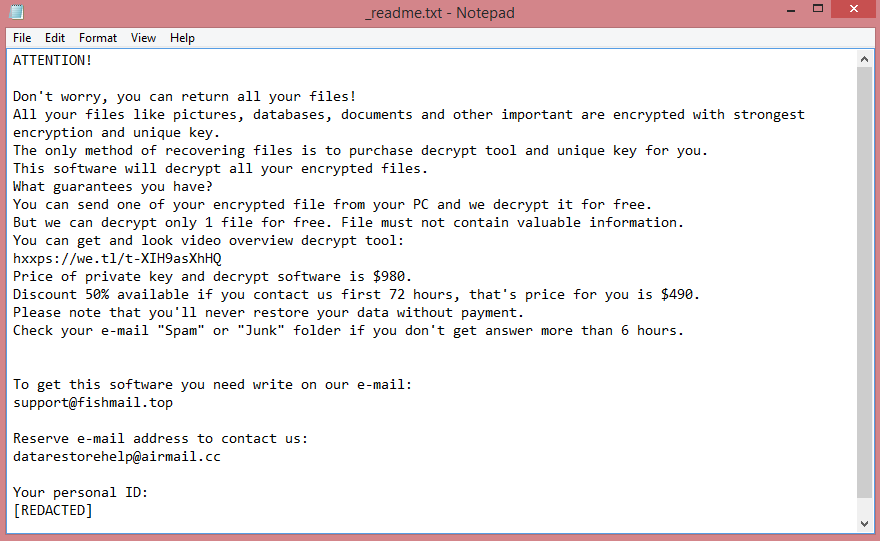
![Inlock ransom note:
¡¡¡TU EQUIPO HA SIDO CIFRADO!!!
Lo sentimos mucho, pero has sido objectivo de un ciberataque.
Todos tus datos personales han sido cifrados. Ponte encontacto conmigo para negociar el rescate.
Una vez me llegue el pago, te haré llegar la herramienta encargada de descifrar todos los ficheros.
Espero que no tengas nada de gran valor ;)
El siguiente código no lo pierdas o no podrás recuperar nunca más tus datos:
[REDACTED]
This is the end of the note. Below you fill find a guide explaining how to remove Inlock ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-inlock-ransomware.png)
![Dom ransom note:
!!! ALL YOUR FILES ARE ENCRYPTED !!!
All your files, documents, photos, databases and other important files are encrypted.
You are not able to decrypt it by yourself! The only method of recovering files is to purchase an unique
private key.
Only we can give you this key and only we can recover your files.
Do you really want to restore your files?
You can write us to our mailboxes: dekrypt666@onionmail.org
(in subject line please write your MachineID: [REDACTED] and LaunchID: [REDACTED])
Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price (they add their fee
to our) or you can become a victim of a scam.
This is the end of the note. Below you will find a guide explaining how to remove Dom ransomware.](https://www.computips.org/wp-content/uploads/2022/11/how-to-remove-dom-ransomware.png)