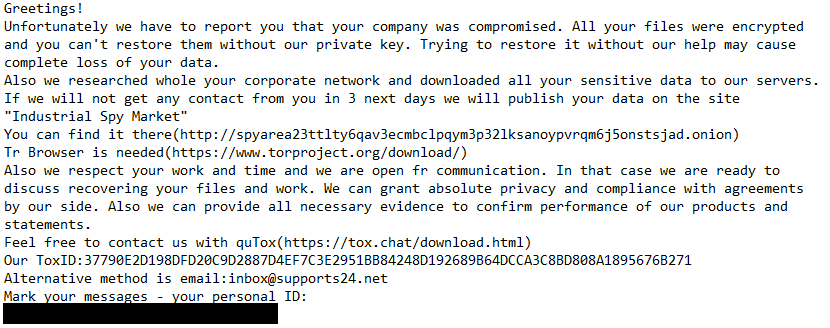
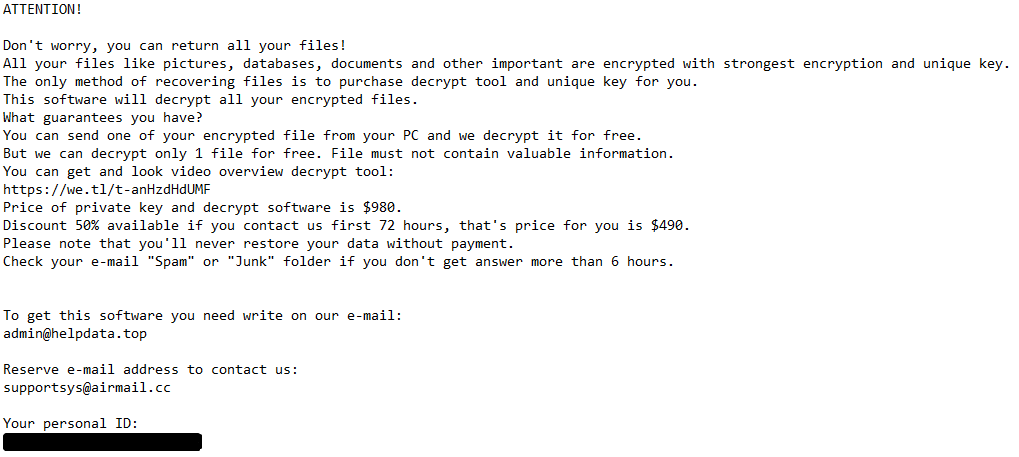
![LV's ransom note:
---=== Welcome. Again. ===---
[+] What's Happened? [+]
Your files have been encrypted and currently unavailable. You can check it. All files in your system have 0nzo8yk extension. By the way, everything is possible to recover (restore) but you should follow our instructions. Otherwise you can NEVER return your data.
[+] What are our guarantees? [+]
It's just a business and we care only about getting benefits. If we don't meet our obligations, nobody will deal with us. It doesn't hold our interest. So you can check the ability to restore your files. For this purpose you should visit our website where you can decrypt one file for free. That is our guarantee.
It doesn't metter for us whether you cooperate with us or not. But if you don't, you'll lose your time and data cause only we have the private key to decrypt your files. In practice - time is much more valuable than money.
[+] How to get access to our website? [+]
Use TOR browser:
1. Download and install TOR browser from this site: https://torproject.org/
2. Visit our website: http://4to43yp4mng2gdc3jgnep5bt7lkhqvjqiritbv4x2ebj3qun7wz4y2id.onion
When you visit our website, put the following data into the input form:
Key:
[REDACTED]
!!! DANGER !!!
DON'T try to change files by yourself, DON'T use any third party software or antivirus solutions to restore your data - it may entail the private key damage and as a result all your data loss!
!!! !!! !!!
ONE MORE TIME: It's in your best interests to get your files back. From our side we (the best specialists in this sphere) ready to make everything for restoring but please do not interfere.
!!! !!! !!](https://www.computips.org/wp-content/uploads/2022/06/how-to-remove-lv-ransomware.png)
What is LV ransomware
LV ransomware (also known as 0nzo8yk ransomware) is a modified version of another ransomware program, REvil. The ultimate goal of any ransomware virus is to generate money for the cybercriminals. This is done via ransom – LV (as well as every other ransomware program) encrypts the victim’s data and demands a payment to decrypt them.
LV’s ransom note is called “EDGEWATER-README.txt”, which you can read on the image above. One thing is absent from this note, and that is price. The price varies depending on the profile of the victim, so the hackers are using their Tor website to communicate this information (see example). This is important because it means that LV most likely focuses on a small number of valuable targets such as companies. This does not rule out the possibility of private individuals being targeted with LV – they could be targeting both.
Either way, this guide will show you how to remove LV ransomware from your computer, and will give you tips on how to decrypt .0nzo8yk files.
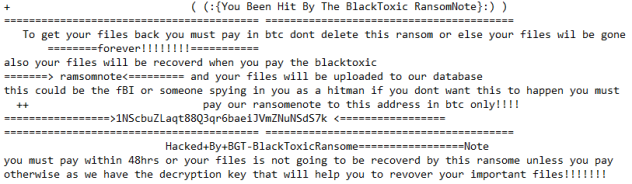
![Horsemagyar's ransom note:
::: Hello my dear friend :::
Unfortunately for you, a major IT security weakness left you open to attack, your files have been encrypted
If you want to restore them,write to our skype - HORSEMAGYAR DECRYPTION
Also you can write ICQ live chat which works 24/7 @HORSEMAGYAR
Install ICQ software on your PC https://icq.com/windows/ or on your mobile phone search in Appstore / Google market ICQ
Write to our ICQ @HORSEMAGYAR https://icq.im/HORSEMAGYAR
If we not reply in 6 hours you can write to our mail but use it only if previous methods not working - horsemagyar@onionmail.org
Attention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* We are always ready to cooperate and find the best way to solve your problem.
* The faster you write, the more favorable the conditions will be for you.
* Our company values its reputation. We give all guarantees of your files decryption,such as test decryption some of them
We respect your time and waiting for respond from your side
tell your MachineID: [REDACTED] and LaunchID: [REDACTED]
Sensitive data on your system was DOWNLOADED.
If you DON'T WANT your sensitive data to be PUBLISHED you have to act quickly.](https://www.computips.org/wp-content/uploads/2022/05/how-to-remove-horsemagyar-ransomware.png)