What is Gatz ransomware?
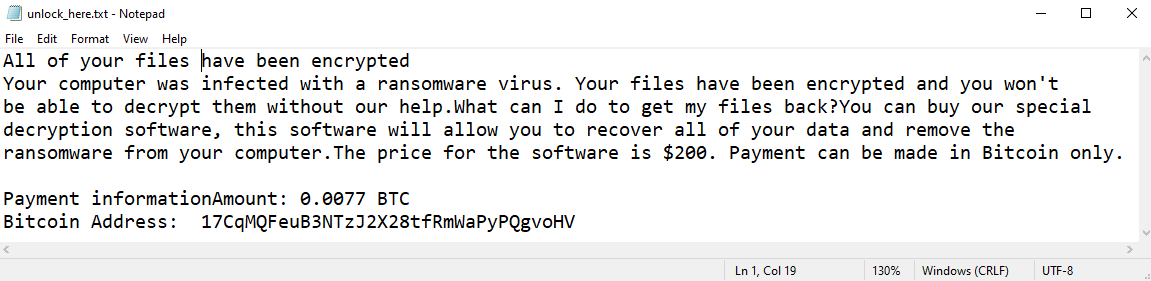
Gatz is the newest computer virus in the STOP/Djvu ransomware family. The virus, just like every other ransomware program, encrypts all files it can reach. After doing this, it proceeds to demand payment for the decryption of the files.
STOP/Djvu viruses are incredibly similar to one another, so there aren’t many ways to confirm that your computer has been infected by Gatz specifically. The only reliable method is to check the extension of the encrypted files – they should have .gatz file extension.
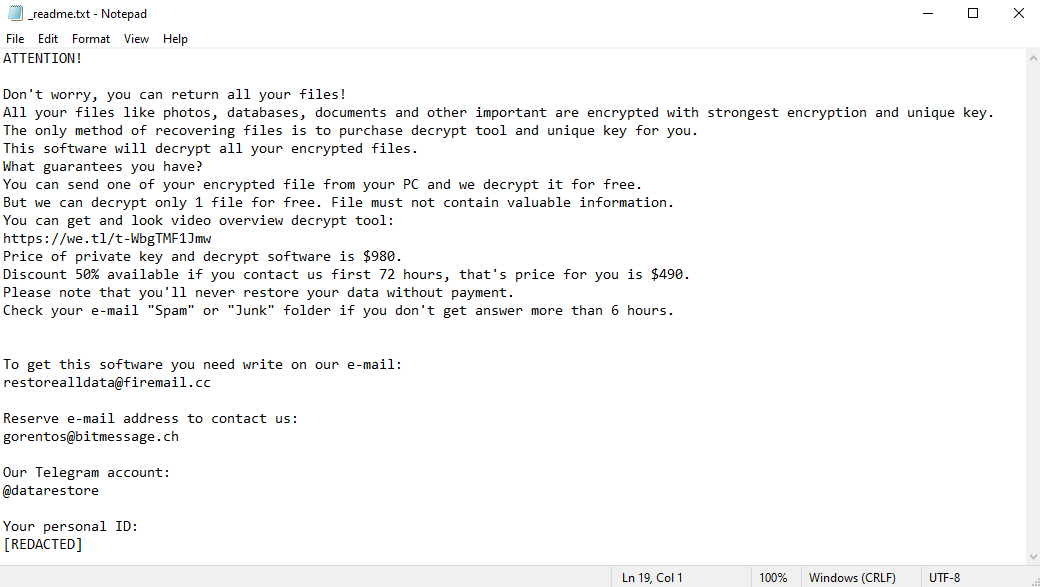
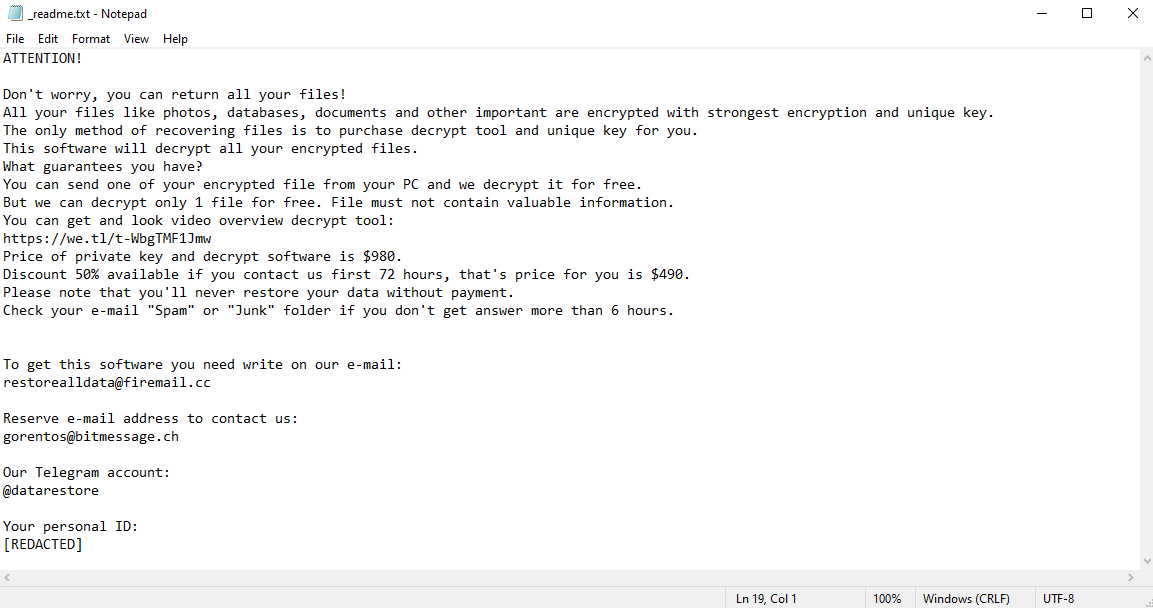
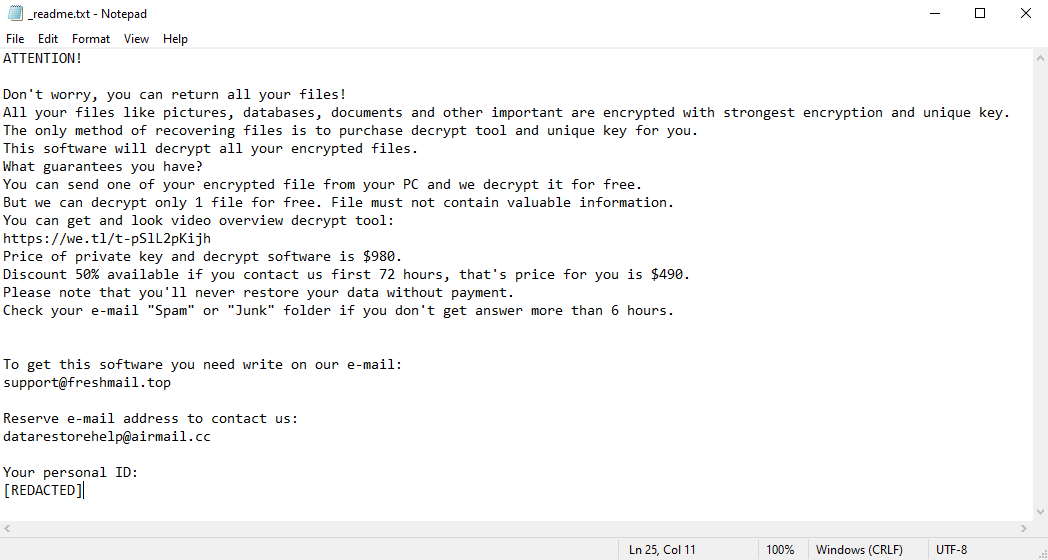
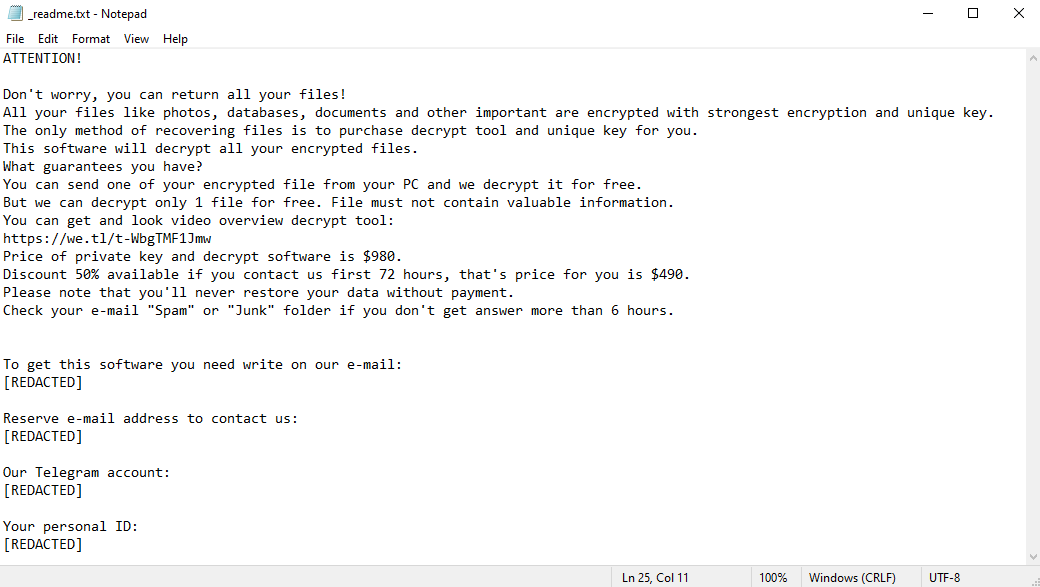
To communicate with its victims, the virus creates a file named “_readme.txt”. This file is a ransom note; it contains the hackers’ contact information and their demands. As you can read on the image above, the hackers order the victims to pay $980 to get their files back. To discourage hesitation, the hackers also provide a 50% “discount” to those who pay within 3 days of infection.
Of course, this is still a bad deal. And to make the matters worse, the hackers will often cut communications with the victim after getting paid, without decrypting any files. This is why you should consider alternate ways to remove Gatz ransomware and decrypt .gatz files; read the article below to learn more about them.